Dashboard
The dashboard is the default page displayed after you log into the ESET PROTECT Web Console for the first time. It displays pre-defined reports about your network. You can switch between dashboards using the tabs in the top menu bar. Each dashboard consists of several reports.
Dashboard manipulation
•Add—Click the plus ![]() symbol at the top of the dashboard header to add a new dashboard. Type a name for the new dashboard and click Add dashboard to confirm. A new blank dashboard is created.
symbol at the top of the dashboard header to add a new dashboard. Type a name for the new dashboard and click Add dashboard to confirm. A new blank dashboard is created.
•![]() Move—Click and drag the dashboard name to change its location relative to other dashboards.
Move—Click and drag the dashboard name to change its location relative to other dashboards.
•You can customize your dashboards by adding, modifying, resizing, moving and re-arranging reports.
•Select a dashboard, click the gear ![]() icon on the top (next to the refresh page
icon on the top (next to the refresh page ![]() icon) and select Set as default to use your dashboard as a default dashboard for all new Web Console users with access to Dashboards.
icon) and select Set as default to use your dashboard as a default dashboard for all new Web Console users with access to Dashboards.
•MSP users can click Select next to the MSP Customer to filter the dashboard view for the selected customer.
Click the ![]() gear icon next to the selected dashboard title to get the following options in the drop-down menu:
gear icon next to the selected dashboard title to get the following options in the drop-down menu:
|
Refresh the report templates in this dashboard. |
|
Remove the dashboard. |
|
Rename the dashboard. |
|
Create a copy of the dashboard with the same parameters in the user's home group. |
Change Layout |
Choose a new layout for this dashboard. The change will remove current templates from the dashboard. |
You cannot customize these default dashboards: Status Overview, Security Overview, ESET LiveGuard, ESET Inspect, ESET MDR, Incidents, ESET Vulnerability & Patch Management, ESET Cloud Office Security, Detections, ESET MDR Ultimate. |
The following dashboards come pre-configured in ESET PROTECT:
Status Overview
The Status Overview dashboard is the default screen you see when you log into ESET PROTECT (unless you set another dashboard as the default one). It displays general information about your network.
Computer status—A number of managed devices based on the last reported status (Error, Warning). In the tile, you can see the total number of devices and muted devices. You can click the tiles to open a filtered device list.
Incident status—A number of active incidents by severity: High severity, Medium severity. On a tile, you can click the![]() three dots button to:
three dots button to:
•![]() View all—Open Incidents page.
View all—Open Incidents page.
Top functional problems—The top functional problems on managed devices. You can click a problem and choose to:
•Alert—Proceed with remedial action (Update Application Modules, Retry Failed Encryption, Reboot, ...) depending on the functional problem.
•Search the Web—Open your search browser.
•View affected computers—Display the Computers page with filtered affected computers.
On a tile, you can click the![]() three dots button to:
three dots button to:
•![]() View all—Display all Functional problems in a new dialog window. You can click any problem and select an action to proceed.
View all—Display all Functional problems in a new dialog window. You can click any problem and select an action to proceed.
•View by count—Order the problems based on an amount.
•View by severity—Order the problems based on severity, with critical (red) ones at the top.
Most impactful active incidents—A list of the most impactful active incidents with the incident Name, the number of affected Computers and the current incident Status. On a tile, you can click the![]() three dots button to:
three dots button to:
•![]() View all—Open the Incidents page.
View all—Open the Incidents page.
Top vulnerable applications—A list of vulnerable applications sorted by vulnerability score with the Application name, the number of Affected computers, the number of Total vulnerabilities and the overall application risk score set in a percentage—Overall Impact. The visibility of vulnerabilities is affected by the selected static group and by filters: OS type, Muted vulnerabilities (the static group for the dashboard is your root group (usually All)).
On a tile, you can click the![]() three dots button to:
three dots button to:
•![]() View all—Open the Vulnerabilities page.
View all—Open the Vulnerabilities page.
•Show with muted vulnerabilities—Display the number with the muted vulnerabilities.
•Show without muted vulnerabilities—Display the number without the muted vulnerabilities.
•Apply to all widgets—Apply your selection to all widgets.
Computer connection status—A graph of last connections of managed devices—Online, 1 day, 1-7 days, > 7 days and Never. You can click anywhere in the graph to open the Computers page.
On a tile, you can click the![]() three dots button to:
three dots button to:
•![]() View all—Open the Computers page.
View all—Open the Computers page.
Computer management status—A graph with the number of:
•Computers with installed ESET Management Agent and an ESET Security application—Protected.
•Computers with installed ESET Management Agent but with no ESET Security application—Not protected.
•Computers that are known to ESET PROTECT but do not have ESET Management Agent installed—Unmanaged devices.
You can click anywhere in the graph to open the Computers page. On a tile, you can click the![]() three dots button to:
three dots button to:
•![]() View all—Open the Computers page.
View all—Open the Computers page.
Platform modules—The graph of total number of enabled eligible computers with specific protection module (ESET Security Application, ESET LiveGuard, ESET Full Disk Encryption, ESET Vulnerability & Patch Management, ESET Inspect). You can hover over the protection module to display detailed information about the layer.
The chart displays the ratio of current and outdated ESET component or ESET security application versions.
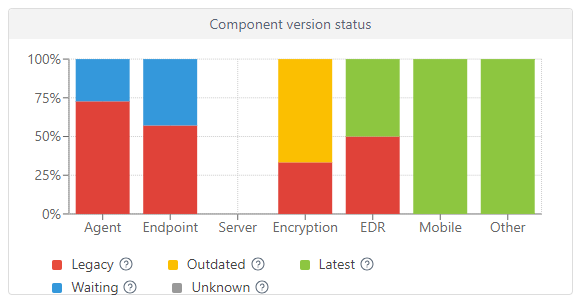
Click the yellow/red graph representing outdated components or applications and select Update installed ESET components to initiate an update. See also ESET End of Life policy for business applications and services.
•Red (Legacy)—A legacy version of the ESET component/application or an earlier version with a discovered security vulnerability that is no longer supported and is not in the ESET repository.
•Yellow (Outdated)—The installed version of the ESET component/application is outdated but still supported. Usually, two versions earlier than the latest version are in the yellow state unless they contain a recently discovered security vulnerability.
•Green (OK)—The latest version of the ESET component/application is installed or the installed version is the last version of the ESET component/application compatible with the used ESET PROTECT Web Console.
Earlier ESET component/application versions report OK (green) in the chart if there is no later compatible component/application version in the ESET repository for the specific operating system version or platform (x86, x64, ARM64). |
•Blue (Waiting)—The auto-updates are enabled and the latest version will install automatically. Read more details about the auto-updates:
If ESET components are not updating, you can update them manually by clicking the blue graph and selecting Update installed ESET components. Alternatively, you can use the Upgrade Agent Client Task to upgrade Agents and the Software Install Client Task to upgrade ESET security applications. |
•Gray (Unknown)—The ESET component/application version is not recognized (for example, shortly after a new ESET application installation).
On a tile, you can click the![]() three dots button to:
three dots button to:
•![]() Update ESET applications—Initate the update.
Update ESET applications—Initate the update.
RSS feed—Displays an RSS feed from WeLiveSecurity and the ESET Knowledgebase Portal. When you click the gear icon in the RSS feed, you can choose to Turn off feed autoplay, turn off individual feed source or Turn off RSS feed.
Detections
This dashboard provides you with useful statistics data on Detections. Click the gear ![]() icon on the top (next to the refresh page
icon on the top (next to the refresh page ![]() icon) and select Hide/Show Incidents to hide/show the dashboard.
icon) and select Hide/Show Incidents to hide/show the dashboard.
Detections tiles show the following information:
•Unresolved detections by severity—The total number of unresolved detections and unresolved detections by severity level—Informational, Warning or Critical.
•Detections by severity in last 7 days—A compound line chart with the number of detections by severity in the last seven days.
•Unresolved detections—The number of unresolved detections.
•Detections by detection method in last 7 days—The number of detections by its category in the last seven days.
•Top 10 computers with detections in last 7 days—The computer name, the number of detections by severity level (red—critical, yellow—warning and blue—informational) and the total number of detections.
•Top 10 users with detections in last 7 days—The user name, the number of detections by severity level (red—critical, yellow—warning and blue—informational) and the total number of detections.
Incidents
This dashboard provides you with useful statistics data on Incidents. Click the gear ![]() icon on the top (next to the refresh page
icon on the top (next to the refresh page ![]() icon) and select Hide/Show Incidents to hide/show the dashboard.
icon) and select Hide/Show Incidents to hide/show the dashboard.
Incident tiles show the following information:
•Active incidents—A number of active incidents by severity: All active incidents, High severity, Medium severity and Low severity.
•Number of created incidents over time—A line chart with the number of created incidents over time.
•Latest active incidents—A list of the latest created incidents with Creation time, Name of the incident, the number of impacted Computers, the number of Detections and the current Status of the incident.
•Top impacted computers—A list of the most impacted computers with the Computer name, the number of Incidents on the impacted computer, the Group where the computer is located, and the computer's Last seen time.
•Most impactful active incidents—A list of the most impactful active incidents with the incident's Name, the number of Affected computers and the current incident Status.
•Active incidents by status—A doughnut chart with the number of incidents in the Open and In progress status.
•Closed incident resolution—A doughnut chart with the number of closed incidents: True positive, False positive, Canceled.
On a tile, you can click the![]() three dots button to:
three dots button to:
•![]() View all—Go to the Incidents page.
View all—Go to the Incidents page.
•Widget time frame—Select the time frame to display: Last 7 days or Last 30 days (applicable only for Number of created incidents over time).
ESET LiveGuard
If you are using the ESET LiveGuard Advanced, you can find an overview of useful ESET LiveGuard Advanced reports here. Click the gear ![]() icon on the top (next to the refresh page
icon on the top (next to the refresh page ![]() icon) and select Hide/Show ESET LiveGuard to hide/show the dashboard.
icon) and select Hide/Show ESET LiveGuard to hide/show the dashboard.
ESET Vulnerability & Patch Management
If you are using ESET Vulnerability & Patch Management, this dashboard provides you with an overview of useful statistics data. Click the gear ![]() icon on the top (next to the refresh page
icon on the top (next to the refresh page ![]() icon) and select Hide/Show ESET Vulnerability & Patch Management to hide/show the dashboard.
icon) and select Hide/Show ESET Vulnerability & Patch Management to hide/show the dashboard.
ESET Vulnerability & Patch Management tiles show the following information:
•Number of vulnerabilities—A count of all vulnerabilities with a High-risk score or Medium-risk score.
•Number of vulnerabilities over time—A timeline graph displaying vulnerabilities with a risk score—High risk or Medium risk.
•Computers scanned for vulnerabilities—A doughnut chart with the number of computers scanned for vulnerabilities in the Last 24 hours, Last 1 - 3 days, 4 days and more and Never.
•Top vulnerable computers—A list of vulnerable computers with the Device name, Device type, the number of High-risk vulnerabilities, Medium-risk vulnerabilities and Total vulnerabilities.
•Top vulnerable computers by OS vulnerabilities—A list of computers with a vulnerable OS with the Device name, OS name, the number of High-risk OS vulnerabilities, Medium-risk OS vulnerabilities and Total OS vulnerabilities.
•Top vulnerable applications—A list of vulnerable applications sorted by vulnerability score with the Application name, the number of Affected computers, the number of Total vulnerabilities and the overall application risk score set in a percentage—Overall Impact. The visibility of vulnerabilities is affected by the selected static group and by filters: OS type, Muted vulnerabilities (the static group for the dashboard is your root group (usually All)).
•Top outdated applications with available patches—A list of outdated applications with available patches, including the Application name and Affected devices.
On a tile, you can click the![]() three dots button to:
three dots button to:
•![]() View all—Go to the Vulnerabilities or Patch Management page.
View all—Go to the Vulnerabilities or Patch Management page.
•![]() Refresh—Refresh the tile.
Refresh—Refresh the tile.
•Show with muted vulnerabilities—Display the number with muted vulnerabilities.
•Show without muted vulnerabilities—Display the number without muted vulnerabilities.
•Apply to all widgets—Apply your selection to all widgets.
•Show with Linux vulnerabilities—Display with Linux vulnerabilities.
•Show without Linux vulnerabilities—Hide Linux vulnerabilities.
•Show by total count—Order the items in the tile by total count.
•Show by severity—Order the items in the tile by severity.
ESET Inspect
If you are using ESET Inspect, this dashboard provides an overview of substantial ESET Inspect statistics data. Click a tile to open the ESET Inspect console and go from there. Click the gear ![]() icon on the top (next to the refresh page
icon on the top (next to the refresh page ![]() icon) and select Hide/Show ESET Inspect to hide/show the dashboard.
icon) and select Hide/Show ESET Inspect to hide/show the dashboard.
ESET Inspect tiles show the following information:
•Unresolved detections by severity—The total number of unresolved detections and unresolved detections by severity level—Informational, Warning or Critical.
•Detections by severity in last 7 days—A compound line chart with the number of detections by severity in the last seven days.
•Top 10 computers with detections in last 7 days—The computer name, the number of computers by detection severity level (red—critical, yellow—warning and blue—informational) and the total number of detections.
•Computers by detection severity—A doughnut chart with the number of computers by detection severity level—Critical, Warning and Informational.
•Incidents—The number of incidents (created in ESET Inspect) by status (Open, In-Progress, On-Hold, Resolved, Closed and Invalid). Click a number next to an incident status to see more details in ESET Inspect. When an ESET Service Representative edits the incident in ESET Inspect, you can see the incident tagged as Investigated by ESET.
ESET Cloud Office Security
If you use ESET Cloud Office Security, this dashboard provides an overview of substantial ESET Cloud Office Security statistics data. Click a tile to open the ESET Cloud Office Security console and go from there. Click the gear ![]() icon on the top (next to the refresh page
icon on the top (next to the refresh page ![]() icon) and select Hide/Show ESET Cloud Office Security to hide/show the dashboard.
icon) and select Hide/Show ESET Cloud Office Security to hide/show the dashboard.
ESET Cloud Office Security tiles include the following information:
•Protected users—The number of protected users
•License usage—The number of used and unused subscriptions
•Protected SharePoint sites—The number of protected SharePoint sites
•Protected Teams groups—The number of protected Teams groups
•Top 10 users with detections in the last 30 days—The name and email with the number of email and file detections for the top 10 users
•Detections in the last 30 days—A histogram chart with the number of detections in the specific services (Teams, SharePoint, Email and Drive) in the last 30 days; click any service in the histogram chart to open the Detections page in ESET Cloud Office Security
•Quarantined objects—The number of quarantined objects in the specific services in the last 7 and 30 days; click any service row to go to the Quarantine page in ESET Cloud Office Security
Computers
This dashboard provides an overview of client machines, including their protection status, operating systems and update status.
Antivirus detections
Here, you can see reports from the antivirus module of client security applications, including active detections, detections in the last 7/30 days, and so on.
Firewall detections
Firewall events of the connected clients are arranged according to their severity, time of reporting, etc.
ESET applications
This dashboard allows you to view information about installed ESET applications.
Cloud-based protection
This dashboard gives you an overview of cloud-based protection reports (ESET LiveGrid® and if you have the eligible subscription, also ESET LiveGuard Advanced).
ESET MDR
ESET Managed Detection and Response (MDR) service provides 24/7 threat monitoring, detection and incident response, combining AI with human expertise to protect your business from cyber threats. ESET MDR prevents breaches and ransomware attacks. The service identifies malicious activities and creates incidents—a set of alarms and detections. If the attack pattern is confirmed, the service will stop its escalation and block further access to the customer’s environment from unauthorized threat actors. ESET MDR provides an immediate view of incidents, countermeasures, and monitor activities. The service sends critical notifications, weekly and monthly, to the login email address (ESET MDR report).
ESET MDR provides an overview of incidents and detections from ESET Inspect. To use ESET MDR, you need an ESET Inspect subscription and the ESET PROTECT MDR tier.
ESET MDR availability ESET MDR is only available in selected service-enabled markets. |
The ESET MDR service covers all the managed devices running ESET Inspect.
You need the following permission set to view ESET MDR in the Dashboard: •Access to ESET Inspect—Read You can find data in tiles based on your customized Permission Sets in ESET Inspect and ESET PROTECT. |
ESET MDR tiles provide the following information:
•Incidents—The number of incidents by severity level in the last day(s)—Total, High, Medium and Low.
•Top incidents awaiting user input—A list of top incidents waiting for user input in the last day(s)—Incident name, Author, Creation date, Impacted computers and Assigned to.
•Incident statistics—The number of the Total incidents created, Detections related to incidents and All detections in the last day(s).
•Closed incident resolution—A doughnut chart showing the number of closed incidents categorized by their resolution in the last day(s)—True positive and False positive.
•Top impacted computers—A list of the highest number of impacted computers by their severity level in the last day(s)—Computer name, Incidents (severity level—Informational, Warning or Critical), Group name and Last seen.
•Response actions—A doughnut chart with the number of response actions to an incident in the last day(s)—Isolate, Kill process, Clean and block, Block executable.
•Active incidents by status—A doughnut chart with the number of active incidents by their status in the last day(s)—Open, In progress and Waiting for input.
•Incident response management—A doughnut chart displaying the ESET MDR status on the computers:
▪Automatic response—ESET MDR fully protects computers with automatic incident response enabled. ESET MDR, ESET Inspect and the endpoint security application are active, with the ESET Inspect Connector correctly deployed on the computers.
▪Custom response—Some automatic response actions are allowed, while others are suppressed based on your settings. ESET MDR, ESET Inspect and the endpoint security application are active, but only the allowed action will be triggered automatically.
▪Manual response—You manage incident response for computers independently. ESET MDR, ESET Inspect and the endpoint security application are active, but computers have been selected as critical assets, and all automatic response actions have been suppressed for them.
▪Not monitored—Computers are not monitored or integrated with ESET MDR. Although ESET MDR and the endpoint security application are active, the ESET Inspect Connector is missing on the computers, making them invisible to ESET MDR and ESET Inspect.
•ESET MDR protection—A doughnut chart displaying the ESET MDR enablement status—Enabled (computers protected by ESET MDR), Enablement in progress, Removal in progress (ESET MDR is currently being removed from computers), Not yet enabled (computers with the endpoint security application installed and ready for ESET MDR enablement).
•Suppressed remediation actions—The list of suppressed remediation actions displaying the Task name, number of Computers and Type of the remediation task.
•Incidents in time—A line chart with the number of incidents found in the last day(s) by severity level—High, Medium and Low.
•Top MITTRE ATT&CK techniques—A horizontal bar chart with the top MITTRE ATT&CK techniques in the last day(s).
The following information is related to the activation of the Open XDR Data. |
•Events in time—A line chart with the number of events found in the last day(s).
•Indicators in time—A line chart with the number of indicators found in the last day(s).
•Number of events by source—A doughnut chart show with a number of sources: EDR, Non-EDR.
•Number of indicators by source—A doughnut chart show with a number of sources: EDR, Non-EDR.
On a tile, you can click the![]() three dots button to:
three dots button to:
•![]() View all—Get into the Incidents page, the ESET Inspect Web Console (Top impacted computers tile), or the Tasks page (Suppressed remediation actions tile). You will be redirected to the specific section with the set filter.
View all—Get into the Incidents page, the ESET Inspect Web Console (Top impacted computers tile), or the Tasks page (Suppressed remediation actions tile). You will be redirected to the specific section with the set filter.
•![]() Refresh—Refresh the tile.
Refresh—Refresh the tile.
•Widget time frame—Click to view data in the tile for the Last day, Last 7 days or Last 30 days. Click Apply to all widgets to apply your selection to all tiles.
When no incident is detected, ESET MDR tiles provide the following information:
The following information is related to the activation of the Open XDR Data. |
•Events in time—A line chart with the number of events found in the last day(s).
•Indicators in time—A line chart with the number of indicators found in the last day(s).
•Number of events by source—A doughnut chart show with a number of sources: EDR, Non-EDR.
•Number of indicators by source—A doughnut chart show with a number of sources: EDR, Non-EDR.
•Incident response management—A doughnut chart displaying the ESET MDR status on the computers:
▪Automatic response—ESET MDR fully protects computers with automatic incident response enabled. ESET MDR, ESET Inspect and the endpoint security application are active, with the ESET Inspect Connector correctly deployed on the computers.
▪Custom response—Some automatic response actions are allowed, while others are suppressed based on your settings. ESET MDR, ESET Inspect and the endpoint security application are active, but only the allowed action will be triggered automatically.
▪Manual response—You manage incident response for computers independently. ESET MDR, ESET Inspect and the endpoint security application are active, but computers have been selected as critical assets, and all automatic response actions have been suppressed for them.
▪Not monitored—Computers are not monitored or integrated with ESET MDR. Although ESET MDR and the endpoint security application are active, the ESET Inspect Connector is missing on the computers, making them invisible to ESET MDR and ESET Inspect.
•ESET MDR protection—A doughnut chart displaying the ESET MDR enablement status—Enabled (computers protected by ESET MDR), Enablement in progress, Removal in progress (ESET MDR is currently being removed from computers), Not yet enabled (computers with the endpoint security application installed and ready for ESET MDR enablement).
See also the ESET MDR report. |
ESET MDR Ultimate
ESET MDR Ultimate is displayed only to users with the ESET MDR Ultimate tier. |
ESET MDR Ultimate is an end-to-end solution built around an XDR-enabling solution—ESET Inspect. It helps you to reach the full benefits of Endpoint Detection & Response. It covers all related areas, including alert triage and investigation, file analysis, incident response, digital forensics, threat monitoring and proactive periodic threat hunting.
ESET MDR Ultimate tiles show the following information:
•Active incidents—The number of active incidents—Total and Waiting for your action.
•Closed incident resolution—A doughnut chart showing the number of closed incidents categorized by their resolution in the last day(s)—True positive, False positive and Suspicious.
•Incident statistics—The number of the Total incidents created, Detections related to incidents and All detections in the last day(s).
•ESET MDR Ultimate protection—A doughnut chart displaying the ESET Detection and Response enablement status: Enabled (computers protected by ESET MDR Ultimate), Enablement in progress, Removal in progress (ESET MDR Ultimate is currently being removed from computers) and Not yet enabled (computers with the endpoint security application installed and ready for ESET MDR Ultimate enablement).
•Top impacted computers—A list of the highest number of impacted computers by their severity level in the last day(s)—Computer name, Incidents (severity level—Informational, Warning or Critical), Group name and Last seen.
•Response actions—A doughnut chart with the number of response actions to an incident in the last day(s)—Isolate, Kill process, Clean and block, Block executable.
•Incidents in time—A line chart with the number of incidents found in the last day(s) by severity level: High, Medium and Low.
On a tile, you can click the![]() three dots button to:
three dots button to:
•![]() View all—Get into the Incidents page or the ESET Inspect Web Console (Top impacted computers tile).
View all—Get into the Incidents page or the ESET Inspect Web Console (Top impacted computers tile).
•![]() Refresh—Refresh the tile.
Refresh—Refresh the tile.
•Widget time frame—Click to view data in the tile for the Last day, Last 7 days or Last 30 days. Click Apply to all widgets to apply your selection to all tiles.
Actions in a dashboard report
|
Click to view a report in fullscreen mode. |
|
Refresh the report template. |
|
Click Download to generate and download the report. You can choose from .pdf or .csv. CSV is suitable only for table data and uses ; (semicolon) as a delimiter. If you download a CSV report and see numbers in a column where you expect text, we recommend downloading a PDF report to see the text values. |
|
Change the report template for another from the template list. |
|
Edit an existing report template. The same settings and options used for creating a new report template apply. |
|
Set up custom refresh intervals for the template. |
|
Schedule a report - you can modify the schedule trigger, throttling and report delivery. You can find all scheduled reports in the Scheduled reports tab. |
|
Remove the report template from the dashboard. |
|
Rename the report template. |
This Cell |
Select a new layout for this dashboard. The change will remove current templates from the dashboard. |
Permissions for Dashboard
A user must have the appropriate permission to work with Dashboards. Users can only access report templates where they have access rights. If a user has no rights assigned for Reports and Dashboard, they will find no data in the Dashboard section. An administrator can access all data by default.
•Read—User can list report templates and their categories, generate reports based on report templates and read their dashboard •Use—User can modify their dashboard with available report templates •Write—Create/modify/remove templates and their categories All default templates are located in the All group. |