Incidents
Incidents allow us to correlate indicators into incidents, improving threat investigations. Incidents are created automatically from indicators, which significantly reduces alert triage time.
Filtering the view
There are different ways to filter your view:
•Click the Tags selector (arrow icon) and choose a tag(s) to activate the filter on the listed incidents. Results are highlighted in blue and show incidents with the selected tags.
•Click an Incident severity— High,
Medium or
Low. You can combine these icons by turning them on or off.
•Incident status— Open,
In progress,
![]() Waiting for input or
Waiting for input or Closed
•Click Add Filter and select incident types from the drop-down menu.
oAssignee—type the assingee name.
oAuthor—select from the drop-down menu: ESET, ESET Service or the username.
oClose reason—select from the drop-down menu: All, False positive, Suspicious, True positive.
oCreation time—select from the drop-down menu: ≤ Today, ≤ 24h ago, ≤ 3 days ago, ≤ 7 days ago, ≤ 14 days ago, ≤ 30 days ago, ≤ 90 days ago or ≤ 180 days ago.
oLast update—select from the drop-down menu: ≤ Today, ≤ 24h ago, ≤ 3 days ago, ≤ 7 days ago, ≤ 14 days ago, ≤ 30 days ago, ≤ 90 days ago or ≤ 180 days ago.
oName—type the incident name.
oNumber of computers—type the number of selected computers.
oNumber of indicators—type the number of selected indicators.
oNumber of users—type the number of selected users.
Filters and layout customization
You can customize the current Web Console screen view:
•Manage the side panel and main table.
•Add filters and filter presets. You can use tags for filtering the displayed items.
If you cannot find a specific incident in the list and know it is in your ESET PROTECT infrastructure, ensure that all filters are turned off and permission sets are assigned to your user account. |
The permissions you configure are applied to the parent company of the static group you selected in the Static Groups step. |
|
|
|
Open the ESET Inspect Web Console Incidents section. ESET Inspect is only available when you have ESET Inspect subscription and ESET Inspect connected to ESET PROTECT. A Web Console user requires Read permission or higher for Access to ESET Inspect. |
|
Refresh the page. |
Incident details
Select any incident(s), click the Actions button and click the three dots ![]() button to:
button to:
•View Details—to display an overview of the incident.
Overview—provides the following information:
oIncident details are displayed in the main section.
oCompany impact—the number of affected Computers, Executables and Processes. Click the number to go to the related specific page.
Executables and Processes are available only for customers with EDR tier with active ESET Inspect subscription. You will be redirected to the cloud ESET Inspect console to see the lists. |
oComments—you can Add comment for the incident. Click View all comments to display all created comments. You can Edit comment, Pin comment or Delete comment.
oDescription—incident explanation.
oMITTRE ATT&CK® techniques—available MITTRE ATT&CK techniques for the selected incident.
oRecommended steps—steps to initiate the incident response process.
Graph—view the incident graph structure made of indicators in the compound or hierarchical layout. The graph provides a control panel with buttons for quick orientation—zoom in/zoom out bar, Fit to screen, Reset view and info tooltip with Shortcuts.
The graph consists of nodes. In the graph, you can click any white node to view detailed information in the side panel. You cannot view details of the gray nodes.
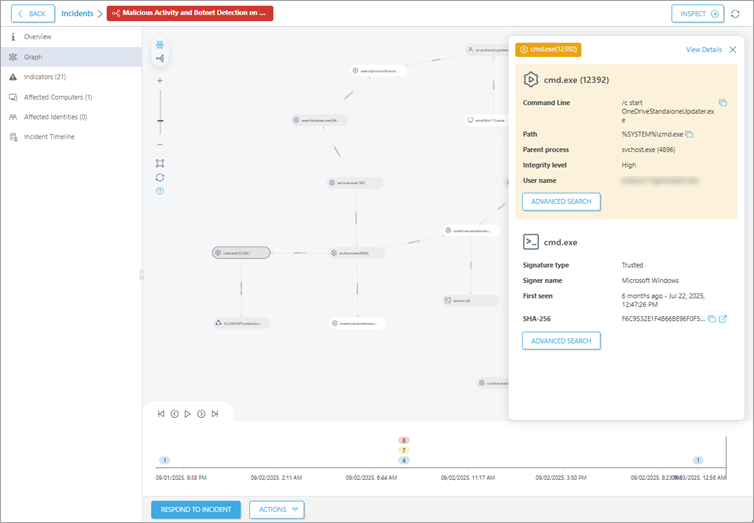
An arrow between nodes represents the relationship between different types of nodes, for example:
oUser → LOGGED IN → Computer
oUser → EXECUTES → Process
oParent process → SUB-PROCESS → Child process
You can find the incident graph timeline with the timeline control panel to rewind the state of the graph to the beginning, move forward or play the selected time period of the graph.
You can select groups of indicators based on their severity. When you click the group of indicators, a subgraph is highlighted. Subgraph consists only of the selected severity indicators group.
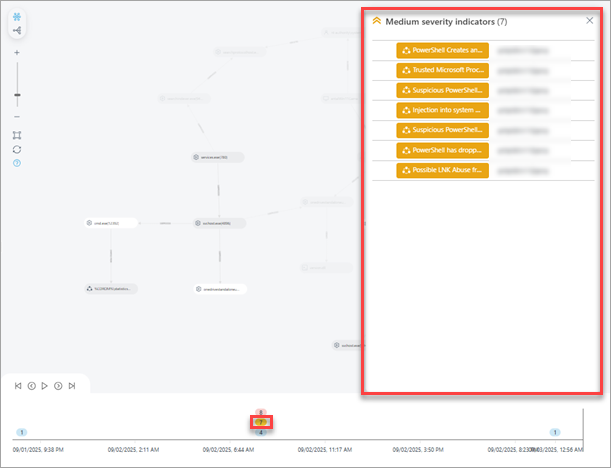
Indicators—list of indicators. Click an indicator to view details. Optionally, you can view details in a new tab, click ![]() > View Details in New Tab.
> View Details in New Tab.
You can view a process tree with process and indicator nodes:

Indicator details for indicators and processes are available for incidents created after the ESET PROTECT 6.4 release update (August 1, 2025). If you have incidents created before the ESET PROTECT 6.4 release update, you will be redirected to the cloud ESET Inspect console to see more details. |
The process tree allows users to navigate through indicator. You can click a process node (a rounded node) or a indicator node (a rectangle node) in the process tree to display details based on data availability:
Affected Computers—list of affected computers.
Affected Identities—list of affected users.
Incident Timeline—timeline with a brief history of incidents, from the triggering event until closing the incident.
In every section (except for Graph), you can click:
•the Inspect button to redirect into ESET Inspect and investigate the incident in the incident graph.
•the refresh button ![]() to refresh the page.
to refresh the page.
Click the Respond to incident button to select the affected objects and define their response actions. Select a response action (Isolate, Log out user, Reboot, Scan & Clean) and click Confirm.
oComputers > Continue > select the response action (Isolate, Log out user, Reboot, Scan & Clean) > Confirm.
oProcesses > Continue > select the response action (Kill Process) > Confirm.
oExecutables > Continue > select the response action (Block, Block & Clean) > Confirm.
•Change Status & Assignee—click to select from the drop-down menu.
oStatus—select the incident's current status from the drop-down menu: Open, In progress, Waiting for input or Closed. When you select Closed, additionally select the reason for closing the incident (True positive, Suspicious, False positive or invalid) and optionally write a comment.
oAssignee—when you selected Open or In progress status, select the available user from the drop-down menu.
Click Save.
•Tags—click to select tags from the drop-down menu and click Apply. Or you can type a new keyword and press Enter to create a new tag.