Activate ESET PROTECT Platform modules
ESET PROTECT Hub offers security solutions designed to address various cybersecurity aspects. The Dashboard includes the ESET PROTECT Platform tile where you can activate ESET PROTECT Platform modules.
Only a superuser can request, activate or deactivate customer's ESET PROTECT Platform modules. |
You can activate a module after purchasing the protection tier that includes it.
•If you have purchased a protection tier, click the Enter activation key button. Type the activation key and click the Add subscription button.
•If you have not purchased a protection tier, click the Get module button next to the desired module. The window with subscriptions that include your module will display. To purchase the protection tier, click the Choose customer and order button. You will be redirected to Subscriptions. See Add a subscription.
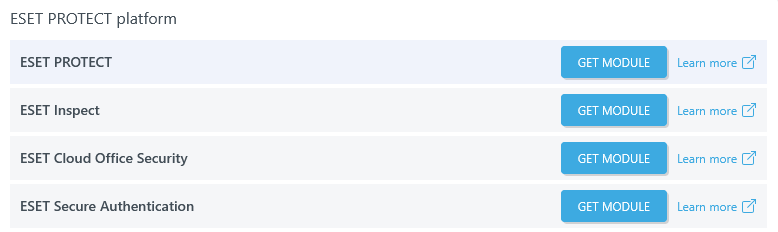
ESET PROTECT Platform modules
ESET PROTECT allows you to manage ESET solutions on workstations and servers in a networked environment with up to 50,000 devices from one central location.
Protect assets not managed by ESET PROTECT Click Help > Download installer in the top bar to deploy and set up your ESET business solutions on assets not managed by ESET PROTECT. |
Transferring an ESET PROTECT module under a different account may impact your configuration. Subscription transfers may result in data loss. Before proceeding, review the implications and follow the best practices in the Cloud-to-Cloud Migration guide. |
ESET Inspect identifies anomalous behavior and breaches with Extended Detection and Response (XDR), providing advanced threat hunting, risk assessment, incident response, investigation and remediation capabilities.
ESET Cloud Office Security is a standalone solution that handles security in your Microsoft 365 or Google Workspace cloud environments, mailboxes or cloud storage.
ESET Secure Authentication is a cloud-based solution offering the Two-Factor Authentication (2FA) for various applications. It delivers the second factor through multiple methods, including mobile phone applications, hard tokens and FIDO keys, enhancing and securing the standard user authentication process.
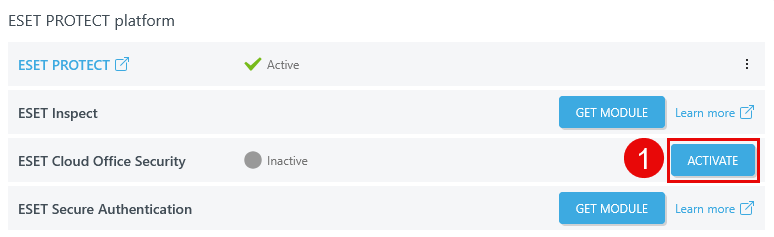
Activate a module
1.Click the Activate button. The Activate module wizard will display.
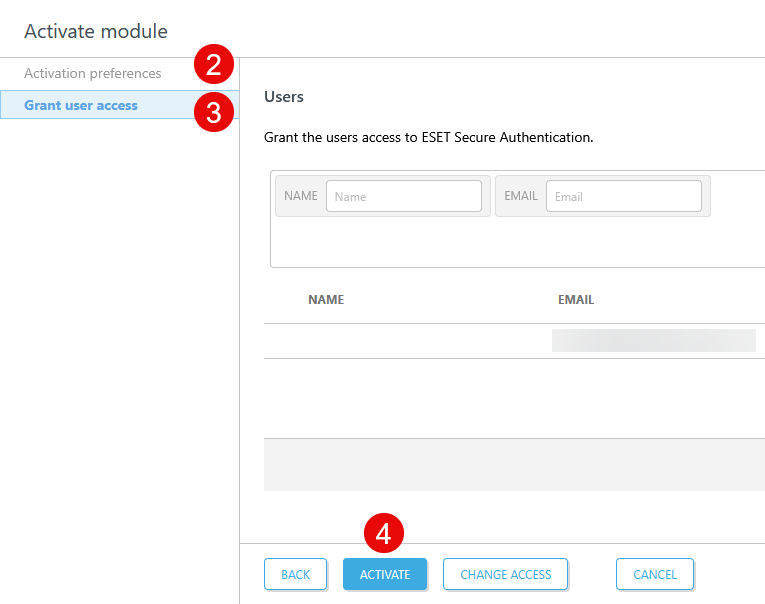
2.In the Activation preferences tab, select the Data center location and the Language. Click Next.
3.In the Grant user access tab, you can grant users access to the module. You can select a custom access for each user. Click the Change access button at the bottom and select Grant all Access to grant access to all users or select Grant all No access to revoke access from all users.
4.Click the Activate button. It can take a few minutes to activate the module.
When the module is activated, click the three dots icon next to the module name to:
•Show details—Display the module's activation status and description.
•Learn more—See the module's Online Help.
•Remove—Remove a module.
Remove a module
1.Click the three dots icon > Remove.
2.Type your password and click the Authenticate button. When you remove a module, your module will be suspended, and its data will be permanently removed after 30 days. After its removal, you can activate the module again by clicking the Activate button.