Resolving cloning questions
Every time a machine connects to the ESET PROTECT, an entry is created based on two fingerprints:
•an ESET Management Agent UUID (universally unique identifier) - It changes after the ESET Management Agent is re-installed on a machine (see Double Agent situation).
•a machine hardware fingerprint - It changes if the machine is cloned or redeployed.
A question is displayed if ESET PROTECT Server detects one of the following:
•a cloned device connecting
•a change of hardware in an existing device with ESET Management Agent installed
Hardware fingerprint detection is not supported on: •Linux, macOS, Android, iOS •machines without ESET Management Agent |
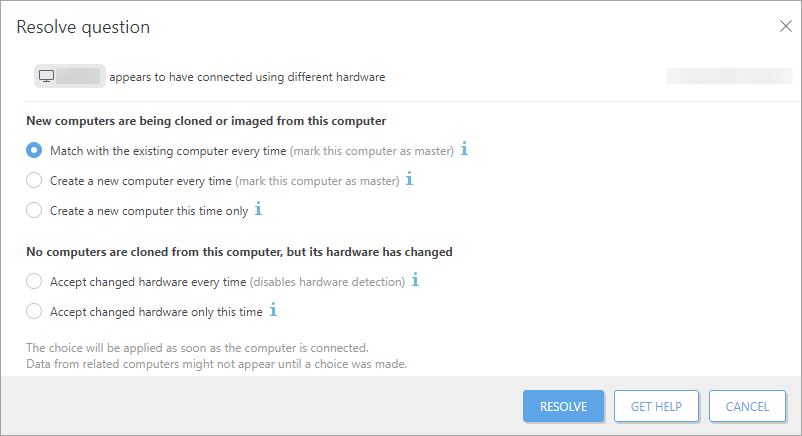
Click the question and select:
Resolve question > New computers are being cloned or imaged from this computer:
Option |
Action |
|---|---|
Match with the existing computer every time |
Select this option when: •You use the computer as a master and all its images should connect to the existing computer entry in ESET PROTECT. •You use the computer as a master to set up a VDI environment and the computer is in VDI pool and is expected to recover its identity based on a hardware fingerprint ID. |
Create a new computer every time |
Select this option when you use this computer as a master image and you want ESET PROTECT to automatically recognize all clones of this computer as new computers. Do not use with VDI environments. |
Create a new computer this time only |
Computer is cloned only once. Select to create a new instance for the cloned device. |
Read also the Manage cloned computers in ESET PROTECT Knowledgebase article. |
Resolve question > No computers are cloned from this computer, but its hardware has changed:
Option |
Action |
|||
|---|---|---|---|---|
Accept changed hardware every time |
Disable the hardware detection permanently for this device. Use only if non-existent hardware changes are reported.
|
|||
Accept changed hardware only this time |
Select to renew the hardware fingerprint of the device. Use this option after the hardware of the client computer is changed. Future hardware modifications will be reported again. |
Click Resolve to submit the selected option. The cloning question gets resolved next time the cloned computer connects to ESET PROTECT.
If you do not resolve a question in 30 days, the Create a new computer this time only option will be selected automatically. |
Double Agent situation
If an ESET Management Agent is uninstalled (but the computer is not removed from Web Console) on the client machine and installed again, there are two same computers in the Web Console. One is connecting to ESET PROTECT and the other one is not. The Questions dialog window does not handle this situation. Such a situation is the result of an incorrect agent removal procedure. The only solution is to manually ![]() remove the computer that is not connecting from the Web Console. The history and logs created before the re-installation will be lost afterward.
remove the computer that is not connecting from the Web Console. The history and logs created before the re-installation will be lost afterward.
Using the Delete not connecting computers task
If you have a VDI pool of computers and did not resolve the question (refer above) correctly, the Web Console creates a new computer instance after reloading the computer from the pool. Computer instances stack up in the Web Console and subscriptions can get overused. We do not recommend solving this issue by setting up a task for deleting not connecting computers. Such a procedure removes the history (logs) for deleted computers, and subscriptions can also be overused.
Overused subscriptions
When a client computer with installed ESET Management Agent and activated ESET security product gets cloned, each cloned machine can claim another subscription seat. This process can overuse your subscriptions. In VDI environments, use an offline activation file to activate ESET products and contact ESET to modify your subscription.
Notifications for cloned computers
A user can choose from three prepared notifications for cloning-related actions. To set up a notification, select the ![]() Notifications menu in the Web Console.
Notifications menu in the Web Console.
•New Computer Enrolled—Notify if a computer is connected for the first time to the selected static group (the group All is selected by default)
•Computer Identity Recovered—Notify if a computer was identified based on its hardware; the computer was cloned from a Master machine or other known source
•Potential Computer Cloning Detected—Notify about a significant hardware modification or cloning if the source machine was not flagged as a Master before