What to do in case of a robbery
Mark a computer or device as missing if you suspect that it has been lost or stolen. To do so from the Anti-Theft web interface, select the device that is missing and click Status, and then click My device is missing.
Anti-Theft will prohibit access to all accounts except for the Phantom account (Windows devices only) and start taking regular camera pictures and screenshots that can be viewed in the Activity menu.
Anti-Theft status can be as follows:
•Not missing —Desired value when no activity is needed (green icon ![]() ), or you need to perform the specific action due to optimization issues (yellow icon
), or you need to perform the specific action due to optimization issues (yellow icon ![]() ) displayed in the Optimization section.
) displayed in the Optimization section.
•Marked as Missing—Device was reported stolen or missing, Anti-Theft records data.
•Suspicious activity—Successful Phantom Account auto-login.
To report a device as stolen or missing, select the device and click My device is missing.
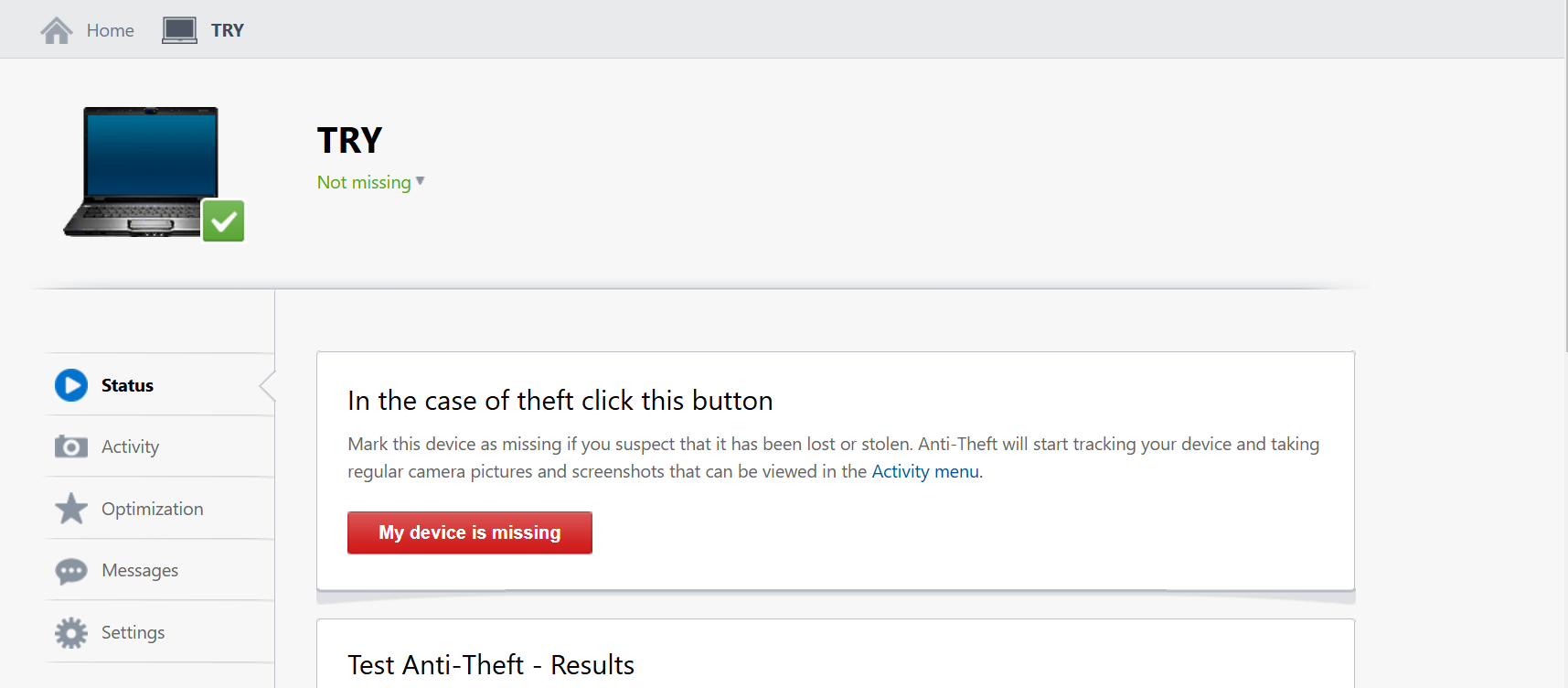
The following actions will be taken:
•You will receive an email notification that your device status has been set to missing.
•When the missing computer or device goes online, ESET Security Ultimate, ESET Internet Security, ESET Smart Security Premium or ESET Mobile Security will record information on regular intervals. This data can be viewed in the Activity tab.
•The missing device will automatically restart within a few minutes of going online.
•If a Phantom Windows account exists, the device will use this account as the default account and automatically log into it. This prevents people from logging into other user accounts or accessing user data.
•If you want to erase all data from its memory card and clear contacts and accounts, click the Wipe button. This feature is not supported on mobile devices running Android 14 or later and when using ESET Mobile Security version 10 or later.
Click Run a test to simulate data gathering activities carried out by Anti-Theft when your device is marked as missing. |
Important recommendations
It is highly recommended that you take the following actions to mitigate the potential damage caused by criminals:
•Keep the details of your ESET HOME account log solely to yourself—Do not share the username and password you use to log into the Anti-Theft web interface. We recommend not to save the login credentials in your web browser.
•Change your email account password—Particularly if you use email programs such as Outlook Express or Mozilla Thunderbird, or if you have stored webmail passwords recorded in your web browser (for example, your Gmail account password).
•Change your internet banking password and check your bank accounts for suspicious transactions.
•Change passwords for all of your social media presences – This concerns mainly social networks like Facebook or Twitter.
Click, I recovered my device to revert it to the Normal state. The device will restart, and your normal user account will be re-activated.
The default monitoring period is 14 days. Five days before expiration, you will receive an email from ESET prompting you to review the status of your device. |
IP geolocation of the device
If no information regarding the location of your device is available, you can try locating your device using IP addresses obtained from the device (see the IP Addresses tab) using the following online service: www.who.is
If the device is stolen, with the help of a law enforcement organization, the internet service provider of the detected public IP address might help locate the device using the private IP address behind NAT (not visible from the internet).