IoC search
IoC search enables users to search for IoC (Indicators of Compromise) types, such as Botnet, C&C, Domain, File, IP, and URL in the ESET Threat Intelligence database. The data is deduplicated, and the data retention period is 90 days.
IoC search is now available as a preview feature. The rate limit is 300 searches per customer per week, and the search results limit is 100 per IoC type. |
The IoC search feature provides two options:
•Simple search—Enables users to input a single value without specific syntax
•Advanced search—Enables users to define multiple search criteria and use logical operators to narrow the search results more precisely
Simple search
Input values for the simple search are the following:
•Hash (MD5, SHA-1, SHA-256)
•URL
•Domain name
•IP address
Users can also use the wildcard string modifier—%. A wildcard acts as a placeholder for one or more characters and can match part of a string. Users can use it to search for patterns instead of exact matches when the exact value is unknown or only partially known, for example, %example.com.
Advanced search
The advanced search input can contain multiple conditions combined using operators and modifiers.
Operators for the advanced search
•:—Equality operator, for example, field:value
Modifiers for the advanced search
•Dates:
od/w/m/y—Supported intervals, where: d—days, w—weeks, m—months, y—years
o-—Lower than, for example, 3d-—lower than three days before
o+—Greater than, for example, 1d+—greater than one day before
•Integers:
o-—Lower than, for example, 100-—lower than 100
o+—Greater than, for example, 10+—greater than 10
The advanced search syntax example: topic:domain last_seen:1d- confidence:High count:10+
Refer to the list of the fields for the advanced IoC search shown in the table.
Advanced IoC search restrictions •Each field can only be used once in the search input. •Each search condition is connected by the logical operator AND. •The wildcard modifier cannot be used in the advanced search. |
Using the IoC search
To use the IoC search, follow the steps below:
1.Navigate to Threat Insights > IoC Search.
2.Type the value to search for into the search bar. To use the advanced search option, click the Advanced search toggle.
3.Click the Search button.
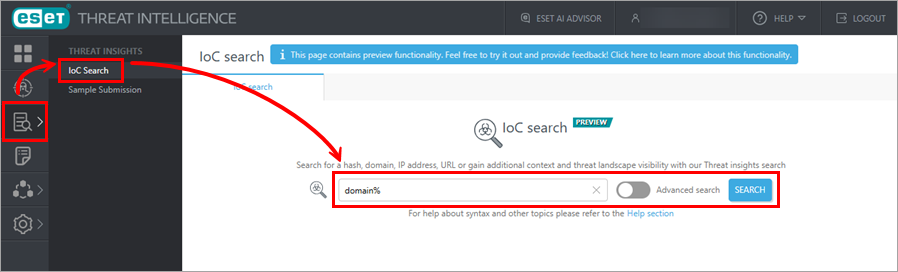
4.Review the search results, including useful statistical data below the search bar. To get more information about a specific IoC from the search result, click the IoC of your interest and see the details in the opened side panel. If the IoC additionally contains a Threat name, you can see detailed information about this threat by clicking the Open Detail button in the side panel.
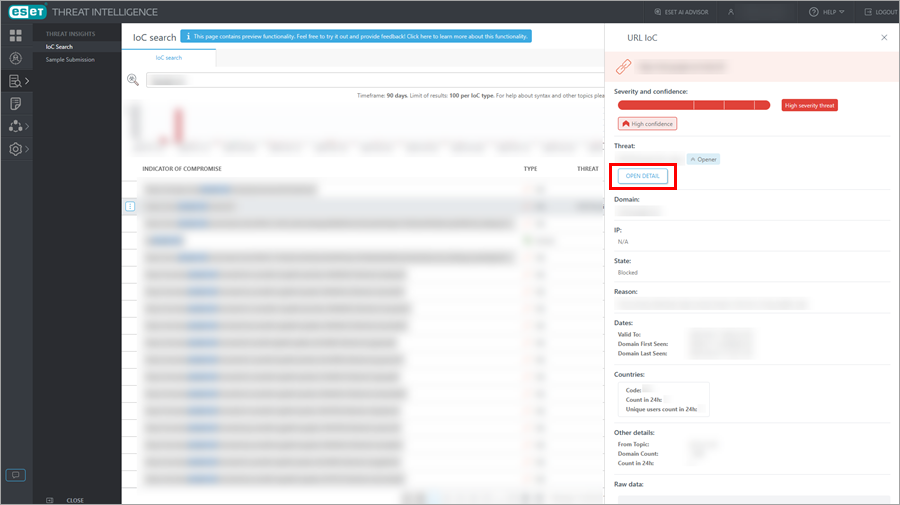
5.To clear the search results, click the Clear button next to the search bar.
Fields for the advanced IoC search
Field name |
Data type |
Enumeration |
|---|---|---|
cnc |
string |
|
cncs.last_alive |
date |
|
cncs.url |
string |
|
confidence |
string |
•High •Medium •Low |
count |
integer |
|
count_24h |
integer |
|
countries.code |
string |
|
countries.count |
integer |
|
countries.count_24h |
integer |
|
countries.country |
string |
|
countries.region |
string |
|
countries.unique_users_count_24h |
integer |
|
direction |
string |
•Incoming •Outgoing |
domain |
string |
|
domain_count |
integer |
|
domain_first_seen |
date |
|
domain_last_seen |
date |
|
downloaded_detection |
string |
|
file.count |
integer |
|
file.file_name |
string |
|
file.file_type |
string |
|
file.first_seen |
date |
|
file.md5 |
string |
|
file.sha1 |
string |
|
file.sha256 |
string |
|
file.size |
integer |
|
file.ssdeep |
string |
|
file_name |
string |
|
file_type |
string |
|
first_seen |
date |
|
from_topic |
string |
|
host |
string |
|
ip |
string |
|
last_alive |
date |
|
last_seen |
date |
|
location |
string |
|
md5 |
string |
|
opener_detection |
string |
|
port |
string |
|
prot_l4 |
string |
|
prot_l7 |
string |
|
protocol |
string |
|
reason |
string |
|
sha1 |
string |
|
sha256 |
string |
|
size |
integer |
|
ssdeep |
string |
|
state |
string |
•Blocked •Phishing •Unwanted •BlockedObject |
threat |
string |
|
topic |
string |
•botnet •cc •domain •file •ip •url |
url |
string |
|
valid_to |
date |
|