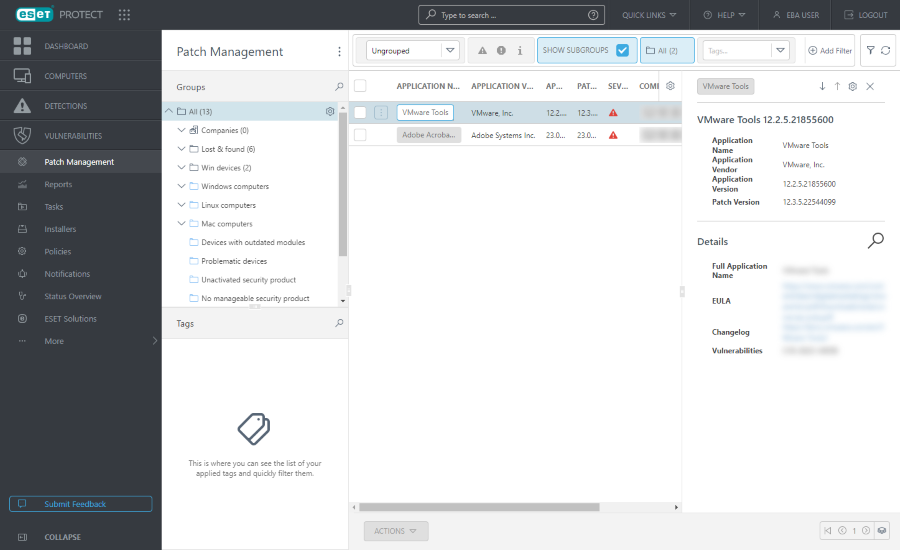
Patch Management
Patch management helps ensure that systems and applications are secure against known vulnerabilities and exploits. The Patch management section lists all available patches remedying the detected vulnerabilities and makes the remediation process easier through automated software updates. With patching options, you can promptly ensure that your endpoints are updated with the latest security patches.
Prerequisites To view and enable ESET Vulnerability & Patch Management, ensure you have one of the following tiers: •ESET PROTECT Elite •ESET PROTECT Complete •ESET PROTECT MDR •ESET PROTECT MDR Ultimate You can enable ESET Vulnerability & Patch Management on computers running: •ESET Management Agent version 10.1+ •ESET Endpoint Security for Windows version 10.1+ •ESET Endpoint Antivirus for Windows version 10.1+ •ESET Server Security for Microsoft Windows Server version 11.0+ •ESET Mail Security for Microsoft Exchange Server 11.0+ •ESET Security for Microsoft SharePoint Server 11.0+ •ESET Endpoint Security for macOS version 8.0+ •ESET Endpoint Antivirus for Linux version 11.0+ (Patch Management available from version 12.0). Vulnerabilities detection is currently supported only on the following operating systems: ✓Ubuntu Desktop 20.04 LTS ✓Ubuntu Desktop 22.04 LTS ✓Ubuntu Desktop 24.04 LTS ✓Red Hat Enterprise Linux 8 with supported desktop environment installed ✓Red Hat Enterprise Linux 9 with supported desktop environment installed ✓Linux Mint 20 ✓Linux Mint 21.1, Linux Mint 21.2 •ESET Server Security for Linux version 11.0+ (Patch Management available from version 12.0) |
You can also purchase ESET Vulnerability & Patch Management as a separate add-on for the ESET PROTECT Entry and ESET PROTECT Advanced tier. |
ESET Vulnerability & Patch Management is not supported on Windows devices with ARM processors. |
|
ESET Bridge does not affect the reporting of vulnerabilities. ESET Bridge blocks the Patch Management network traffic when ESET Vulnerability & Patch Management is disabled. When you apply the Vulnerability & Patch Management Policy on managed computers and the computer running ESET Bridge, ESET Bridge (version 3 and later) automatically allows the Patch Management network traffic by disabling the Access Control List (ACL) rules. ESET PROTECT becomes an open proxy that allows the routing of all network traffic: •ESET PROTECT Web Console will display the Access restrictions are disabled alert in computer details. You can hide the alert by disabling Report open proxy in the ESET Bridge Policy > Reporting. •We recommend setting up proxy authentication to improve network security. |
Patch Management is enabled during Vulnerabilities & Patch Management activation.
View Patch Management
You can view Patch Management from several places:
•Click Patch Management in the main menu to open the Patch Management section and view a list of patches
•Click Computers > select Details > in the Vulnerability & Patch Management tile, click Show patches to open the Patch Management section
Grouping the view
To group patches, select from the drop-down menu:
•Ungrouped—default view
•Group by Application name—when grouped, click an application row and click Show Devices to display devices (computers) where a patch will be applied
Filtering the view
To filter, click Add Filter:
1.In some filters, you can select the operator by clicking the operator icon next to the filter name (the available operators depend on the filter type):
Equal to or Contains
Not equal to or Does not contain
Greater than or equal to
Less than or equal to
2.Select one or more items from the list. Type a search string or select the items from the drop-down menu in the filter fields.
3.Press Enter. Active filters are highlighted in blue.
•Application name—the name of the application with the vulnerability
•Application version—the version of the application causing the vulnerability
•Patch version—the patch version
•Severity—severity level, including informational, warning, or critical
•Computer name—the name of the affected computer
•Application vendor—the name of the application vendor
Side panel with details
Click an application name to view application details in a side panel. Application preview manipulation:
•![]() Next—displays the next application details in the side panel
Next—displays the next application details in the side panel
•![]() Previous—displays the previous application details in the side panel
Previous—displays the previous application details in the side panel
•![]() Manage content for Patch Details—manages how the side panel sections are displayed and in what order
Manage content for Patch Details—manages how the side panel sections are displayed and in what order
•![]() Close—closes the side panel
Close—closes the side panel
Deploy patches
You can patch only selected apps. Only apps installed for all users per computer are supported for patching. Currently, the patch management does not support patching the apps installed per user. |
We recommend that you enable the auto-patch management via a policy. |
You can enable operating system auto-updates and select the severity levels for applying OS updates via a policy. ESET Endpoint Security for macOS does not currently support OS scanning and patching. |
When automated patching is configured, the solution will automatically patch applications during maintenance windows.
Some applications may restart the computer automatically after an upgrade. |
Some applications (for example, TeamViewer) can be licensed to a specific version. Revise your applications. To avoid an unnecessary upgrade, set Auto-patch strategy > Patch all except excluded applications while creating a policy. |
Alternatively, you can deploy patches via:
•Select the applications where you want to deploy patches > click the Actions button and click Update.
•To patch an application on all affected devices, apply the Group by Application name view, select the application name row, click ![]() and click Update.
and click Update.
After you deploy patches with the Update button, a new client task Apply application patch will be created automatically in Tasks. For endpoints, the patches will be applied based on the Vulnerability & Patch Management scheduler set in Policies. For servers, the patches will be installed after a 60-second countdown with no option to postpone.
For more information, see Vulnerability & Patch Management FAQ.