Sample reports
Follow the steps below to report a suspicious sample:
1.In the Reports screen, click Submit File For Analysis.
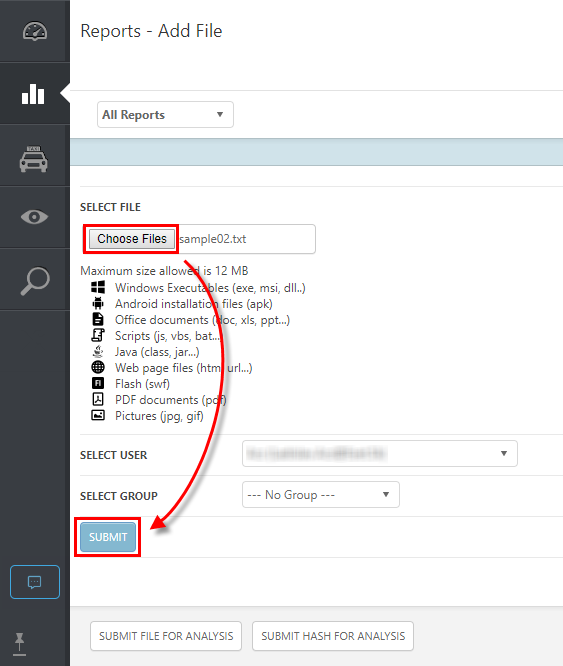
2.Click Choose Files, browse to the sample file, double click it and then click Submit.
3.The uploaded sample file will be shown in the Reports screen when Sample Reports is selected.
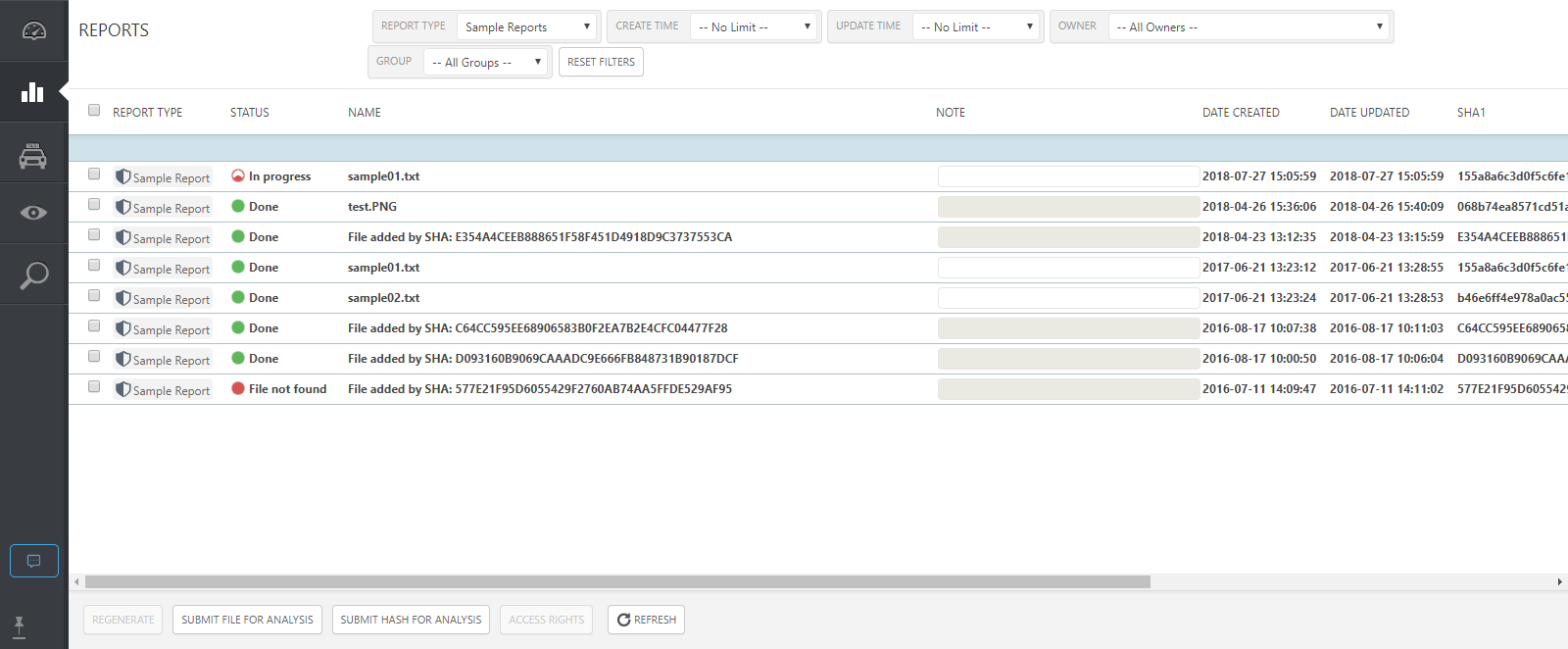
Click here to view larger image
4.Once the submitted sample file is analyzed, you can download the results of the analysis as a pdf or xml document. Instructions to download and open the attachment (Additional data) are included at the end of all PDF reports.
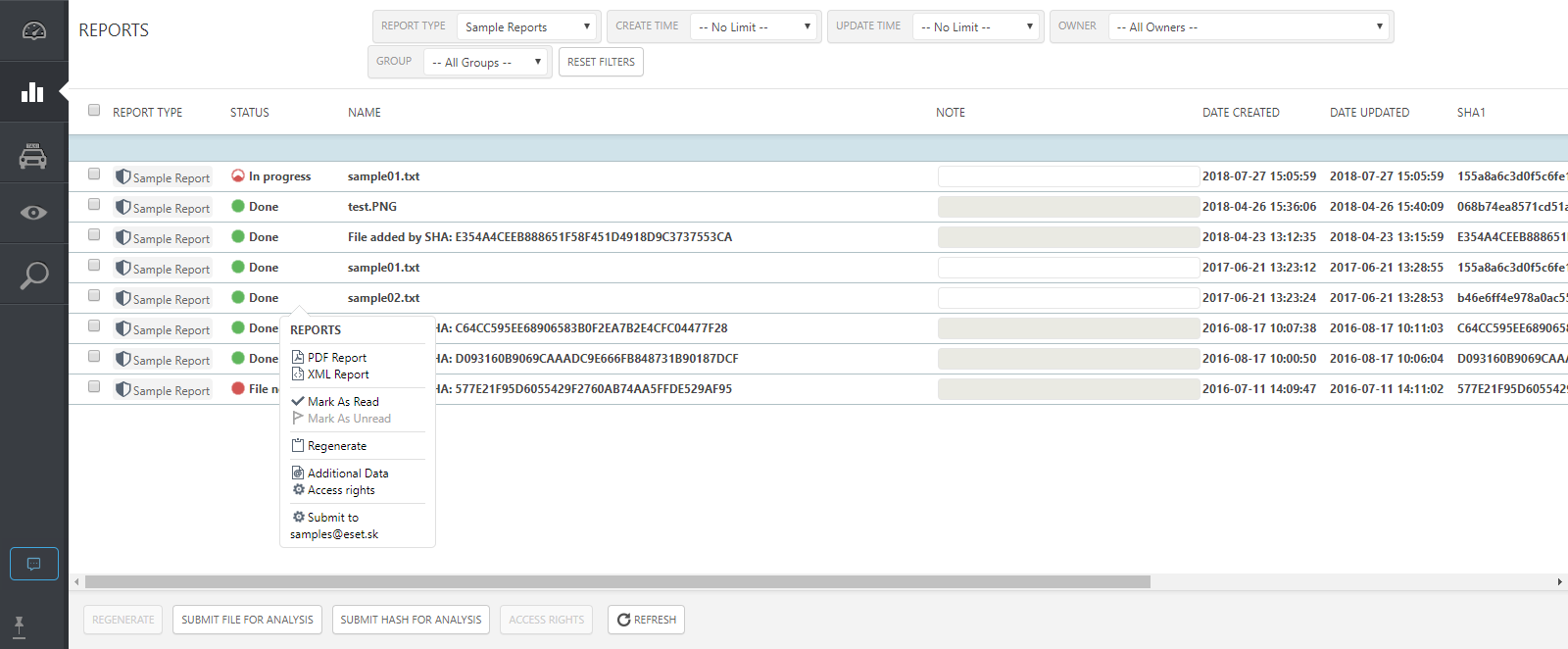
Click here to view larger image
To report a suspicious hash, click Submit Hash For Analysis and follow the on-screen instructions.
The following types of files can be analyzed:
•Windows Executables (exe, dll…)
•Android application installation files (apk)
•Office documents (doc, xls, ppt…)
•Scripts (js, vbs, bat…)
•Java (class, jar…)
•Web page files (htm, URL...)
•Flash (swf)
•PDF documents (pdf)
•Pictures (jpg, gif)
A Sample Report provides the following information:
•Detailed detection information—Name of given malicious file in competing security solutions that also detected the file.
•Reputation information from ESET LiveGrid®
oHow frequently the file was seen in the world and in the country the report was requested from
oWhen it was first seen and last seen in the world
•Similar binaries—Existence of similar files based on DNA Detection.
•File details
oName, type, size, MD5, SHA1, SHA256 and Signature
oPE Information—Machine, Timestamp, Mafic Optional Header, Entry Point, Subsystem, OS Version, Subsystem Version, Linker Version, Image Version, Number of Sections and Sections.
•Sandbox output
oFile system changes with Size and SHA1 information
oRegistry changes with Type of change and Value of change
oNetwork communication with Type of communication, IP Address and Location it communicated with and PDNS value
oProcesses with Time the process started, PID value, Parent value and Name
