Windows Login Protection
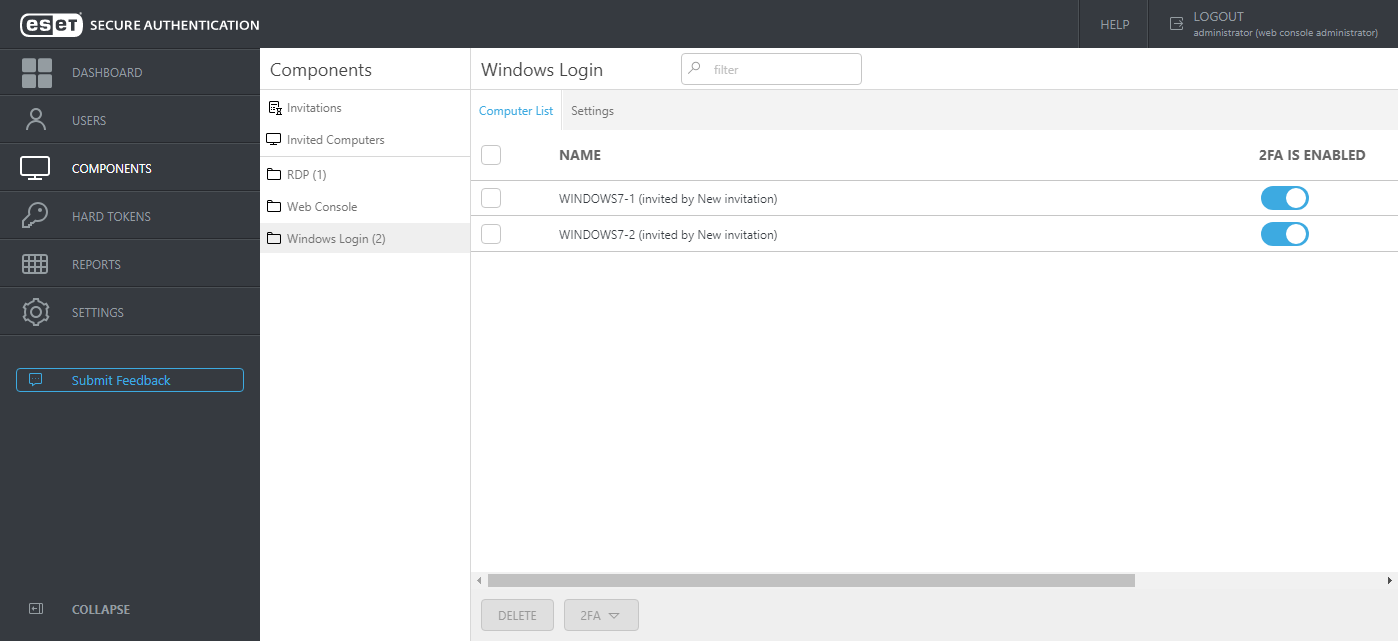
ESA features local login protection for Windows in a domain or LAN environment. To utilize this feature, select the Windows Login component during ESA installation. When the installation is complete, access the ESA Web Console, click Components > Windows Login. The list of computers where the Windows Login component of ESA is installed will display. From this screen, you can enable/disable 2FA protection per computer.
If you have a long list of computers, use the Filter field to search for a specific computer by typing its name.
If the Windows Login component of ESA version 2.6 or later is uninstalled from a specific computer, the computer will be automatically removed from the Computer List of ESA Web Console. A computer entry can be deleted manually also from the Web Console. Select a computer entry and click Delete, or hover a computer, click ![]() and select Delete. Click Delete in the confirmation window also. Suppose a computer entry is removed from the Computer List, but the Windows Login component is not removed from the specific computer. In that case, the computer will show up again in the Web Console with default settings.
and select Delete. Click Delete in the confirmation window also. Suppose a computer entry is removed from the Computer List, but the Windows Login component is not removed from the specific computer. In that case, the computer will show up again in the Web Console with default settings.
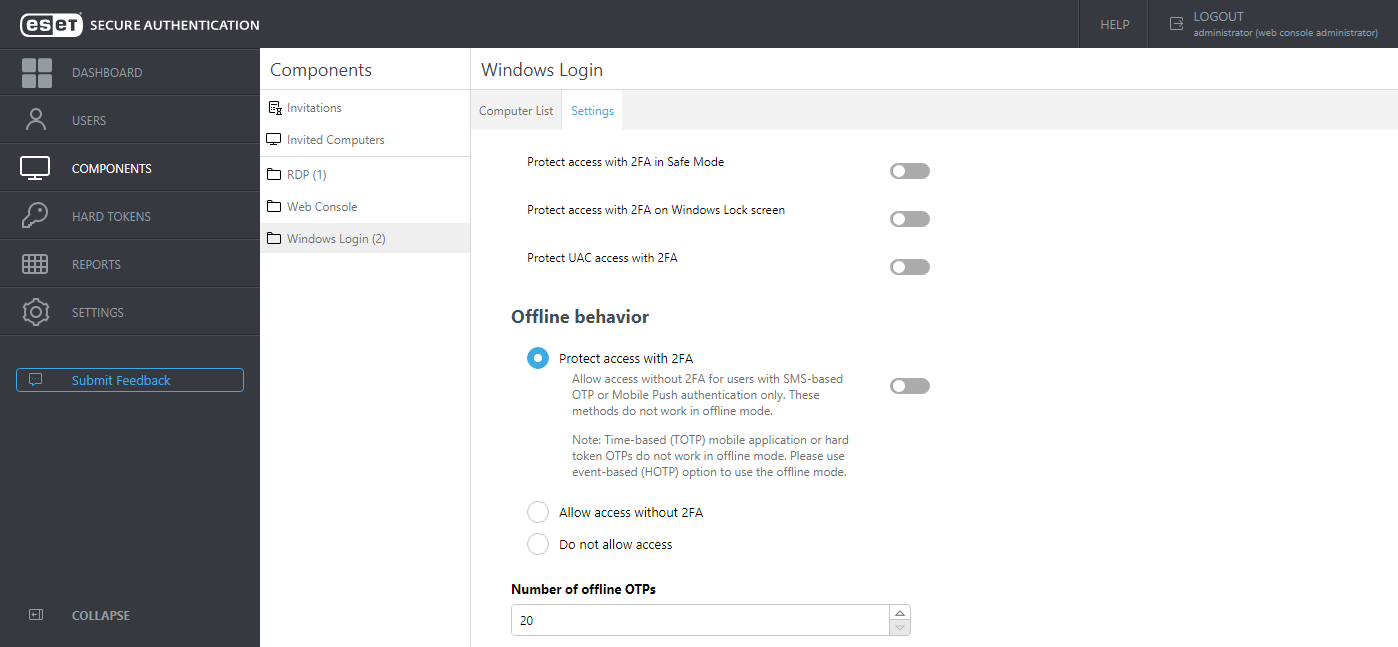
Click the Settings tab to see available settings.
From this screen, you can see various options to apply 2FA, including the option to apply 2FA protection for Safe Mode, Windows lock screen, and User Account Control (UAC).
Suppose the machine where the Windows Login component of ESA is installed must be offline part of the time, and you have users who have SMS authentication enabled. In that case, you can enable Allow access without 2FA for users with SMS-based OTP or Mobile Push authentication only.
If a user using SMS delivery for OTP wants to have an OTP re-sent, they can close the window requiring OTP, and after 30 seconds, type their username and password again to receive a new OTP.
2FA protection cannot be bypassed by an attacker even if the attacker knows the username and password, thus providing better protection of sensitive data. Of course, we assume the hard drive is not accessible by the attacker, or the drive's content is encrypted.
We recommend combining 2FA protection with whole disk encryption to mitigate the breach risk if an attacker has physical access to the disk.
2FA enabled for offline mode If 2FA protection is enabled for offline mode, all users whose accounts are secured by 2FA and who want to use a 2FA-protected PC must log in to that PC for the first time while the PC is online. By 'online',we mean that the main computer where the Authentication Server is installed and the ESET Secure Authentication On-Prem Service service is running and can be pinged from the 2FA-secured computer. Suppose the Windows Login component is installed on the same computer where the Authentication Server is installed, and 2FA protection for Safe Mode is enabled. Simultaneously, the offline mode is disabled (Do not allow access is selected in Offline behavior section). In that case, the user will be allowed to log in to Safe Mode (without networking) without OTP. |
The offline mode allows to log in 20 times using valid OTP each time. If the limit is exceeded, the machine needs to be online when trying to log in. Whenever the machine is online while trying to log in, the limit counter is reset. You can increase the number of offline login limit in the Web Console at Components > Windows Login > Settings > Number of offline OTPs.
Time-based OTPs are not cached OTPs generated by a time-based hard token or time-based OTPs generated by the mobile application are not stored in the offline cache of Windows Login plugin. |
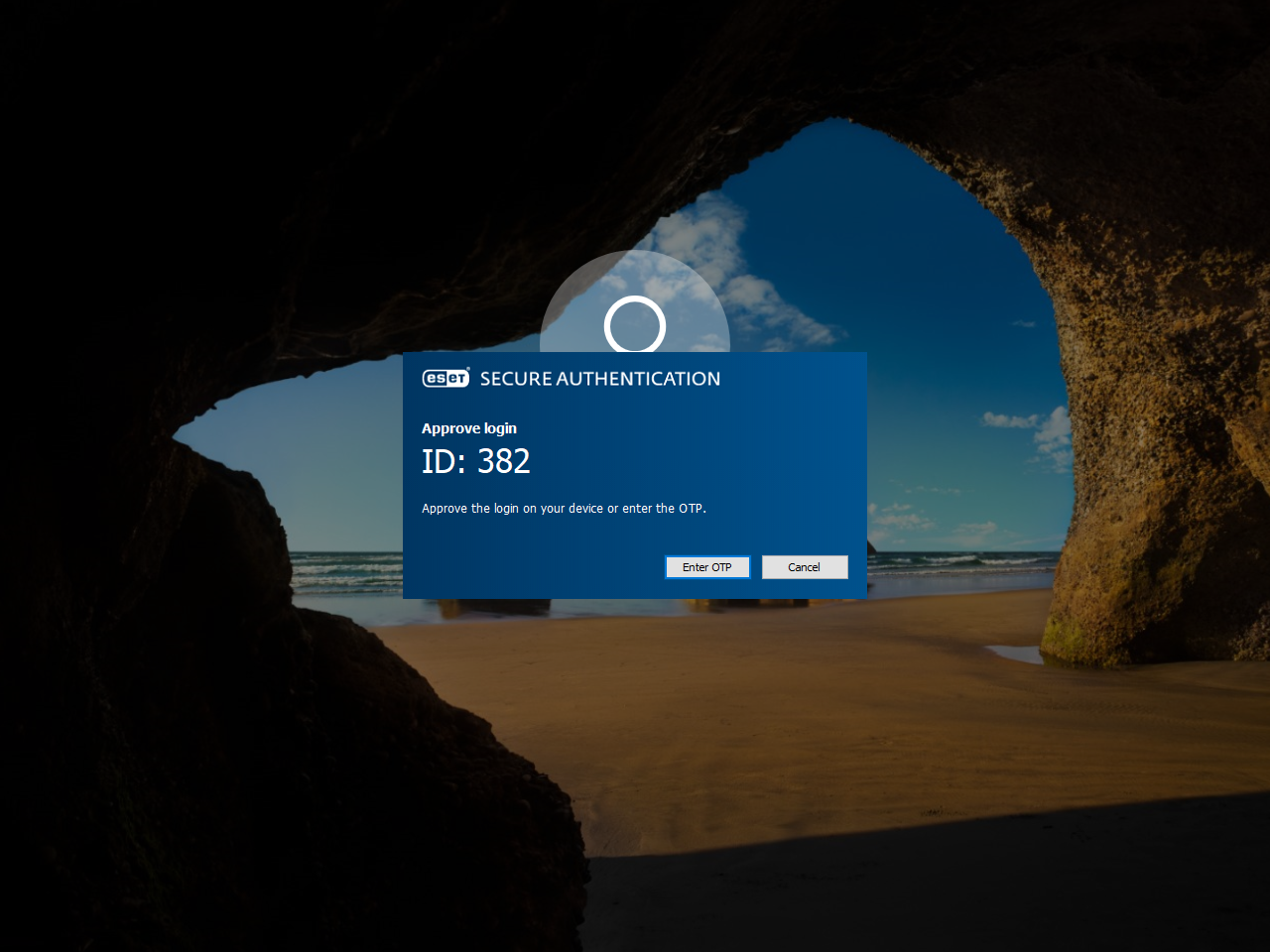
Suppose Windows 10 login is secured by ESA. After typing a valid username and password, users will be prompted to approve login on their Android/iOS mobile device, or Android/Apple watch, or to type an OTP.