Configuration of ESET security product
ESET Cloud Office Security users
To use ESET LiveGuard Advanced in ESET Cloud Office Security, create a new policy or configure an existing one. Users or groups assigned with this policy will have additional protection. For more information, see Protection settings for ESET LiveGuard Advanced.
ESET management console users
To enable ESET LiveGuard Advanced service on a client machine, a user needs to fulfill requirements and create a policy to set the service.
In the ESET PROTECT Web Console, create a new policy or edit an existing one and assign it to machines where you want to use the ESET LiveGuard Advanced.
If you enable the ESET LiveGuard Advanced on a machine where the service is not activated by the license, the setting will not apply. Other settings in the policy would apply. |
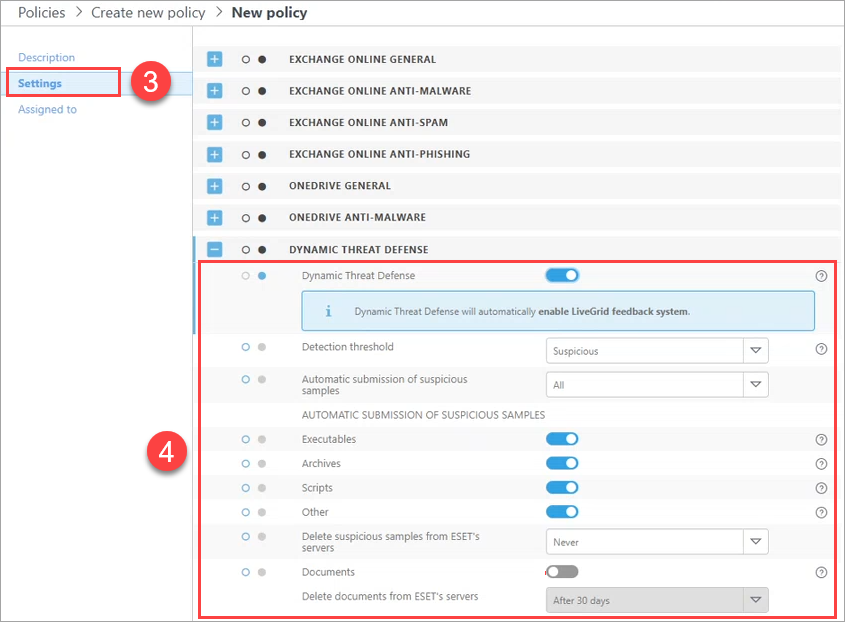
ESET LiveGuard Advanced Settings
1.Log in to Web Console of your ESET management console and create or edit a policy.
2.In the Settings section, select your product and navigate to:
Policy |
Setting |
|---|---|
ESET Endpoint for Windows |
Detection Engine > Cloud-Based protection |
ESET Mail Security for Microsoft Exchange (V6+) |
Computer > Cloud-Based protection |
ESET Server Security for Microsoft Server (V6+) |
Detection Engine > Cloud-Based protection |
ESET Endpoint for Linux (V7+) |
Detection Engine > Cloud-Based protection |
ESET Server/File Security for Linux (V7+) |
Detection Engine > Cloud-Based protection |
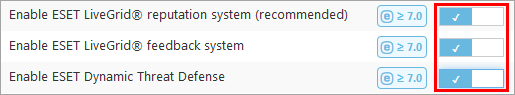
3.To enable the ESET LiveGuard Advanced, you have to switch on all three settings in the Cloud-Based protection section.
Starting from ESET Endpoint for Windows version 10.1 or later, submission of documents is enabled by default. |
Section: Cloud-Based protection |
Description |
|---|---|
Enable ESET LiveGrid® reputation system (recommended) |
Using reputation information from ESET LiveGrid®. |
Enable ESET LiveGrid® feedback system |
Submitting suspicious files to ESET cloud. |
Enable ESET LiveGuard Advanced |
Submitting files for analysis in ESET LiveGuard Advanced. |
4.You can refine which files are sent to ESET cloud when they are detected or identified as suspicious.
Section: Submission of samples |
Description and recommendation |
|---|---|
Manual submission of samples |
Enables the option to manually submit samples to ESET (Windows products only) |
Automatic submission of detected samples |
Select what kind of samples are automatically submitted to ESET for analysis when detected by the Detection engine. |
Executables, Archives, Scripts, Other |
Select types of files that are automatically submitted to the ESET cloud for analysis if the local Detection engine does not detect them. We recommend allowing submitting of all file types. |
Possible Spam emails |
Submission of possible spam emails. (ESET Endpoint for Windows only) |
Delete executables, archives, scripts, other samples and possible spam emails from ESET's servers |
Action after the analysis is done. |
Documents |
Submitting of documents. |
Delete documents from ESET's servers |
Action after the analysis is done. |
Exclusions |
List of file extensions which excludes files from submitting. Extensions are added in the following format: *.ext? where: * stands for the filename ext stands for the file type extension ? stands for one optional character. This is optional. |
Maximum size of samples (MB) |
Maximum size of a submitted file. |
5.Set up detection threshold and actions taken after a file has a positive result above the threshold.
Section: ESET LiveGuard Advanced |
Description and recommendation |
|---|---|
Status of the result of the analysis which triggers the Action after detection. |
|
Action after detection |
Action which the ESET security product does if the analyzed file has a result equal to or above the Detection threshold. |
Maximum wait time for the analysis (min) |
Maximum wait time for the analysis result before the mail is delivered or the downloaded file is made available. |
Proactive protection |
Proactive protection setting. You can enable the execution of files whose analysis is not yet finished. |
6.Finish the policy by selecting computers or groups to be assigned by the policy. New settings are applied after the next replication between Server and Agents (usually a few minutes).