Mobile Device Connector prerequisites
If the port or the hostname for the MDM server is changed, all mobile devices must be re-enrolled. For this reason, it is recommended that you set up a dedicated hostname for the MDM server so that if you ever need to change the host device of the MDM server, you can do so by reassigning the new host device's IP address to the MDM hostname in your DNS settings. |
The following prerequisites must be met to install Mobile Device Connector on Windows:
•Public IP address/hostname or public domain accessible from the internet.
If you need to change the hostname of your MDM Server, you will need to run a repair installation of your MDC component. If you change the hostname of your MDM Server, you will need to import a new HTTPS Server certificate that includes this new hostname for MDM to continue working correctly. |
•Ports open and available - see the complete list of ports. We recommend using default port numbers 9981 and 9980, but these can also be changed in configuration file of your MDM Server if needed. Ensure that mobile devices are able to connect via specified ports. Change your firewall and/or network settings (if applicable) to make this possible. Read more about MDM architecture.
•Firewall settings - when installing Mobile Device Connector on non-server OS such as Windows 7 (for evaluation purpose only), ensure to allow communication ports by creating firewall rules for:
C:\Program Files\ESET\RemoteAdministrator\MDMCore\ERAMDMCore.exe, TCP port 9980
C:\Program Files\ESET\RemoteAdministrator\MDMCore\ERAMDMCore.exe, TCP port 9981
C:\Program Files\ESET\RemoteAdministrator\Server\ERAServer.exe, TCP port 2222
Actual paths to .exe files may vary depending on where each of the ESET PROTECT components is installed on your client OS system. |
•A database server already installed and configured. Ensure you meet Microsoft SQL or MySQL requirements.
•RAM usage of MDM connector is optimized so there can be maximum of 48 "ESET PROTECT MDMCore Module" processes running concurrently, and if the user connects more devices, the processes will then periodically change for each device that currently needs to use the resources.
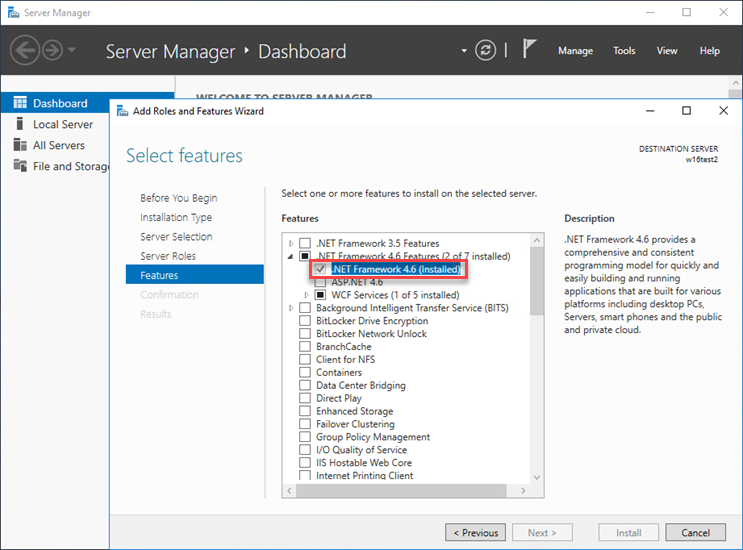
•Microsoft SQL Server Express installation requires Microsoft .NET Framework 4. You can install it using the Add Roles and Features Wizard:
Certificate requirements
•You will need an SSL certificate in .pfx format for secure communication over HTTPS. We recommend that you use a certificate provided by a third-party Certification Authority. Self-signed certificates (including certificates signed by the ESET PROTECT On-Prem CA) are not recommended because not all mobile devices let users accept self-signed certificates.
•You need to have a certificate signed by CA and the corresponding private key, and utilize standard procedures (traditionally using OpenSSL), to merge those into one .pfx file:
openssl pkcs12 -export -in certificate.cer -inkey privateKey.key -out httpsCredentials.pfx
This is the standard procedure for most servers which use SSL certificates.
•For Offline installation, you will also need a Peer certificate (the Agent certificate exported from ESET PROTECT On-Prem). Alternatively, you can use your custom certificate with ESET PROTECT On-Prem.