Add computers using RD Sensor
ESET Rogue Detection (RD) Sensor will be deprecated (there will be no future updates). Some of its features may not work properly. You can no longer manage RD Sensor configuration via a policy. |
If you are not using AD synchronization, the easiest way to find an unmanaged computer in your network structure is to use the RD Sensor. You can install the ESET Rogue Detection Sensor on Windows or Linux. RD Sensor monitors the network in which it is deployed and when a new device without an Agent connects to the network it reports this information to the ESET PROTECT On-Prem.
In Reports, go to section Computers and click the Rogue computers report.
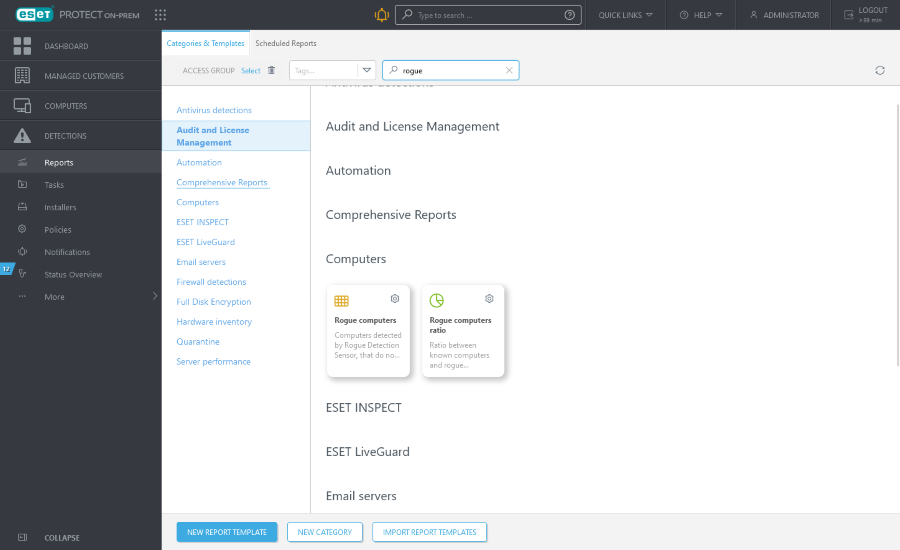
The Rogue computers report lists computers found by the RD Sensor. You can add computers by clicking the computer you want to Add, or you can Add all displayed items.
If you are adding a single computer, you can use a preset name or specify your own (this is a display name that will be used in ESET PROTECT Web Console only, not an actual hostname).
•You can also add a description if you want to. If this computer already exists in your ESET PROTECT On-Prem directory, you will be notified and can decide what to do with the duplicate. The available options are: Deploy Agent, Skip, Retry, Move, Duplicate or Cancel.
•When the computer is added, a window will open with an option to Deploy Agent.
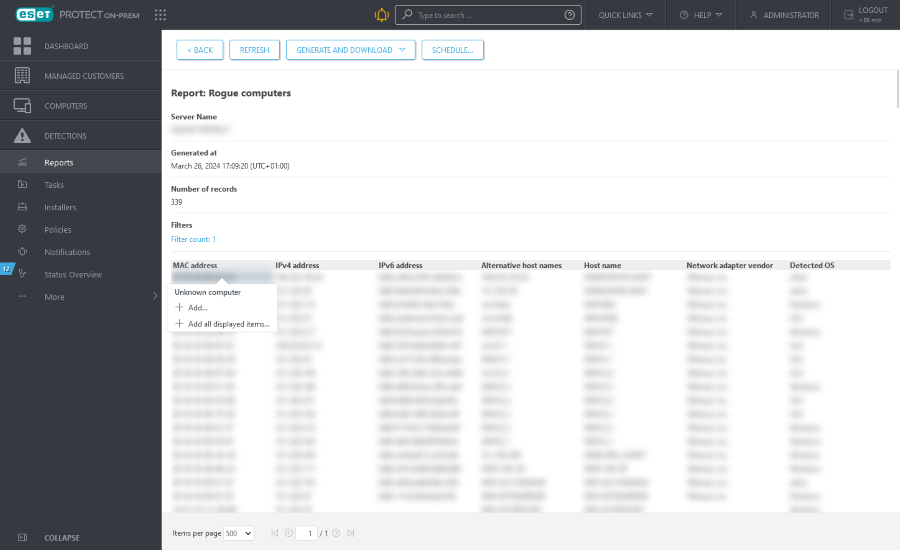
If you click Add all displayed items a list of computers to be added will be displayed:
1.Click ![]() next to the name of a specific computer if you do not want to include it in your ESET PROTECT On-Prem directory at this time. When you are finished removing computers from the list, click Add.
next to the name of a specific computer if you do not want to include it in your ESET PROTECT On-Prem directory at this time. When you are finished removing computers from the list, click Add.
2.Select the action to take when a duplicate is found (allow for a slight delay depending on the number of computers in your list): Skip, Retry, Move, Duplicate or Cancel.
3.An All devices successfully added window will appear.
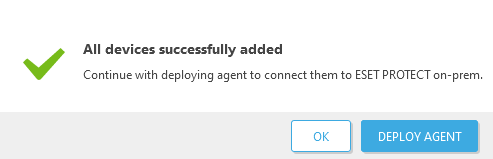
•Click Deploy Agent—In Create Installer, select the operating system and Agent deployment type.
•Click OK to deploy the Agent later. The added computers will appear in Computers. Click the computer > ![]() Platform modules to deploy the Agent:
Platform modules to deploy the Agent:
o![]() Deploy agent using an installer—In Create Installer, select the operating system and Agent deployment type.
Deploy agent using an installer—In Create Installer, select the operating system and Agent deployment type.
o![]() Deploy agent using a server task—Use the Agent Deployment Server Task to deploy the Agent.
Deploy agent using a server task—Use the Agent Deployment Server Task to deploy the Agent.
The results of the RD Sensor scan are written to a log file called detectedMachines.log. It contains a list of discovered computers on your network. You can find the detectedMachines.log file here:
•Windows
C:\ProgramData\ESET\Rogue Detection Sensor\Logs\detectedMachines.log
•Linux
/var/log/eset/RogueDetectionSensor/detectedMachines.log