Connection
Proxy settings
This setting is available only for desktop app. To configure the LAN proxy, select HTTP in the Proxy section and enter Port, Address, Username and Password.
Auto-connect
When enabled, the ESET VPN app connects to the last used location.
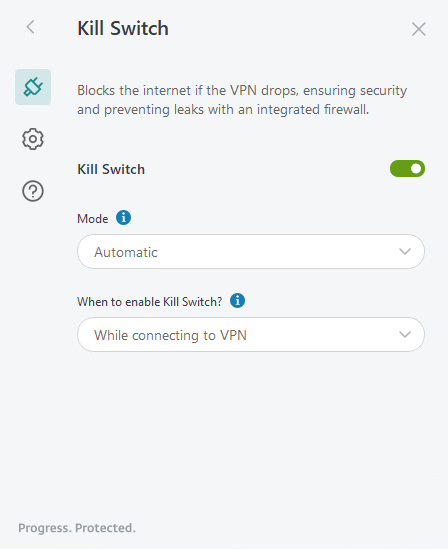
Kill Switch
This setting is available only for desktop app. The Kill Switch feature blocks all connectivity outside the VPN tunnel to ensure there is zero chance of any leak when the VPN connection drops.
Mode
When you enable Kill Switch, the following modes are available from the drop-down menu:
•Always-on—Blocks all internet access unless you are connected to the VPN, ensuring security even if the app crashes or your computer restarts.
•Automatic—Enables the Kill Switch with the firewall when you connect to the VPN and disables it when you disconnect, blocking the internet if the VPN drops or the app crashes.
When to enable Kill Switch?
From the following options, select when you want to enable Kill Switch:
•While connecting to VPN—Blocks all traffic while the VPN connection is being established to prevent any leaks.
•After connecting to VPN—Waits for the VPN connection to be fully established, preventing temporary internet interruptions.
Connection mode
The default option is Automatic, although you can select the connection mode manually. Set it to Manual, and select the Protocol and Port from the drop-down menu. There are six protocols available regardless of your operating system:
•WireGuard—A free, open-source communication protocol that uses the following algorithms:
a)ChaCha20 for symmetric encryption, authenticated with Poly1305
b)Curve25519 for ECDH
c)BLAKE2s for hashing and keyed hashing
d)SipHash24 for hashtable keys
e)HKDF for key derivation
It is typically faster than UDP and TCP protocols and more flexible than IKEv2, making it a great option for securing your online activity.
•IKEv2—A tunneling protocol providing a secure key exchange session paired with IPsec to ensure data encryption and authentication. It is usually the fastest but can be easily blocked. IKEv2 implementation utilizes AES-256-GCM for encryption, SHA-256 for integrity checks. Desktop and Android apps use ECP384 for Diffie-Hellman key negotiation (DH group 20), and iOS uses ECP521 for Diffie-Hellman key negotiation (DH group 21).
•UDP—This mode uses OpenVPN protocol. UDP is usually the fastest protocol to run OpenVPN on because there is less data verification, but it can also be blocked easily.
•TCP—This mode uses OpenVPN protocol. Due to multiple data verifications, could be slower, but it is resilient to bad network conditions and ensures stable connections.
•Stealth—Encapsulates OpenVPN in a TLS tunnel via Stunnel. It is an OpenVPN tunnel masked to look like HTTPS traffic. We recommend using this protocol if all other methods fail.
•Wstunnel—Encapsulates OpenVPN in a WebSocket. We recommend using this protocol if all other methods fail.
|
OpenVPN implementation uses the AES-256-GCM cipher with SHA512 auth and a 4096-bit RSA key. Perfect forward secrecy is also supported. |