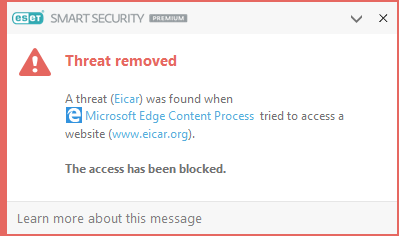
An infiltration is detected
Infiltrations reach the system from various entry points such as web pages, shared folders, email or removable devices (USB, external disks, CDs, DVDs, etc.).
Standard behavior
ESET Small Business Security detects infiltrations using:
•Real-time file system protection
Each uses the standard cleaning level and will attempt to clean the file and move it to Quarantine, or stop the connection. The notification window displays in the notification area at the bottom right corner of the screen. For details about detected/cleaned objects, see Log files. For details on cleaning levels and behavior, see Cleaning levels.
Scanning computer for infected files
If your computer is showing signs of a malware infection, for example, it is slower, often freezes, etc., we recommend that you do the following:
1.Open ESET Small Business Security and click Computer scan.
2.Click Scan your computer (for more information, see Computer scan).
3.After the scan, review the log for the number of scanned, infected and cleaned files.
If you want to scan a certain part of your disk, click Custom scan and select targets to be scanned for viruses.
Cleaning and deleting
If there is no pre-defined action to take for Real-time file system protection, the alert window prompts you to select an option. Usually the options Clean, Delete and No action appear. Selecting No action is not recommended, as this leaves infected files uncleaned. The exception is when you are sure that a file is harmless and detected by mistake.
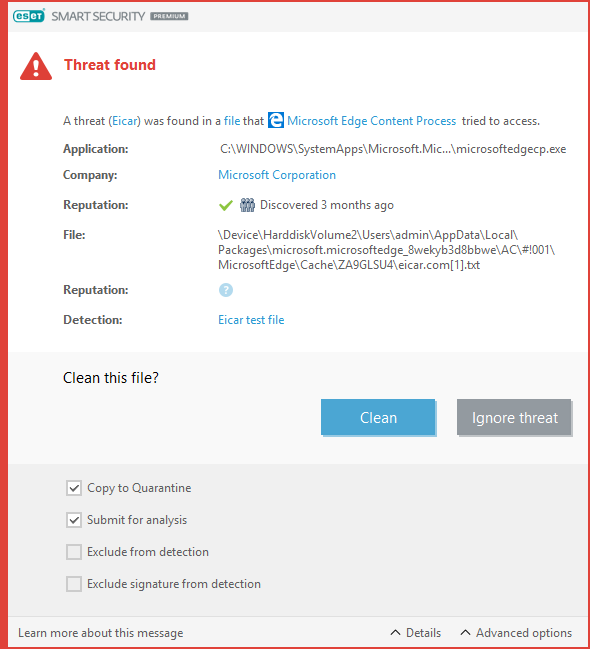
Apply cleaning if a virus has attached malicious code to a file. If so, first attempt to clean the infected file to restore it. If the file is entirely malicious code, it will be deleted.
If an infected file is locked or currently in use by a system process, it will usually only be deleted after it is released (normally after a system restart).
Restoring from the Quarantine
Access the Quarantine from the ESET Small Business Security main program window by clicking Tools > Quarantine.
Quarantined files can also be restored to their original location:
•Use the Restore feature for this purpose, which is available from the context menu by right-clicking a given file in the Quarantine.
•If a file is marked as a potentially unwanted application, the Restore and exclude option is enabled. See also Exclusions.
•The context menu also offers the Restore to option, which enables you to restore a file to a location other than the one from which it was deleted.
•The restore functionality is not available in some cases, for example, for files located on a read-only network share.
Multiple threats
If any infected files were not cleaned during Computer scan (or the Cleaning level was set to No Cleaning), an alert window prompts you to select actions for those files. Select actions for the files (actions are set individually for each file in the list) and then click Finish.
Deleting files in archives
In Default cleaning mode, the entire archive will be deleted only if it contains only infected files and no clean files. In other words, archives are not deleted if they also contain harmless clean files. Be careful when performing a Strict cleaning scan. With Strict cleaning enabled, an archive will be deleted if it contains at least one infected file, regardless of the status of other files in the archive.