Identity Provider Connector (IdP Connector)
Some online services (also known as "service providers") allow you to log in using third-party online services (also known as "identity providers").
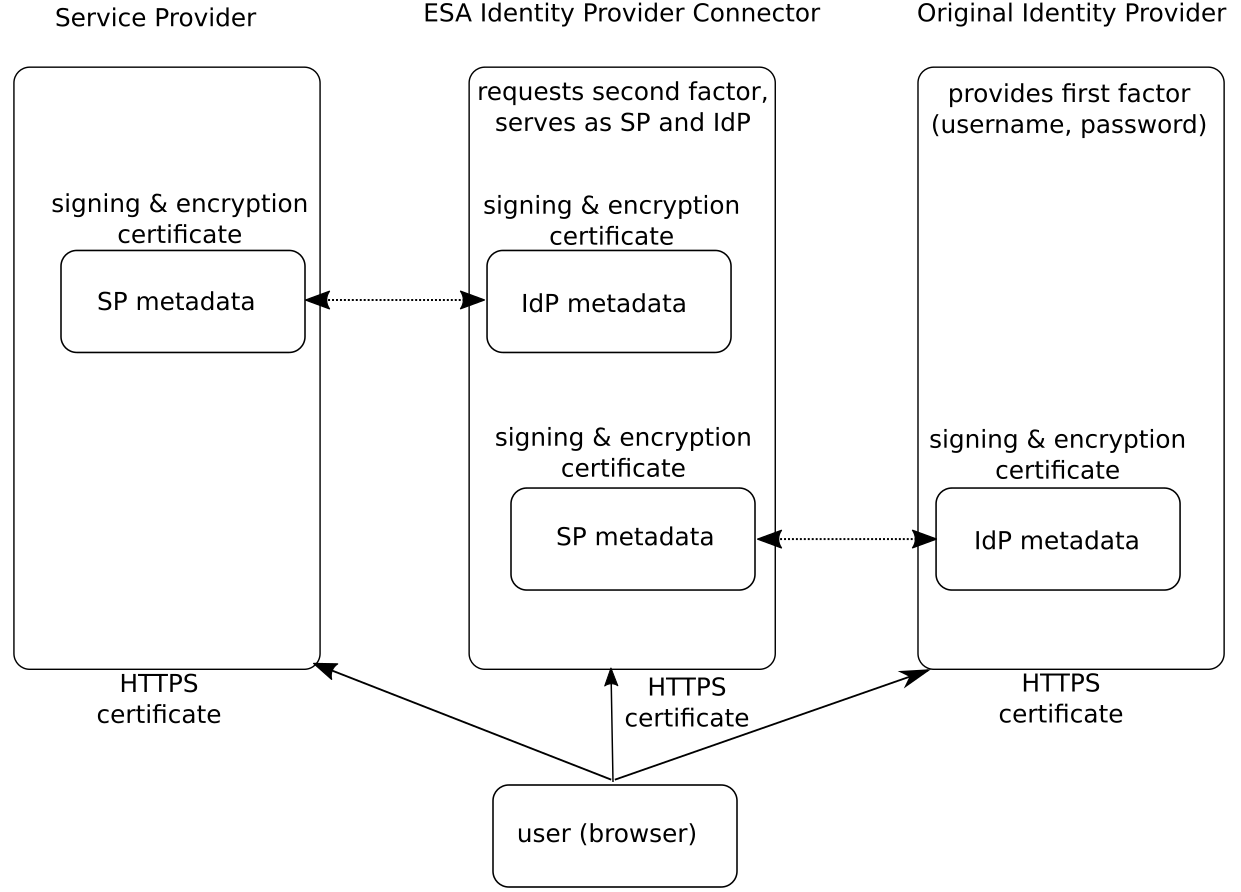
Identity Provider Connector (IdP Connector) of ESA enables adding Two-Factor Authentication between any cloud service (service provider) and identity providers, which use SAML standard.
Service and Identity Provider using SAML standard
1.There is always a Service Provider (SP) and an Identity Provider (IdP), and they need to know about each other. For example, the SP needs to know the metadata URL of the IdP and vice versa.
2.The user goes to the SP to log in but is redirected to the IdP.
3.After successful login to the IdP, the user is redirected back to the SP with signed information about their identity.
4.The SP verifies the signature and then reads the user information, also called "claims".
Some services (SP, IdP) provide their configuration (URLs, certificate details) as SAML metadata file.
When ESA IdP Connector is implemented between a service provider and identity provider (later called "original identity provider"), the communication roles are as follows:
•The Service Provider (SP) uses ESA IdP Connector as the identity provider (IdP)
•The original IdP uses ESA IdP Connector as the SP
•ESA IdP Connector handles the request from the SP and contacts the original IdP to verify the first factor
•ESA IdP Connector provides 2FA interface to verify the second factor
Requirements
•ESA Identity Provider Connector (ESA IdP Connector) installed
•Identity provider (IdP) and Service provider (SP), both using SAML standard
•All certificates involved in the communication (signing certificate, decryption certificate, SSL certificate) must be valid
Identity providers tested with ESET Secure Authentication
•Okta
Service providers tested with ESET Secure Authentication
Proceed to the configuration of Identity Provider Connector in ESA, or see our configuration examples.