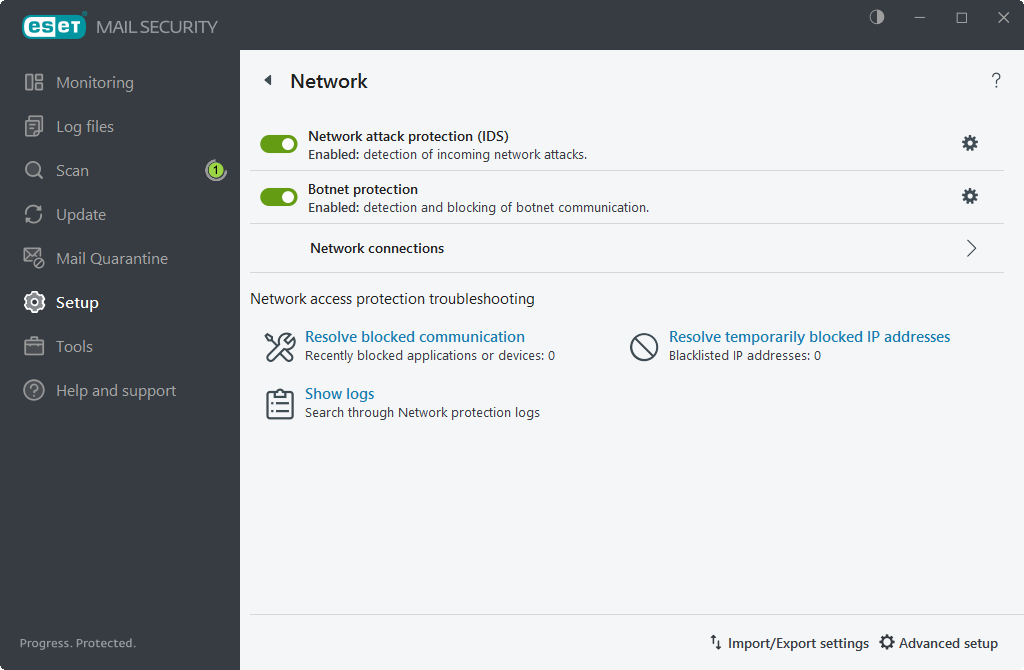
Network
This is accomplished by allowing or denying individual network connections based on your filtering rules. It provides protection against attacks from remote computers and blocks some potentially dangerous services.
The Network module allows you to enable/disable and configure the following components:
Network attack protection (IDS)
Analyzes the content of network traffic and protects from network attacks. Traffic that is considered harmful will be blocked.
Botnet protection
Detection and blocking of Botnet communication. Quickly and accurately identifies malware in the system.
Temporary IP address blacklist (blocked addresses)
View a list of IP addresses that have been detected as the source of attacks and added to the blacklist to block connection for a certain period of time.
Shows the networks where network adapters are connected with detailed information.
Network access protection troubleshooting
Helps you resolve connectivity problems caused by network attack protection.
Resolve temporarily blocked IP addresses
Shows a list of IP addresses detected as the source of attacks and added to the blacklist to block connections for a certain period.
Show logs
A thorough analysis of this data can help detect attempts to compromise system security. Many other factors indicate potential security risks and enable you to minimize their impact: frequent connections from unknown locations, multiple attempts to establish connections, unknown applications communicating or unusual port numbers used.