SPF and DKIM
Sender Policy Framework (SPF) and DomainKeys Identified Mail (DKIM) are validation methods that check incoming email messages from specific domains are authorized by the owner of that domain. This helps protect recipients from receiving spoofed email messages. ESET Mail Security also uses Domain-based Message Authentication, Reporting and Conformance (DMARC) evaluation to enhance SPF and DKIM.
SPF
An SPF check verifies that an email was sent by a legitimate sender. A DNS lookup for SPF records of the sender's domain is performed to get a list of IP addresses. If any of the IP addresses from SPF records matches the actual IP address of the sender, the result of the SPF check is a Pass. If the sender's IP address does not match, the result is a Fail. However, not all domains have SPF records specified in DNS. If there are no SPF records present in DNS, the result is Not available. A DNS request may timeout occasionally, in which case the result is also Not available.
DKIM
DKIM is used by organizations to prevent email message spoofing by adding a digital signature to the headers of outgoing messages according to the DKIM standard. This involves using a private domain key to encrypt your domain's outgoing mail headers and adding a public version of the key to the domain's DNS records. ESET Mail Security can then retrieve the public key to decrypt an incoming header and verify the message comes from your domain and the header has not been changed along the way.
DMARC
DMARC is built on top of the existing SPF and DKIM mechanisms. You can use Mail Transport protection rules to evaluate DMARC result and Apply DMARC policy actions.
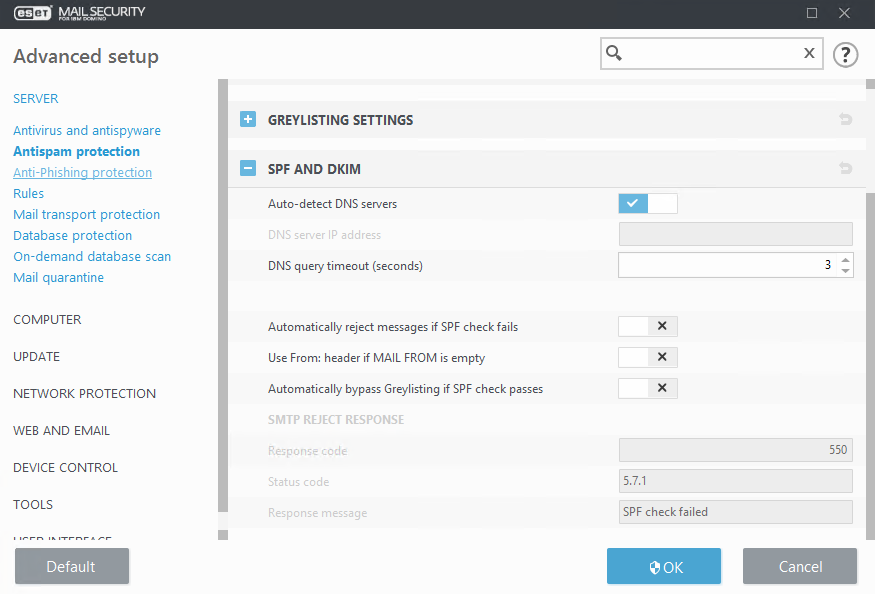
Auto-detect DNS servers
Auto-detect uses your network adapter settings.
DNS server IP address
If you want to use specific DNS servers for SPF and DKIM, type the IP address (in IPv4 or IPv6 format) of the DNS server you want to use.
DNS query timeout (seconds)
Specify a timeout for DNS reply.
Automatically reject messages if SPF check fails
If your SPF check immediately fails, an email message can be rejected before it is downloaded.
The SPF check is done on the SMTP layer. However, it can be rejected either automatically on the SMTP layer or during rules evaluation. Rejected messages cannot be logged into the Events log when you use automatic rejection on the SMTP layer. This is because logging is done by rule action and the automatic reject is done directly on the SMTP layer, which happens before rule evaluation. Because the messages will be rejected before rules are evaluated, there is no information to be logged at the time of rule evaluation. You can log rejected messages only if you reject the messages by a rule action. To reject messages that did not pass SPF check and log such rejected messages, disable Automatically reject messages if SPF check fails and create the following rule for Mail transport protection: Condition •Type: SPF result •Operation: is •Parameter: Failed Actions •Type: Reject message •Type: Log to events |
Use Helo domain in SPF evaluation
This feature uses the HELO domain for SPF evaluation. If the HELO domain is not specified, the computer hostname is used instead.
Use From: header if MAIL FROM is empty
The header MAIL FROM can be empty, and can also be easily spoofed. When this option is enabled and MAIL FROM is empty, the message is downloaded and the header From: is used instead.
Automatically bypass Greylisting if SPF check passes
There is no reason to use Greylisting for a message if its SPF check result was Pass.
SMTP reject response
You can specify a Response code, Status code and Response message, which define the SMTP temporary denial response sent to the SMTP server if a message is refused. You can type a response message in the following format:
Response code |
Status code |
Response message |
|---|---|---|
550 |
5.7.1 |
SPF check failed |