Results of analysis
After a file is analyzed, the ESET cloud sends it to the ESET management console (or ESET Cloud Office Security), where the status of the analyzed file updates from Unknown to one of the statuses listed below. You can view the file information and short results of the analysis in the File details window.
ESET Cloud Office Security users can find the list of submitted files and their results in the Logs section.
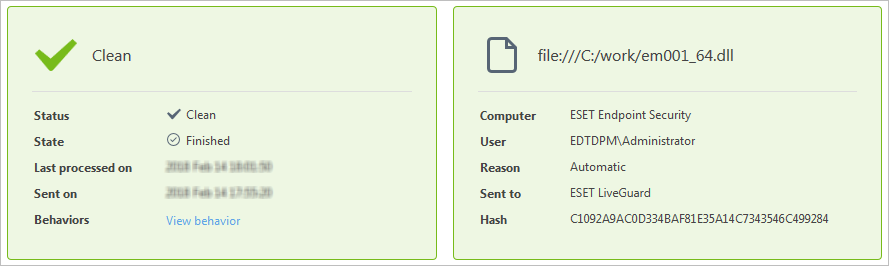
File parameters |
Description |
|---|---|
Computer |
Name of the computer that submitted the file. |
User |
User on the source computer that submitted the file. In some cases, this can be a system user. |
Reason |
Reason for submission (Automatic, Manual). |
Sent to |
Part of the the ESET cloud that received the file. |
Hash |
SHA-1 and SHA-256 hash of the submitted file. |
Filename |
Filename and its full path in the submitter's file system. |
Size |
Size of the file. |
Category |
Category (file type) of the file. Category is used in submission configuration. |
Each sample has two key parameters: State and Status.
The State parameter expresses the current stage in the analysis workflow.
State |
Description |
|---|---|
Sent to LiveGrid® |
The file has been sent to the ESET cloud, but the result will not be available. |
Sent to ESET LiveGuard |
The file has been sent to the ESET cloud for ESET LiveGuard Advanced analysis. |
Analyzing |
The analysis is in progress. |
Finished |
The file has been successfully analyzed. |
Re-analyzing |
The prior result is available, but the file is undergoing analysis again. |
The Status parameter expresses the result of the behavioral analysis or the absence of a result.
Icon |
Status |
Score |
Description |
|---|---|---|---|
|
Unknown |
|
The file has not been analyzed. |
|
Clean |
1–74 |
No detection engine identifies the sample as malicious. |
|
Suspicious Highly suspicious |
75–89 90–99 |
The detection engine has evaluated the file behavior as suspicious but not as clearly malicious. |
|
Malicious |
100 |
The file behavior is considered malicious. |
Recommendations for users with suspicious samples
If your file is evaluated as suspicious or highly suspicious, you should consider the following:
•If your license allows it, inspect the behavioral report for details on the file activities.
•Inspect the source of the file (where the file came from). Do you trust it?
•Upload the file to an external virus analysis tool, for example, VirusTotal.
•If you consider your organization to be at a high risk of an attack, set the Detection threshold to Suspicious.