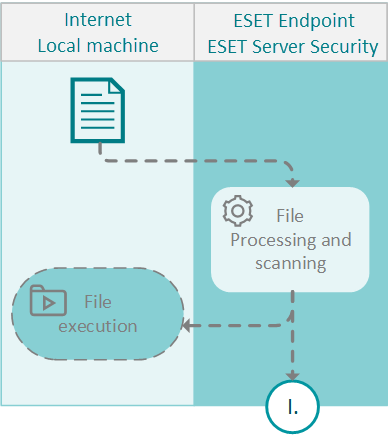
ESET Endpoint Security and ESET Server Security
Each file detected by ESET LiveGuard Advanced within ESET Endpoint Security or ESET Server Security follows the submission process shown below. Use your policy settings to define security levels and cleaning actions for groups or single machines.
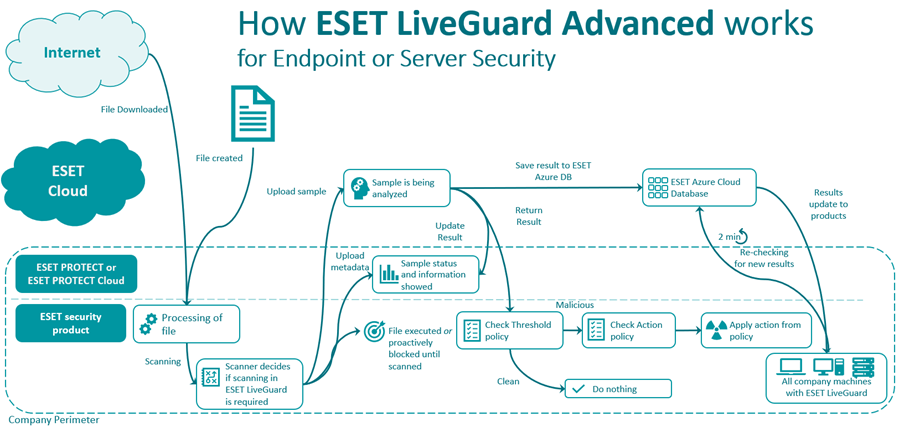
The file analysis follows a four-step process:
1. File scanning
The file is downloaded from the internet, copied to the computer or created. Your ESET security product processes and scans the file.
2. File analysis
If the ESET product decides the file needs to be analyzed, it sends it for analysis. Four separate detection layers process the file and provide a result. The result is reported to ESET PROTECT On-Prem. If the analysis is not needed, the process ends.
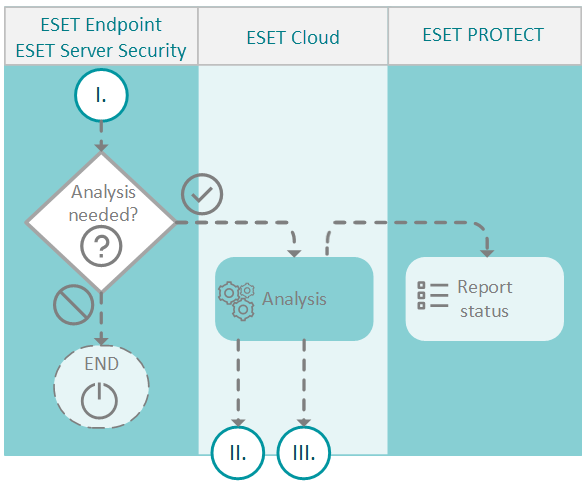
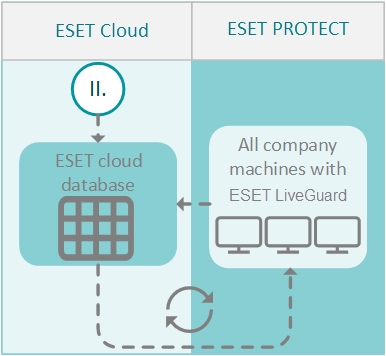
3. Analysis results are shared
The analysis results are saved to a database in the ESET cloud. The database is synchronized every two minutes with ESET PROTECT On-Prem. All machines where ESET LiveGuard Advanced is active have up-to-date information from the ESET cloud.
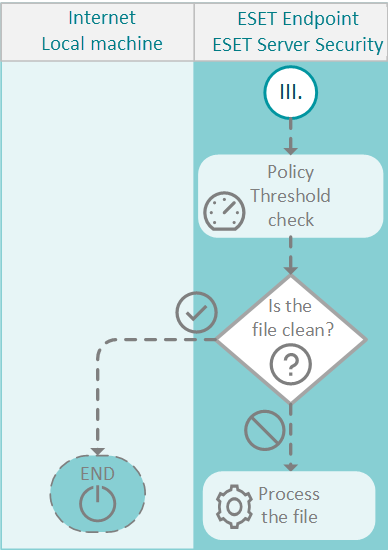
4. Evaluate local policy
The analysis results are also sent back to your ESET security product. Your ESET security product chooses whether to take no action, clean or delete the file based on the cleaning settings defined in your security policy. If the file was blocked and examined during the installation, restart the installation.
•The detection threshold is set in your ESET Endpoint Security / ESET Server Security policy under Protections (for endpoints) or Detection engine (for servers) > Cloud-based protection > ESET LiveGuard Advanced > Detection threshold
•The action taken after a threat is detected is set in your ESET Endpoint Security / ESET Server Security policy under Detection engine > Cloud-based protection > ESET LiveGuard Advanced > Action after detection
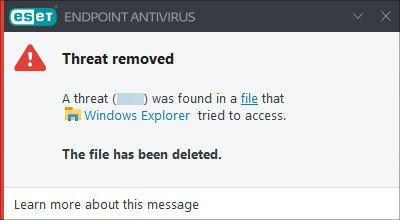
Notification example If ESET LiveGuard Advanced evaluates a file as not clean, ESET Endpoint Security executes the cleaning action. The system displays the following notification to a user after deleting the file:
|