ESET Log Collector User interface
After you have downloaded ESET Log Collector from the ESET website, launch the ESET Log Collector. When you accept the End User License Agreement (EULA), ESET Log Collector will open. If you choose not to accept the terms in the End User License Agreement (EULA), click Cancel, and ESET Log Collector will not open.
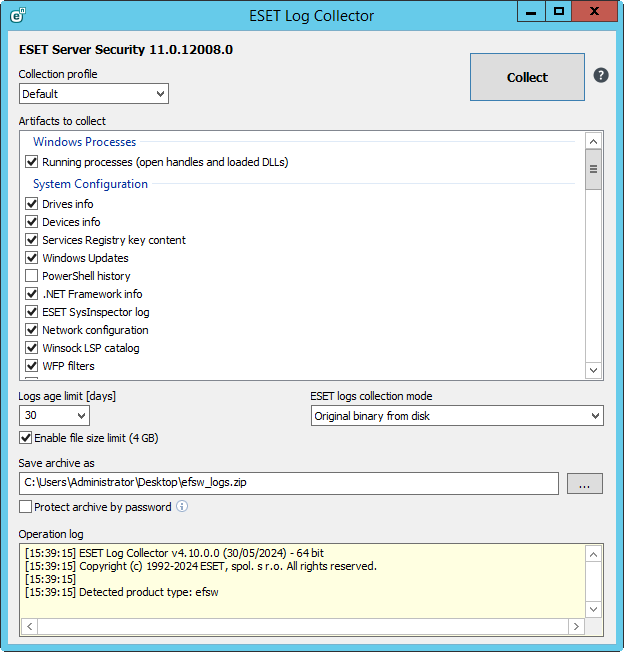
You can choose a Collection profile or make your own artifact selection. A collection profile is a defined set of artifacts:
•Default—A default profile with most of the artifacts selected. It is used for generic support cases. (See the List of artifacts section for a detailed list of selected artifacts).
•Threat detection—Overlaps with the Default profile in many artifacts. Still, in contrast to the Default profile, the Threat detection profile focuses on collecting artifacts that help resolve malware detection-related support cases. (See the List of artifacts section for a detailed list of selected artifacts).
•All—Selects all available artifacts.
•None—Deselects all artifacts and allows you to select the appropriate check boxes for the logs that you want to collect.
•Custom—This collection profile is switched to automatically when you make a change to a previously chosen profile and your current combination of selected artifacts does not fit any of the above mentioned profiles.
The list of displayed artifacts that can be collected changes depending on the detected type of ESET security product installed on your system, your system configuration, as well as other software such as Microsoft Server applications. Only relevant artifacts are available. |
Select the Logs age limit [days] and ESET logs collection mode (default option is Filtered binary).
Use the Enable file size limit (4GB) check box to disable or enable the limit for files that are being collected. Any file larger than 4GB is skipped, and information about skipped files is written into the log.
ESET logs collection mode:
•Filtered binary—Records are filtered by the number of days specified by Logs age limit [days], which means that only records for the last number of days will be collected.
•Original binary from disk—Copies ESET binary log files ignoring Logs age limit [days] value for ESET logs to collect all records regardless of age. However, the age limit still applies to non-ESET logs, such as Windows Event Logs, Microsoft SharePoint logs or Domino logs.
Save archive as – You can specify where to save archive files and click Save. The archive filename is already pre-defined. Click Collect. The application's operation can be interrupted anytime during the processing by pressing the same button – the button's caption changes to Cancel during processing. Success or failure is indicated by a notification message. In case of failure, the log panel contains additional error information.
Protect archive by password – Use the check box to activate password protection, for example, when Gmail blocks sending archive file containing collected logs. Sending password-protected ZIP file prevents Gmail from interfering.
If ESET SysInspector is not present on your machine and you click Collect, you will be asked whether you want to download ESET SysInspector. If you do not want to collect ESET SysInspector log, use the check box to deselect it.
During the collection, you can view the operation log window at the bottom to see what operation is currently in progress. When collection is finished, all the collected and archived data will be displayed. This means that collection was successful and the archive file (for example, emsx_logs.zip, ees_logs.zip or eea_logs.zip) has been saved in the specified location. (See the List of artifacts section for detailed information).