Add or Edit detection exclusion
Exclude detection
A valid ESET detection name should be provided. For a valid detection name, see Log files and then select Detections from the Log files drop-down menu. This is useful when a false positive sample is being detected in ESET Endpoint Security. Exclusions for real infiltrations are very dangerous, consider excluding only affected files / directories by clicking ... in the Path field and/or only for a temporary period of time. Exclusions apply also to Potentially unwanted applications, potentially unsafe applications and suspicious applications.
See also Path exclusion format.
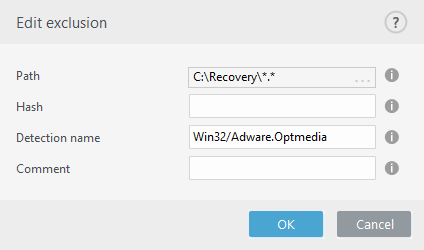
See the Detection exclusions example below.
Exclude hash
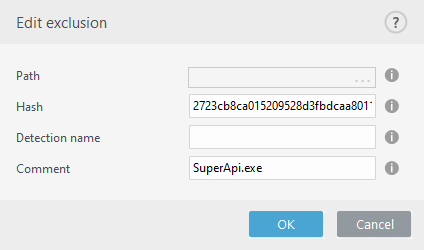
Excludes a file based on a specified SHA-1 hash, regardless of the file type, location, name, or extension.
Control elements
•Add – Excludes objects from detection.
•Edit – Enables you to edit selected entries.
•Delete – Removes selected entries (CTRL + click to select multiple entries).
