Network configurations
ESET Endpoint Encryption Server Usage Configurations
The ESET Endpoint Encryption Server (EEE Server) can be configured to operate in several ways to suit your organizational requirements. Any off-site or cloud-based data is always encrypted, as are the communications between the EEE Server and the client.
Standard Configuration
This configuration is the default recommended configuration. Client machines need an outgoing connection to the internet, over HTTPS, to connect to our cloud proxy server. They need this connection to receive updates; it is not necessary for normal use. The EEE Server needs an outgoing internet connection to our cloud proxy and licensing servers to post updates and license new users. The EEE Server does not need to be running continuously for client PCs to operate. As long as you have basic outgoing internet access to receive updates, there is no need to configure port forwarding, reconfigure firewalls, or maintain SSL certificates.
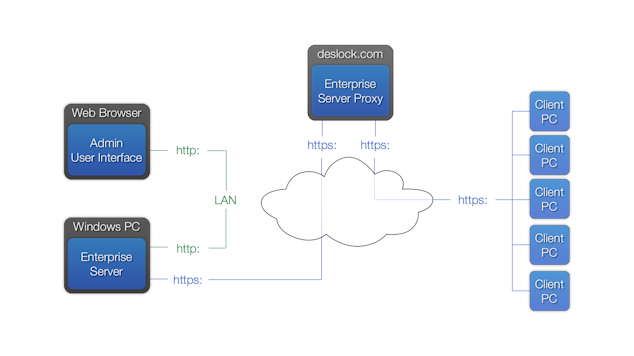
There are four essential components in the system:
•Admin User Interface - This is the administration front end, accessed by a web browser from any PC with a local area connection to the EEE Server itself. As an Administrator, you can use the EEE Server package from any location that has access to the PC/Server that is hosting the software. The web browser can be on any PC, even a client PC, or the EEE Server PC.
•ESET Endpoint Encryption Server - The main system database containing the details accessed by the admin user interface. This also controls the communication with the server proxy. This must be installed on a Windows-based computer, satisfying the minimum system requirements (Windows 10 or Windows Server 2012).
•ESET Endpoint Encryption Server Cloud Proxy - the communications interface between the EEE Server and the client PCs. All data on the server proxy is encrypted. The server may be physically on your site or a remote system in the 'cloud'.
•Client PC - The user's workstation. Multiple users can use the same machine, each with a different account and different encryption keys. Client PC's can be based anywhere with access to the server proxy. Depending on network organization, the client may have LAN or internet access.
The standard configuration uses our cloud-based server proxy for secure communications. The components are the four outlined above.
There are no differences between the Performance, Security or Reliability of the other configurations; they are included purely to give you possible setup scenarios.
After you decide on your network configuration (which elements of the supplied software you will use, or which of your own), proceed to the Software Installation.