HIPS - Host-based Intrusion Prevention System
Changes to HIPS settings should only be made by an experienced user. Incorrect configuration of HIPS settings can lead to system instability. |
The Host-based Intrusion Prevention System (HIPS) protects your system from malware and unwanted activity attempting to negatively affect your computer. HIPS utilizes advanced behavioral analysis coupled with the detection capabilities of network filtering to monitor running processes, files and registry keys. HIPS is separate from Real-time file system protection and is not a firewall; it only monitors processes running within the operating system.
You can configure HIPS settings in Advanced setup > Protections > HIPS > Host Intrusion Prevention System. The HIPS state (enabled/disabled) is shown in the ESET Endpoint Antivirus main program window > Setup > Computer.
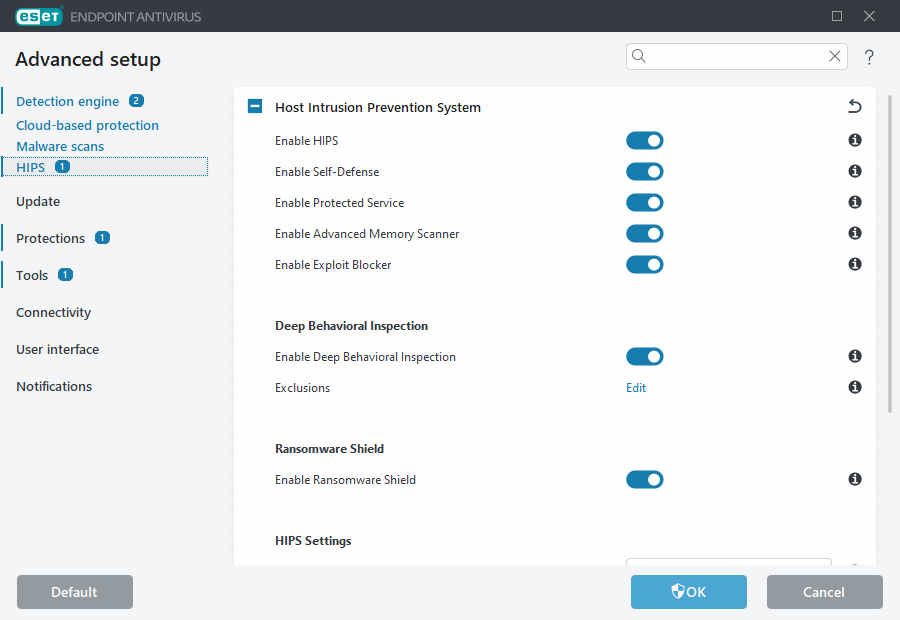
Host Intrusion Prevention System
Enable HIPS—HIPS is enabled by default in ESET Endpoint Antivirus. Turning off HIPS will disable rest of the HIPS features like Exploit Blocker.
Drivers always allowed to load—Listed drivers are always allowed to load regardless of configured filtering mode unless explicitly blocked by user rule.
Enable Advanced Memory Scanner—Works in combination with Exploit Blocker to strengthen protection against malware that has been designed to evade detection by antimalware products through the use of obfuscation or encryption. Advanced memory scanner is enabled by default. Read more about this type of protection in the glossary.
Enable Exploit Blocker—Designed to fortify commonly exploited application types such as web browsers, PDF readers, email clients and Microsoft Office components. Exploit blocker is enabled by default. Read more about this type of protection in the glossary.
Filtering mode can be performed in one of the following modes:
Description |
|
|---|---|
Automatic mode |
Operations are enabled with the exception of those blocked by pre-defined rules that protect your system. |
Smart mode |
The user will only be notified about very suspicious events. |
Interactive mode |
User will be prompted to confirm operations. |
Policy-based mode |
Blocks all operations that are not defined by a specific rule that allows them. |
Learning mode |
Operations are enabled and a rule is created after each operation. Rules created in this mode can be viewed in the HIPS rules editor, but their priority is lower than the priority of rules created manually or rules created in automatic mode. When you select Learning mode from the Filtering mode drop down menu, the Learning mode will end at setting will become available. Select the time span that you want to engage learning mode for, the maximum duration is 14 days. When the specified duration has passed, you will be prompted to edit the rules created by HIPS while it was in learning mode. You can also choose a different filtering mode, or postpone the decision and continue using learning mode. |
Mode set after learning mode expiration—Select the filtering mode that will be used after learning mode expires. After expiration, the Ask user option requires administrative privileges to perform a change to the HIPS filtering mode.
The HIPS system monitors events inside the operating system and reacts accordingly based on rules similar to those used by the Firewall. Click Edit next to Rules to open the HIPS rules editor. In the HIPS rules window you can select, add, edit or remove rules. More details on rule creation and HIPS operations can be found in Edit a HIPS rule.
Log all blocked operations—All blocked operations will be written to the HIPS log. Use this feature only when troubleshooting or requested by ESET Technical Support, as it might generate a huge log file and slow down your computer.
Notify when changes occur in Startup applications—Displays a desktop notification each time an application is added to or removed from system startup.
Self-Defense
Enable Self-Defense—ESET Endpoint Antivirus uses the built-in Self-defense technology as a part of HIPS to prevent malicious software from corrupting or disabling your antivirus and antispyware protection. Self-defense protects crucial system and ESET's processes, registry keys and files from being tampered with. ESET Management Agent is protected as well when installed.
Enable Protected Service—Enables protection for ESET Service (ekrn.exe). When enabled, the service is started as a protected Windows process to defend attacks by malware. This option is available in Windows 8.1 and Windows 10.
Deep Behavioral Inspection
Enable Deep Behavioral Inspection—Another layer of protection that works as a part of the HIPS feature. This extension of HIPS analyzes the behavior of all programs running on the computer and warns you if the behavior of the process is malicious.
HIPS exclusions from Deep Behavioral Inspection—Enables you to exclude processes from analysis. To ensure that all processes are scanned for possible threats, we recommend only creating exclusions when it is absolutely necessary.
Ransomware Shield
Enable Ransomware Shield—Another layer of protection that works as a part of HIPS feature. You must have the ESET LiveGrid® reputation system enabled for Ransomware shield to work. Read more about this type of protection.
Enable Intel® Threat Detection Technology—Helps to detect ransomware attacks by utilizing unique Intel CPU telemetry to increase detection efficacy, lower false positive alerts, and expand visibility to catch advanced evasion techniques. See the supported processors.
Enable Ransomware Shield Audit mode—Everything detected by the Ransomware shield is not automatically blocked, but logged with a warning severity and sent to the management console with the "AUDIT MODE" flag. Administrator can either decide to exclude such detection to prevent further detection, or keep it active, which means that after Audit mode ends, it will be blocked and removed. Enabling/disabling the Audit mode will also be logged in ESET Endpoint Antivirus. This option is available only in the ESET PROTECT On-Prem policy configuration editor.
Ransomware Remediation
Restore files after a ransomware attack—This feature is enabled by default. It improves Ransomware Shield protection by performing a backup on documents and eventually restoring encrypted files after detection.
List of excluded folders—You can exclude specific folders from being backed up. The path must end with the backslash (\) and asterisk (*) to indicate that it is a folder and that all folder content (files and subfolders) will be excluded. For more information on exclusion format, see Performance exclusions.
List of protected file types—You can add the file types or edit the existing list of file types commonly secured and monitored.
When you initiate the backup process, the system verifies and starts the process on the NTFS-formatted hard drive only. |
When a backup is created, the backed-up files are copied to the drive where ESET Endpoint Antivirus is installed. |
For additional information, read Ransomware Remediation. |