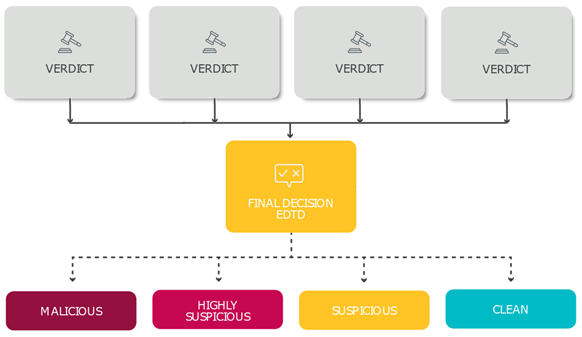
How detection layers work
ESET LiveGuard Advanced uses four separate detection layers to ensure the highest detection rate. Each layer uses a different approach and gives its verdict over the sample. The final assessment is the result of all information about the sample. See the overview of the process in the scheme below:
Click the image for the full-size picture.
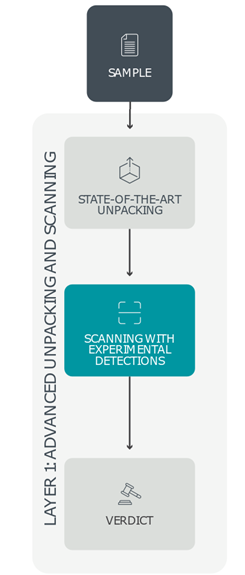
Layer 1: Advanced unpacking and scanning
After entering the initial layer of ESET LiveGuard Advanced—the so-called Advanced unpacking and scanning layer—static samples are matched against ESET’s threat database: enriched with experimental and yet to be distributed detections as well as against a comprehensive list of clean, potentially unwanted (PUA), and potentially unsafe (PUsA) items. Malware often tries to thwart detection by hiding its malicious core behind a range of packing layers; thus, this coating must be removed for proper analysis. ESET LiveGuard Advanced uses Advanced unpacking and scanning to achieve this by utilizing highly specialized tools based on packers that ESET researchers have found in malicious code. These specialized unpackers peel away malware’s protective layer, allowing ESET LiveGuard Advanced to match the sample against the enriched threat database again. The Advanced unpacking and scanning layer classifies the sample as malware, clean, PUA, or PUsA. Due to security risks and hardware demands associated with the unpackers and other incorporated procedures, a high-performance and secure environment are required. This unique environment is provided by ESET LiveGuard Advanced’s robust and resilient cloud infrastructure.
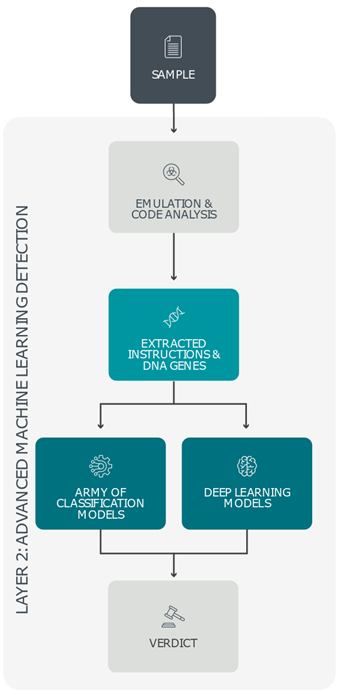
Layer 2: Advanced Machine Learning detection
Each item submitted to ESET LiveGuard Advanced is also subject to static analysis via Advanced Machine Learning detection, producing basic characteristics of the sample. As analyzing compressed or encrypted code with no further processing would only attempt to classify noise, the submitted item simultaneously undergoes another more dynamic analysis that extracts its instructions and DNA genes. By describing a sample’s active features and behaviors, malicious characteristics of packed or obfuscated objects are uncovered even without executing it. Information extracted from all previous steps is further processed by a small army of carefully chosen classification models and deep learning algorithms. Finally, all this information is consolidated via a neural network that returns one of four probability levels – malicious, highly suspicious, suspicious, and clean. If this or any other ESET LiveGuard Advanced layer is not used, an “analysis not needed” message is displayed. Due to these procedures' complexity and hardware demands, a significantly more powerful infrastructure than the one provided by a user’s endpoint is necessary. ESET engineers devised a superior and complex set of systems to handle the computation-heavy tasks – ESET LiveGuard Advanced.
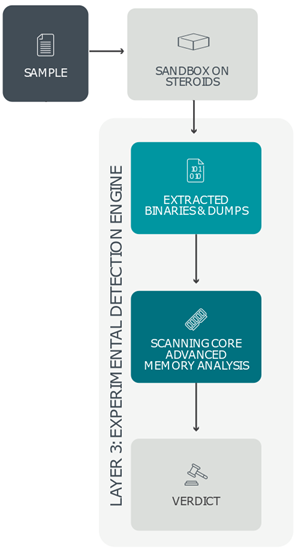
Layer 3: Experimental detection engine
To further analyze each sample, a deeper and behavior-focused analysis is necessary to complement the previous findings. To gather this type of threat intelligence, another ESET LiveGuard Advanced layer steps in – namely, the Experimental detection engine. It inserts the suspicious item into a set of precisely configured systems that resemble full-scale machines using various operating systems – a kind of “sandbox on steroids”. These highly controlled environments serve as monitoring cells fitted with a legion of ESET’s detection algorithms logging every action. To identify hidden malicious behavior, the Experimental detection engine also produces a large quantity of memory dumps. These are subsequently scanned and matched against ESET’s enriched threat database that incorporates unpublished and experimental detections, ensuring highly accurate detection results and an extremely low number of false positives. Intelligence gathered by the Experimental detection engine is also compiled into a comprehensive list of events detected by the sandbox, which is then used for further analysis in the final ESET LiveGuard Advanced detection layer – In-Depth Behavioral Analysis.
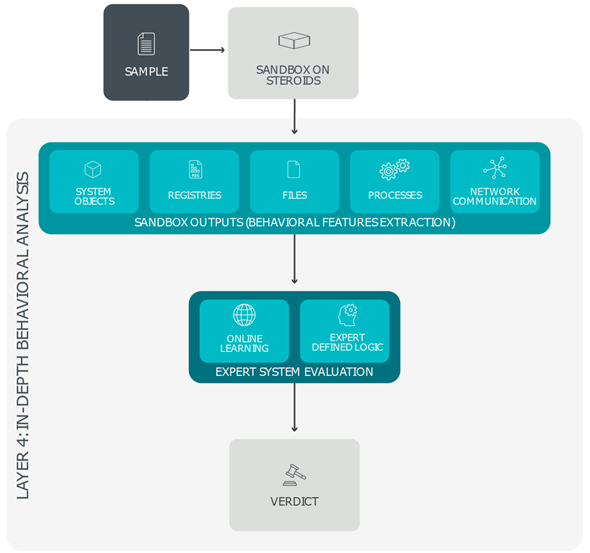
Layer 4: In-Depth Behavioral Analysis
In the final ESET LiveGuard Advanced layer, known as In-Depth Behavioral Analysis, all sandbox outputs – including files created or deleted on the hard-drive, entries added to or removed from the Windows system registry, all external communication attempts, and scripts that are being run – are subject to a thorough behavioral analysis. In this stage, ESET LiveGuard Advanced focuses on malicious and suspicious actions such as attempted connections to web locations with bad reputations, use of known malicious objects, and use of unique strings generated by specific malware families. In-Depth Behavioral Analysis also breaks up the sandbox outputs into logical blocks, which are then matched against an extensive and periodically reviewed database of previously analyzed patterns and chains of actions to identify even the slightest indication of malicious behavior.
Final result
ESET LiveGuard Advanced combines all available verdicts from the detection layers and evaluates the sample's status. The result is delivered to the user's ESET security product and their company's infrastructure first.