Create a Policy for MDC to activate APN/ABM for iOS enrollment
When changing the https certificate used in your policy for MDC, follow the steps below to avoid disconnecting mobile devices from your MDM: 1. Create and apply the new policy that uses the new https certificate. 2. Allow devices to check in to the MDM server and receive the new policy. 3. Verify that devices are using the new https certificate (the https certificate exchange is completed). 4. Allow at least 72 hours for your devices to receive the new policy. After all devices have received the new policy (MDM Core alert "HTTPS certificate change still in progress. The old certificate is still being used " is no longer displayed in the Alerts tab), you can delete the old policy. |
This is an example of how to create a new policy for ESET Mobile Device Connector to activate APNS (Apple Push Notification Services) and iOS Device Enrollment Program feature. This is required for iOS device Enrollment. Before configuring this policy, create a new APN certificate and have it signed by Apple on the Apple Push Certificates Portal so that it becomes a signed certificate or APNS Certificate. For step-by-step instructions, see the APN certificate section.
Basic
Type in a Name for this policy. The Description field is optional.
Settings
Select ESET Mobile Device Connector from the drop-down list.
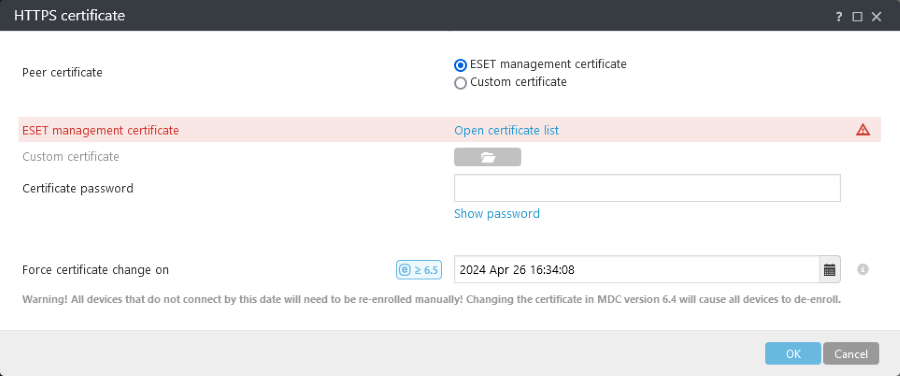
If you installed MDM Server with All-in-One Installer (Not as a standalone and not as a component), the HTTPS certificate was generated automatically during the installation. For all other cases, you need to apply a custom HTTPS certificate. You can find more information annotated following step one of Mobile Device Management topic. You can use the ESET PROTECT certificate (signed by ESET PROTECT On-Prem CA) or your custom certificate. You can also specify the date for Force certificate change. Click the tooltip next to this setting for more information. |
Type your actual organization's name over the Organization string. This is used by the enrollment profile generator to include this information in the profile. |
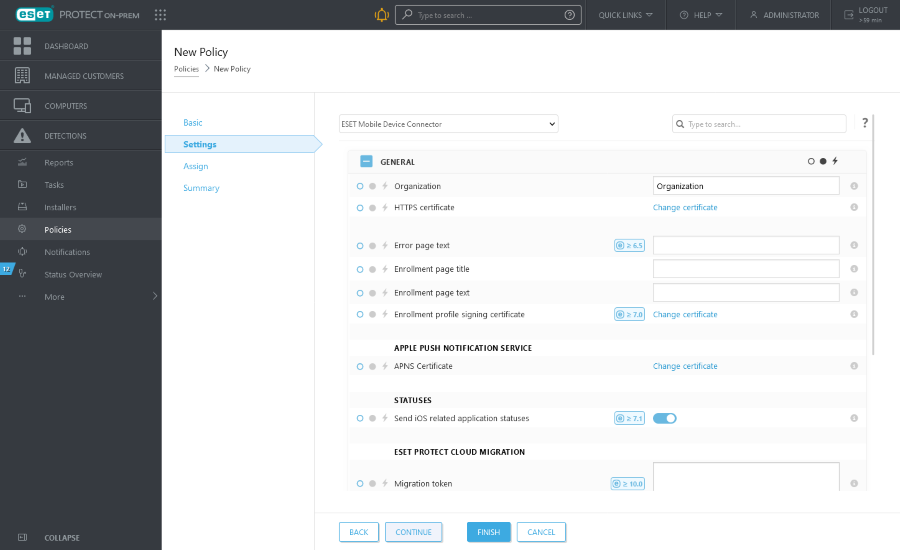
Under ![]() General, you can optionally upload your HTTPS certificate for enrollment into the Enrollment profile signing certificate (this affects only non-ABM enrollment). This will allow the enrollment page for iOS devices they visit during enrollment process to be signed and that they will be visible in the Signed by filed based on the certificate.
General, you can optionally upload your HTTPS certificate for enrollment into the Enrollment profile signing certificate (this affects only non-ABM enrollment). This will allow the enrollment page for iOS devices they visit during enrollment process to be signed and that they will be visible in the Signed by filed based on the certificate.
Upload the Apple certificates for iOS enrollment – navigate to the Apple Push Notification Service and upload the APNS Certificate and a APNS Private Key.
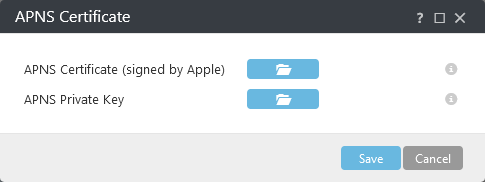
APNS Certificate (signed by Apple) - click the folder icon and browse for the APNS Certificate to upload it. The APNS Certificate is the file you downloaded from Apple Push Certificates Portal.
APNS Private Key - click the folder icon and browse for the APNS Private Key to upload it. The APNS Private Key is the file you downloaded during APN/ABM Certificate creation.
Product Improvement Program - Enable or disable transmission of crash reports and anonymous telemetry data to ESET.
Trace log verbosity - Set the log verbosity to determine the level of information that will be collected and logged, from Trace (informational) to Fatal (most important critical information).
If you are creating this policy for iOS enrollment with Apple ABM, navigate to the ![]() Apple Business Manager (ABM).
Apple Business Manager (ABM).
![]() Apple Business Manager (ABM) - these settings are ABM-only.
Apple Business Manager (ABM) - these settings are ABM-only.![]()
After the initial configuration, if any of these settings will be changed, to apply the changes, you will need to factory-reset and re-enroll all the affected iOS devices. |
Upload authorization token - click the folder icon and browse for the ABM server token. The ABM server token is the file you downloaded when you created the virtual MDM server on the Apple ABM portal.
Mandatory Installation - the user will not be able to use the device without installing the MDM profile.
Allow user to remove MDM profile - device must be in supervised mode to prevent the user from removing the MDM profile.
Require domain login - user must use valid domain credentials in the device Setup Wizard.
Skip Setup Items - this setting allows you to choose which of the initial setup steps during the initial iOS setup will be skipped. You can find more information about each of these steps in the Apple Knowledgebase Article.
Assign
Select the device that is hosting the MDM server the policy is targeted on.
Click Assign to display all Static and Dynamic Groups and their members. Select the Mobile Device Connector instance that you want to apply the policy on and click OK.
Summary
Review the settings for this policy and click Finish.
