Botnet feed
The botnet feed shares all the data ESET has about the Botnet network. The feed consists of three types of feeds (botnet, cc, and target). Each feed contains different information.
ei.botnet
Below is a description of some attributes of the ei.botnet feed.
•Detection—The name of the detection defined by ESET (Win32/TrojanDownloader.Wauchos.CX trojan).
•Hashes—The hash of the detected file (SHA1, MD5, SHA256).
•File_extension—The type of malicious file (.exe, .sys, .dll, script, or unk).
•Used by—The family name of the attacking botnet. This field has the same value as the target field in ei.target (Win32/Dorkbot.H worm).
•Last alive—The timestamp of when ESET was last able to communicate with the server (2015-12-03 13:17:31).
•URIobj type=C2—The link of the Command and Control (CnC) server. This value might be a TOR link also (http://t7yz3cihrrzalznq.onion/assets).
•Config—The SHA-1 hash of the configuration file when downloaded (.ini, .bin).
•URIobj type=target—The targeted link string botnet is attacking (*paypal.*/webscr?cmd=_login-submit*).
•Files downloaded by the main file—These files may be downloaded by the main file. If so, the feed contains the following:
oDetection—The name of the detection defined by ESET.
oHashes (SHA1, MD5, or SHA256)
oType of file (.exe, .sys, .dll, script, or unk)
JSON
Below is a snippet of an ei.botnet feed in JSON format.
<taxii_11:Content>[ { "cncs": [ { "last_alive": "2020-10-16 04:48:55 UTC", "url": "http://www.ruartemoyano.com/xnc/" } ], "file": { "count": 1, "file_name": "PI41006.exe", "file_type": "application/x-dosexec", "first_seen": "2020-10-26 01:52:05 UTC", "md5": "1e5fe47835896ae4bb10a382167cf0f1", "sha1": "742e2b17e6e3c5e90098c401ddbccba339ce4c6f", "sha256": "81c1d78fd9c2c4e78b74976875c7ea0ac39ab5c87f5d1671e203c8c05bce01ca", "size": 363008, "ssdeep": "6144:xVIHTKyfQWoiVcy5iqEQC4V5dHDwsaPWNN2gdG96x9hupaO6Sv:IHRfQni2yHEQC4RHDMWWes6Sv" }, "files": [], "targets": [], "threat": "Win32/Formbook.AA trojan", "valid_to": "2020-10-28 03:10:11 UTC" } ]</taxii_11:Content> |
STIX 2.0
Below is a snippet of an ei.botnet feed in STIX 2.0 format.
<taxii_11:Content>{ "type": "bundle", "id": "bundle--cc0d80d6-183d-4df6-af2f-51972380cbc8", "spec_version": "2.0", "objects": [ { "type": "indicator", "id": "indicator--793b0b72-d349-47b2-a3d8-05b183a71a89", "created": "2020-10-26T03:10:11.000Z", "modified": "2020-10-26T03:10:11.000Z", "name": "Malware variant", "description": "Each of these file hashes indicates that a variant of Win32/Formbook.AA trojan is present.", "pattern": "[file:hashes.'SHA-256'='81c1d78fd9c2c4e78b74976875c7ea0ac39ab5c87f5d1671e203c8c05bce01ca'] OR [file:hashes.'SHA-1'='742e2b17e6e3c5e90098c401ddbccba339ce4c6f'] OR [file:hashes.'MD5'='1e5fe47835896ae4bb10a382167cf0f1']", "valid_from": "2020-10-26T03:10:11Z", "valid_until": "2020-10-28T03:10:11Z", "labels": [ "malicious-activity" ] }, { "type": "malware", "id": "malware--796adca6-3d1a-4432-bb8f-b99796d56151", "created": "2020-10-26T03:10:11.000Z", "modified": "2020-10-26T03:10:11.000Z", "name": "Win32/Formbook.AA trojan", "labels": [ "trojan" ] }, { "type": "relationship", "id": "relationship--7afabbe3-aa6e-4f6e-b9ad-5e39db65ad0c", "created": "2020-10-26T03:10:27.132Z", "modified": "2020-10-26T03:10:27.132Z", "relationship_type": "indicates", "source_ref": "indicator--793b0b72-d349-47b2-a3d8-05b183a71a89", "target_ref": "malware--796adca6-3d1a-4432-bb8f-b99796d56151" }, { "type": "observed-data", "id": "observed-data--5529823a-0da1-4bc9-9b4d-056de663c08a", "created": "2020-10-26T03:10:11.000Z", "modified": "2020-10-26T03:10:11.000Z", "first_observed": "2020-10-26T01:52:05Z", "last_observed": "2020-10-26T03:10:11Z", "number_observed": 1, "objects": { "0": { "type": "file", "hashes": { "MD5": "1e5fe47835896ae4bb10a382167cf0f1", "SHA-1": "742e2b17e6e3c5e90098c401ddbccba339ce4c6f", "SHA-256": "81c1d78fd9c2c4e78b74976875c7ea0ac39ab5c87f5d1671e203c8c05bce01ca", "ssdeep": "6144:xVIHTKyfQWoiVcy5iqEQC4V5dHDwsaPWNN2gdG96x9hupaO6Sv:IHRfQni2yHEQC4RHDMWWes6Sv" }, "size": 363008, "name": "PI41006.exe", "mime_type": "application/x-dosexec" } } }, { "type": "relationship", "id": "relationship--72166c85-d539-4141-98df-fbe61d8450e0", "created": "2020-10-26T03:10:27.132Z", "modified": "2020-10-26T03:10:27.132Z", "relationship_type": "based-on", "source_ref": "indicator--793b0b72-d349-47b2-a3d8-05b183a71a89", "target_ref": "observed-data--5529823a-0da1-4bc9-9b4d-056de663c08a" }, { "type": "observed-data", "id": "observed-data--fe408eb0-bd2e-4a39-94d3-1de5e99e78da", "created": "2020-10-26T03:10:11.000Z", "modified": "2020-10-26T03:10:11.000Z", "first_observed": "2020-10-16T04:48:55Z", "last_observed": "2020-10-16T04:48:55Z", "number_observed": 1, "objects": { "0": { "type": "url", "value": "http://www.ruartemoyano.com/xnc/" } } }, { "type": "relationship", "id": "relationship--db13b6a9-1d22-43d7-83be-8d62b8079afe", "created": "2020-10-26T03:10:27.132Z", "modified": "2020-10-26T03:10:27.132Z", "relationship_type": "related-to", "source_ref": "observed-data--fe408eb0-bd2e-4a39-94d3-1de5e99e78da", "target_ref": "indicator--793b0b72-d349-47b2-a3d8-05b183a71a89" } ] }</taxii_11:Content> |
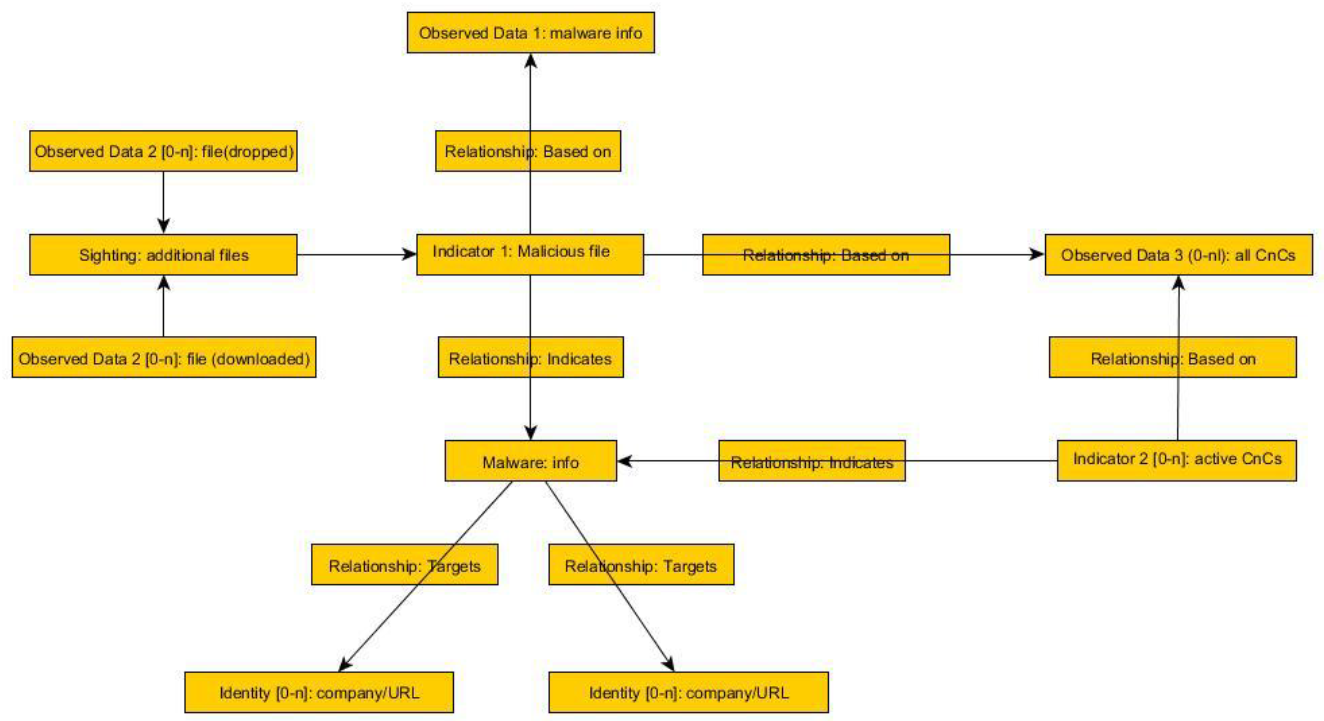
The following types of STIX domain objects are available for the botnet feed:
•Indicator 1—The main Indicator of Comprise (IoC), which is a malicious file that communicates with a CnC server. This object is always present in the feed
•Observed data 1—Additional information about the malicious file.
•Malware—A detection of a malicious botnet file.
•Identity—The targets of the malware obtained from the configuration of the CnC. This object is optional.
•Observed data 2—If a malicious file (IoC 1) creates or downloads additional files, the files will be connected to that file (IoC 1) via Sighting.
•Indicator 2—The secondary IoC tied to IoC 1. This object refers to the link of the CnC server and the associated data. If the last communication with the CnC server through the given link was more than 48 hours ago, Indicator 2 turns to Observed data 3.
•Observed data 3—This object shows all links that were pointing to the CnC server hosting the malware. If the links were active in the last 48 hours, they have a relationship also with Indicator 2.
•Relationship: