Rules
Brute-force attack protection rules enable you to create, edit and view rules for incoming and outgoing network connections. The pre-defined rules cannot be edited or deleted.
Managing Brute-force attack protection rules
Add—Create a new rule.
Edit—Edit an existing rule.
Delete—Remove an existing rule from the list of rules.
![]() Top/Up/Down/Bottom—Adjust the priority level of rules.
Top/Up/Down/Bottom—Adjust the priority level of rules.
To ensure the highest possible protection, the blocking rule with the lowest Max attempts value is applied even if the rule is positioned lower in the Rules list when multiple blocking rules match the detection conditions. |
Rule editor
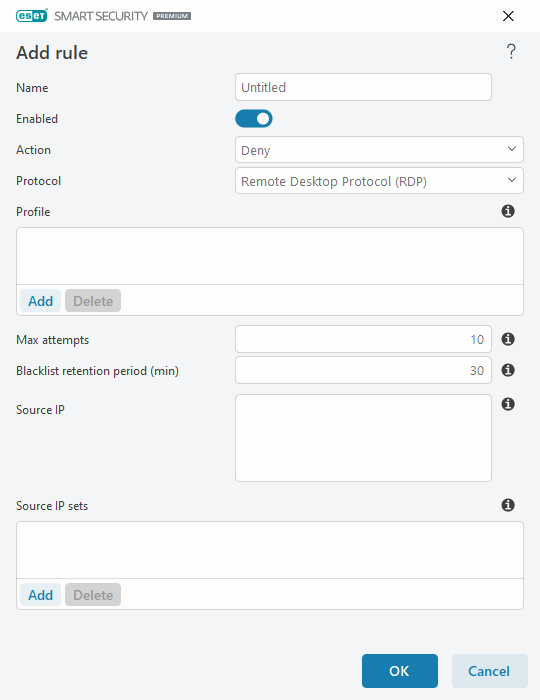
Name—Name of the rule.
Enabled—Disable the toggle if you want to keep the rule in the list but not to apply it.
Action—Choose whether to Deny or Allow the connection if the rule settings are fulfilled.
Protocol—The communication protocol this rule will inspect.
Profile—Custom rules can be set and applied for specific profiles.
Max attempts—The maximum number of allowed attempts of attack repetition until the IP address is blocked and added to the blacklist.
Blacklist retention period (min)—Sets the time for the address expiration from the blacklist.
Source IP—A list of IP addresses/ranges/subnets. Multiple addresses must be separated by a comma.
Source IP sets—Set of IP addresses you have already defined in IP sets.