Detection exclusions
Detection exclusions allow you to exclude objects from cleaning (deletion or moving to quarantine) by filtering the detection name, object path or its hash.
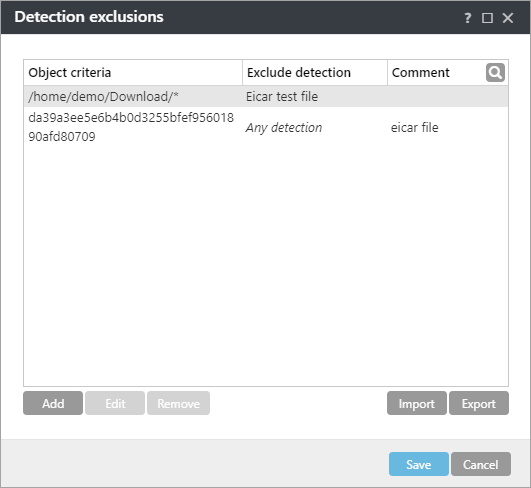
How detection exclusions work Detection exclusions do not exclude files and folders from scanning as Performance exclusions do. Detection exclusions exclude objects from being quarantined/deleted only when they are detected by the detection engine and an appropriate rule is present in the exclusion list. See the sample rules in the image below. The rule in the first row will exclude an object that is detected as Eicar test file and is located at /home/demo/Download/some.file. The rule in the second row will exclude every detected object that has the corresponding SHA-1 hash, regardless the detection name. |
Detection exclusions object criteria
•Path—Detection exclusion for a specified path (or any if left empty)
•Detection name—A detected object will be excluded if it matches the defined detection name. If the file is later infected with other malware, its detection name will change; thus, it will be detected as infiltration, and proper action will be taken against it. If Path is defined, only files located at that path and matching the Detection name will be excluded from detection. To add such detections to the exclusion list, use the detection exclusion wizard. Alternatively, navigate to Quarantine, click a quarantined file, and select Restore and exclude. This option is displayed only for items the detection engine evaluated as eligible for exclusion.
•Hash—Excludes a file based on a specified hash (SHA1 or SHA256), regardless of the file type, location, name, or extension