Establishing connection – detection
The Firewall detects each newly-created network connection. The active firewall mode determines which actions are performed for the new rule. If Automatic mode or Policy-based mode is activated, the Firewall will perform pre-defined actions with no user interaction.
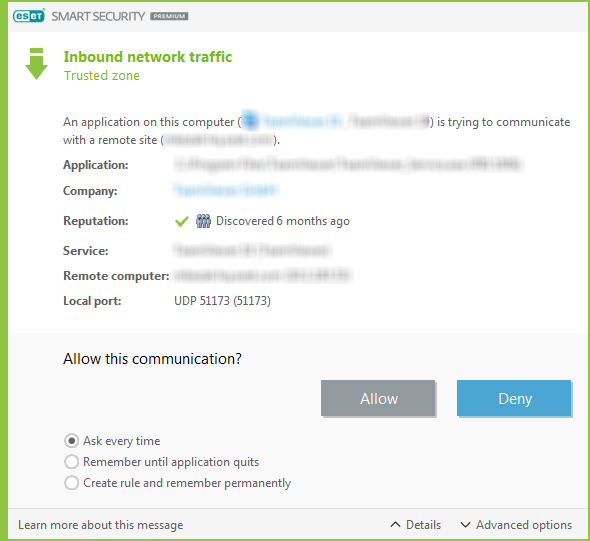
The Interactive mode displays an informational window that reports the detection of a new network connection with detailed information about the connection. You can choose to Allow or Deny (block) the connection. If you repeatedly allow the same connection in the dialog window, we recommend that you create a new rule for the connection.
Select Create rule and remember permanently to save the action as a new rule for the Firewall. If the Firewall recognizes the same connection in the future, it will apply the existing rule without requiring user interaction.
When creating new rules, only allow connections that you know are secure. If all connections are allowed, the Firewall fails to accomplish its purpose. These are the important parameters for connections:
Application—Executable file location and process ID. Do not allow connections for unknown applications and processes.
Signer—Application's publisher name. Click the text to show a security certificate for the company.
Reputation—Risk level of the connection. Connections are assigned a risk level: Fine (green), Unknown (orange) or Risky (red), by using a series of heuristic rules that examine the characteristics of each connection, the number of users, and discovery time. This information is gathered by ESET LiveGrid® technology.
Service—Name of the service, if the application is a windows service.
Remote computer—Address of the remote device. Only allow connections to trusted and known addresses.
Remote port—Communication port. Communication on common ports (e.g., web traffic – port number 80,443) can be allowed under normal circumstances.
Computer infiltrations often use the internet and hidden connections to help them infect remote systems. If rules are configured correctly, a Firewall becomes a useful tool for protection against a variety of malicious code attacks.
