Other RADIUS configurations
In the example below, we used an Active Directory domain environment.
Client Type — Client validates username and password
If you set Client Type to Client validates username and password when configuring a RADIUS client in ESA Web Console, then the first factor (username and password) is validated by the other PAM module:
When configuring RADIUS in this manner, add the following line in /etc/pam.d/sshd (or the appropriate integration):
auth required /usr/lib/pam/pam_radius_auth.so force_prompt prompt=RADIUS
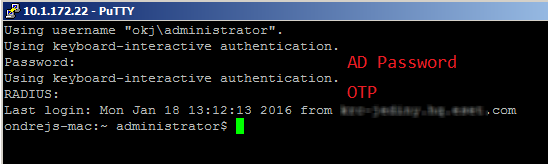
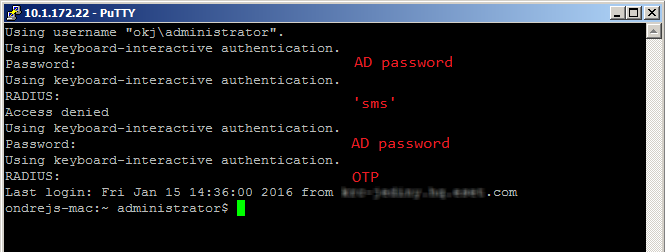
In this case, an SSH login process would look like this:
•Prompts that start with the string Password: are handled by other PAM modules. Prompts that begin with the string RADIUS: are handled by our PAM module. See the argument 'prompt=RADIUS' in the sample code above
•SMS—a user must type their AD password at the first prompt. They must type the text 'sms' (without apostrophes) at the second prompt. At the third prompt, they must type their AD password. At the fourth prompt, they must type the received OTP
•If you are using another type of OTP (OTP received via mobile app or a hard token), type the AD password on the first attempt and the OTP on the second attempt.