SMS-based OTPs
This scenario occurs if the user is configured to use only SMS-Based OTPs and the RADIUS client is configured to use SMS-based OTP authentication.
In this configuration, a user logs in with their Active Directory password. The first authentication attempt by the VPN client will fail to authenticate and the user will be prompted to type their password again. At the same time, the user will receive an SMS with their OTP. The user then logs in with the OTP contained in the SMS. The second authentication attempt will grant access if the OTP is correct.
This sequence is depicted in figure: RADIUS SMS OTP Authentication.
Supported authentication protocols: PAP, MSCHAPv2.
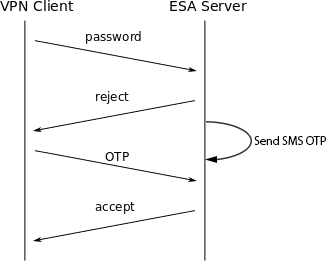
RADIUS SMS OTP Authentication