Antispam advanced settings
Configure these settings for message verification by external servers (defined as RBL - Realtime Blackhole List and DNSBL - DNS Blocklist) according to their predetermined criteria. RBL servers get queried with IP addresses extracted from Received: headers and DNSBL servers get queried with IP addresses and domains extracted from the message body.
For details explanation, see articles about RBL and DNSBL.
Maximum number of verified addresses from Received: headers
You can limit the number of IP addresses that are checked by Antispam. This concerns the IP addresses written in Received: from headers. The default value is 0, which means that only the last identified sender's IP address is checked.
Verify sender's address against end-user blacklist
Email messages that are not sent from mail servers (computers that are not listed as mail servers) are verified to make sure the sender is not on the blacklist. This option is enabled by default. You can disable it if required, but messages not sent from mail servers will not be checked against the blacklist.
Results of external third-party Blocklists have priority over end-user blacklist for IP addresses in Received: from headers. All IP addresses (up to the specified maximum number of verified addresses) are sent for evaluation by external third-party servers. |
Additional RBL servers
Is a list of Realtime Blackhole List (RBL) servers which are queried when analyzing messages.
When adding Additional RBL servers, enter the server's domain name (for example. sbl.spamhaus.org). It will work with any return codes that are supported by the server. |
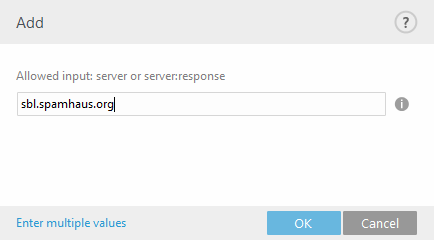
Alternatively, you can specify a server name with a return code in the format server:response (for example. zen.spamhaus.org:127.0.0.4). When using this format, we recommend that you add each server name and return code separately, so that you will have a complete list. Click Enter multiple values in the Add window to specify all server names with their return codes. Entries should look like the example below, your actual RBL server host names and return codes may vary:
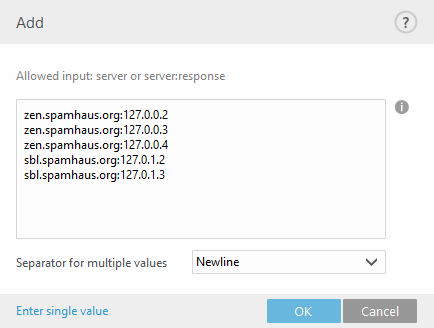
You can also import your custom list from a file instead of adding every single entry manually, click Import and browse for your file that contains entries you want to add to the list. Likewise, if you need to export your existing list to a file, select Export from the context menu.
RBL query execution limit (in seconds)
This option allows you to set a maximum time for RBL queries. RBL responses are only used from those RBL servers which respond in time. If the value is set to "0" no timeout is enforced.
Maximum number of verified addresses against RBL
This option allows you to limit how many IP addresses are queried against the RBL server. Note that the total number of RBL queries will be the number of IP addresses in the Received: headers (up to a maximum of RBL maxcheck IP addresses) multiplied by the number of RBL servers specified in RBL list. If the value is set to "0" an unlimited number of received headers are checked. Note that IPs on the ignored IP list do not count toward the RBL IP address limit.
Additional DNSBL servers
Is a list of DNS Blocklist (DNSBL) servers which are queried with domains and IP addresses extracted from the message body.
When adding Additional DNSBL servers, enter the server's domain name (for example, dbl.spamhaus.org). It will work with any return codes that are supported by the server. |
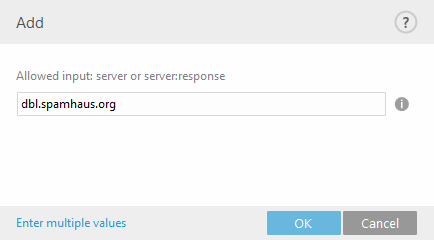
Alternatively, you can specify a server name with a return code in a form of server:response (for example, zen.spamhaus.org:127.0.0.4). In this case we recommend that you add each server name and return code separately, so that you have a complete list. Click Enter multiple values in the Add window to specify all server names with their return codes. Entries should look like the example below, your actual DNSBL server host names and return codes may vary:
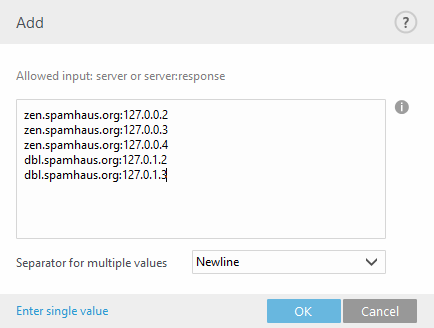
DNSBL query execution limit (in seconds)
Enable you to set a maximum timeout for all DNSBL queries to complete.
Maximum number of verified addresses against DNSBL
Enable you to limit how many IP addresses are queried against the DNS Blocklist server.
Maximum number of verified domains against DNSBL
Enable you to limit how many domains are queried against the DNS Blocklist server.
Maximum message scan size (kB)
Limits Antispam scan for messages larger than the specified value. Default value 0 means unlimited message size scan. Normally, there is no reason to limit Antispam scan, but if you need to set a limit in certain situations, change the value to required size. When set, Antispam engine will process messages up to the specified size and ignore larger messages.
The smallest possible limit is 12 kB. If you set the value from 1 to 12, Antispam engine will always read at least 12 kB. |
Enable temporary rejecting of undetermined messages
If the Antispam engine is not able to determine whether the message is or is not SPAM, which means the message has some suspicious SPAM characteristics but not enough to be marked as SPAM (for example the first email of a campaign, or an email originating from an IP range with mixed ratings), then this setting (when enabled) allows ESET Mail Security to temporarily reject the message - the same way Greylisting does - and keep rejecting it for a specific time period, until:
•The interval has elapsed and the message is accepted upon the next delivery attempt. This message is left with the initial classification (SPAM or HAM).
•Antispam cloud gathers enough data and is able to properly classify the message before the interval elapses.
The rejected message is not kept by ESET Mail Security as it must be re-sent by the sending mail server in accordance with the SMTP RFC.
Enable submitting of temporary rejected messages for analysis
The message content is automatically sent for further analysis. This helps improve message classification of future email messages.
It is possible that temporarily rejected messages which are sent for analysis could in fact be HAM. In rare cases, temporarily rejected messages may be used for manual evaluation. Enable this feature only if there are no risks of leaking any potentially sensitive data. |