Scan
The On-demand scanner is an important part of ESET Mail Security. It is used to perform scans of files and folders on your computer. To ensure the security of your network, it is essential that computer scans are not just run when an infection is suspected but regularly as part of routine security measures.
We recommend that you perform regular (for example, once a month) in-depth scans of your system to detect viruses not detected by Real-time file system protection. This can occur if a threat is introduced when Real-time file system protection is disabled, the detection engine has not been updated, or if a file was not detected when it was first saved to the disk.
Select available On-demand scans for ESET Mail Security:
Mailbox database scan
Lets you run On-demand database scan. You can choose Public folders, Mail Servers and Mailboxes to scan. Also, you can use Scheduler to run the database scan at a specific time or at an event.
If you are running Microsoft Exchange Server 2007, 2010, 2013 or 2016 you can choose between Mailbox database protection and On-demand database scan, only one protection type can be active at a time. If you decide to use On-demand database scan you will need to disable integration of Mailbox database protection in Advanced setup under Server. Otherwise On-demand database scan will not be available. |
Microsoft 365 mailbox scan
Enables you to scan remote mailboxes in Microsoft 365 hybrid environments.
Storage scan
Scans all shared folders on the local server. If Storage scan is not available, there are no shared folders on your server.
Scan your computer
Allows you to quickly launch a computer scan and clean infected files with no need for user intervention. The advantage of Scan your computer is that it is easy to operate and does not require detailed scanning configuration. Scan checks all files on local drives and automatically cleans or deletes detected infiltrations. The cleaning level is automatically set to the default value. For more detailed information on types of cleaning, see Cleaning.
We recommend that you run a computer scan at least once a month. Scanning can be configured as a scheduled task. |
Custom scan is an optimal solution if you want to specify scanning parameters such as scan targets and scanning methods. The advantage of Custom scan is the ability to configure scan parameters in detail. Configurations can be saved to user-defined scan profiles, which can be useful if scanning is repeatedly performed using the same parameters.
Removable media scan
Similar to Smart scan - quickly launch a scan of removable media (such as CD/DVD/USB) that are connected to the computer. This may be useful when you connect a USB flash drive to a computer and want to scan its content for malware and other potential threats. This type of scan can also be initiated by clicking Custom scan and then selecting Removable media from the Scan targets drop-down menu and clicking Scan.
This option is only visible in the menu if Hyper-V Manager is installed on the server that runs ESET Mail Security. Hyper-V scan allows for scanning of Virtual Machine (VM) disks on Microsoft Hyper-V Server without the need to have any "Agent" installed on the specific VM.
Repeat last scan
Repeats your last scan operation using exactly the same settings.
Repeat last scan function is not available if On-demand database scan is present. |
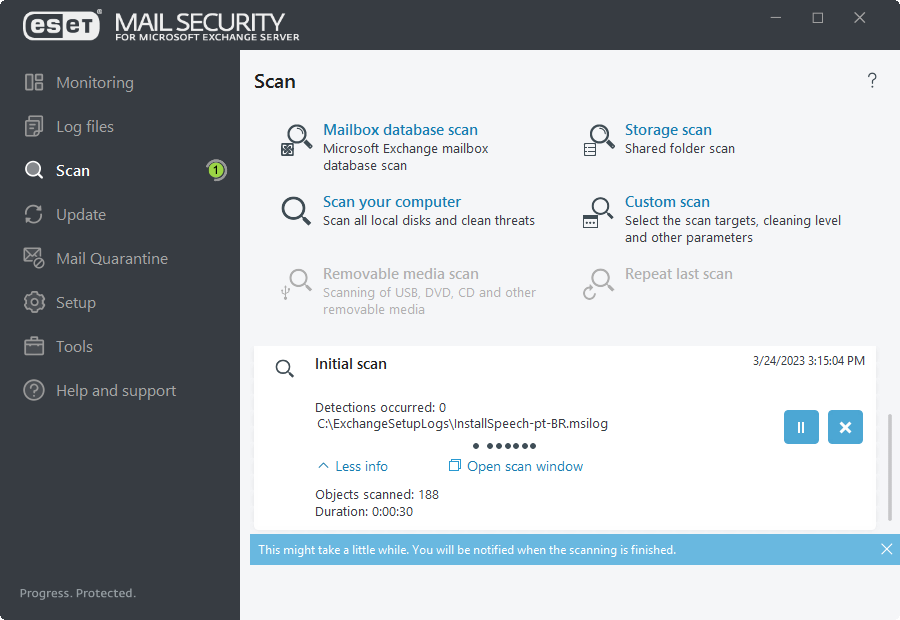
You can use options and shows more information about the scan statuses:
Drag and drop files |
You can also drag and drop files into the ESET Mail Security scan window. These files will be virus scanned immediately. |
|---|---|
Dismiss/ Dismiss all |
Dismissing of give messages. |
Scan statuses |
Show the status of initial scan. This scan has finished completed or has been interrupted by user. |
Shows more detailed information. |
|
More info |
During a scan to see details such as the User who executed the scan, number of Objects scanned and the scan Duration. If On-demand Database scan is running, it shows the user who executed the scan, not the actual Database scan account that is being used to connect to EWS (Exchange Web Services) during the scan process. |
The scan progress window shows the current status of the scan and information about the number of files found that contain malicious code. |