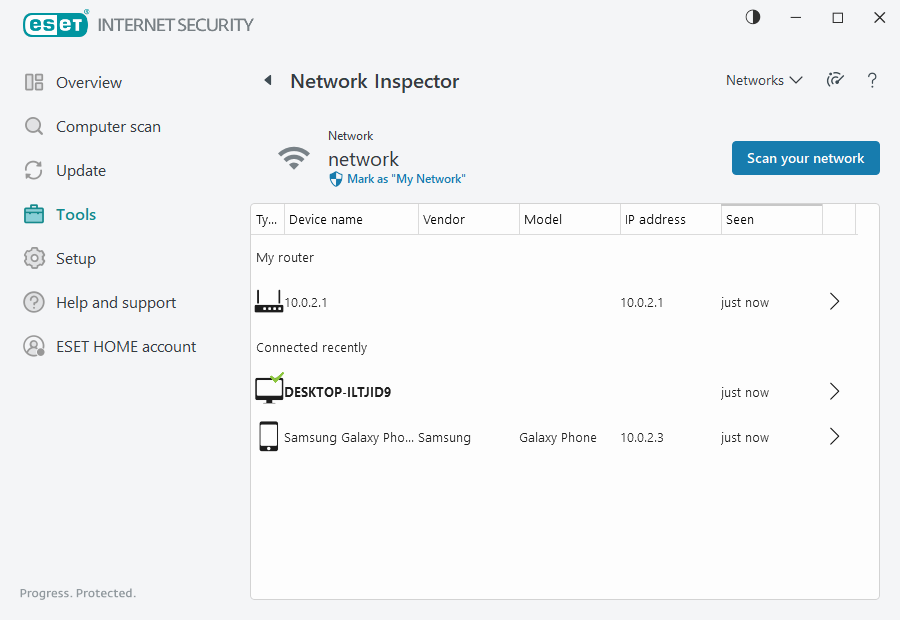
Network Inspector
Network Inspector can help identify vulnerabilities in your trusted (home or office) network (for example, open ports or a weak router password). It also provides a list of connected devices, categorized by device type (for example, printer, router, mobile device, etc.) to show you what is connected to your network (for example, game console, IoT, or other smart home devices).
Network Inspector helps you identify a router's vulnerabilities and increases your level of protection when connected to a network.
Network Inspector does not reconfigure your router for you. You will make the changes yourself using your router's specialized interface. Home routers can be highly vulnerable to malware used to launch distributed denial-of-service attacks (DDoS). If the router password has not been changed from the default by the user, it is easy for hackers to guess and then log in to your router and reconfigure it or compromise your network.
We strongly recommend creating a strong password that is long enough and includes numbers, symbols, or capital letters. To make the password harder to crack, use a mix of different types of characters. |
If the network you are connected to is configured as trusted, you can mark the network as "My Network". Click Mark as "My Network" to add a My Network tag to the network. This tag will be shown next to the network throughout the ESET Internet Security for better identification and security overview. Click Unmark as "My Network" to remove the tag.
Each device that is connected to your network is displayed with basic information in a list view. Click the specific device to edit the device or view detailed information about the device.
In the list view, the Networks drop-down menu enables you to filter devices based on the following criteria:
•Devices connected to a specific network
•Devices connected to All networks
•Uncategorized devices
Click the device icon to edit the device or view detailed information about the device. Recently connected devices are shown closer to the router so that you can easily spot them.
Click the gear wheel ![]() in the upper right corner to select whether to notify when a new device is discovered in the network.
in the upper right corner to select whether to notify when a new device is discovered in the network.
Click Scan your network to manually perform a scan of the network you are currently connected to. Scan your network is available only for a trusted network. See Network connection profiles to review or edit your network settings.
You can choose from the following scanning options:
•Scan everything
•Scan router only
•Scan devices only
Perform network scans on trusted network only! If you do this on untrusted networks, be aware of potential danger. |
When the scan is complete, a notification with a link to basic information about the device will be shown, or you can double-click the suspicious device in the list or sonar view. Click Troubleshoot to see recently blocked communications. More information about Firewall troubleshooting.
There are two types of notifications displayed by the Network Inspector module:
•New device connected to the network—displayed if a previously unseen device connects to the network while the user is connected.
•New network device found—displayed if you reconnect to your trusted network and a previously unseen device is now present.
Both notification types inform you if an unauthorized device is trying to connect to your network. Click View device details to show the details. |
What do the icons on the devices in Network Inspector mean?
|
The yellow star icon indicates devices that are new to the network or detected by ESET for the first time. |
|
The yellow caution icon indicates that your router may contain vulnerabilities. Click the icon in your product for more detailed information about the issue. |
|
The red warning icon indicates that your router contains vulnerabilities and may be infected. Click the icon in your product for more detailed information about the issue. |
|
The blue icon may appear when your ESET product has additional information for your router but does not require immediate attention because there are no security risks present. Click the icon in your product for more detailed information. |