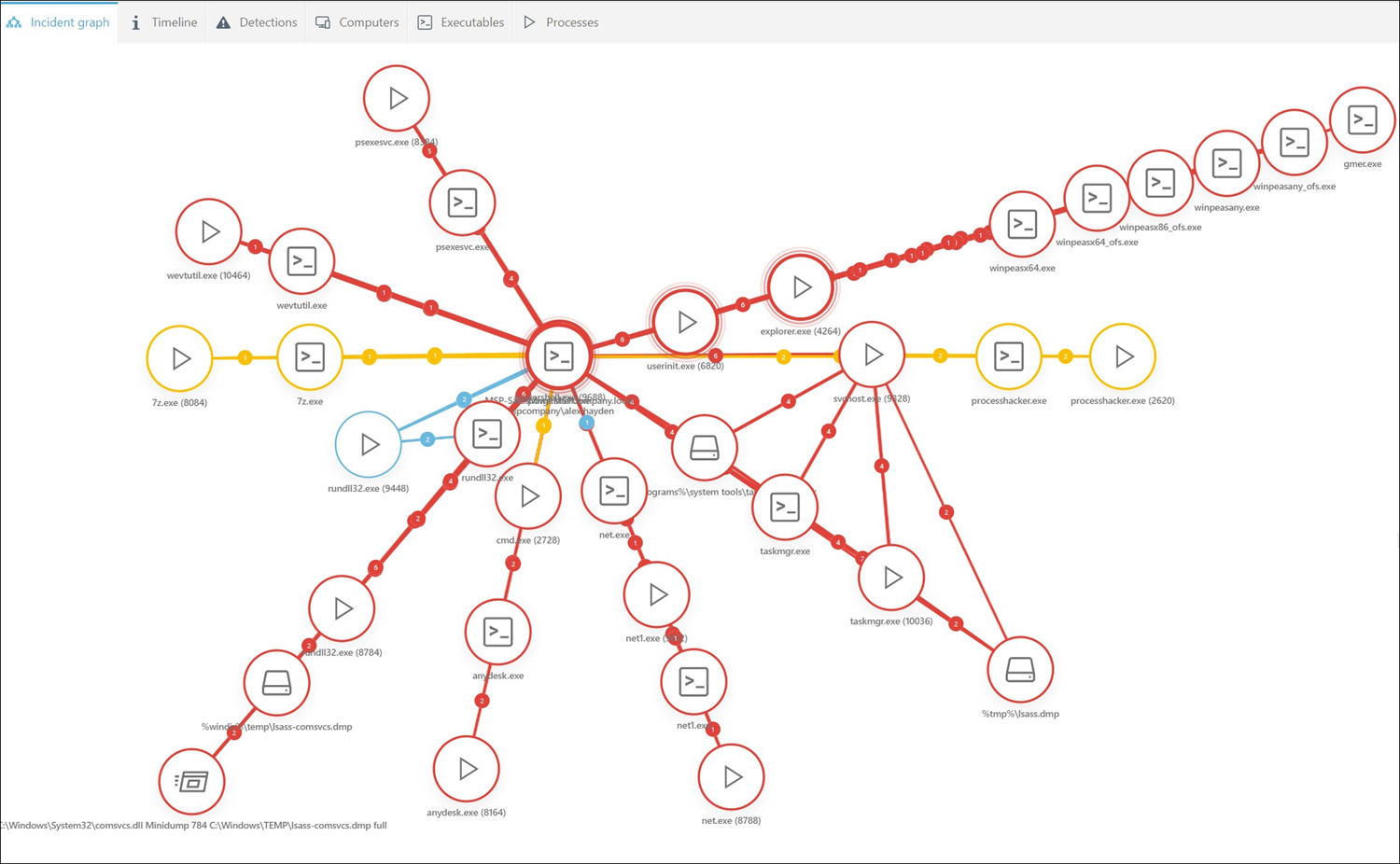
Incident Graph example
In this example, we will explain one incident in the Incident Graph:
In the example graph, you can see:
1.User alex.hayden executed trusted utilities (whoami.exe, net.exe, net1.exe) from PowerShell. Which indicates that this action intends to gather information about the system users and domain-level groups.
2.Multiple malicious files (winpeasx64.exe, winpeasany.exe, winpeasany_ofs.exe, gmer.exe, winpeasx86_ofs.exe, winpeasx64_ofs.exe) were accessed by Windows File Explorer (explorer.exe).
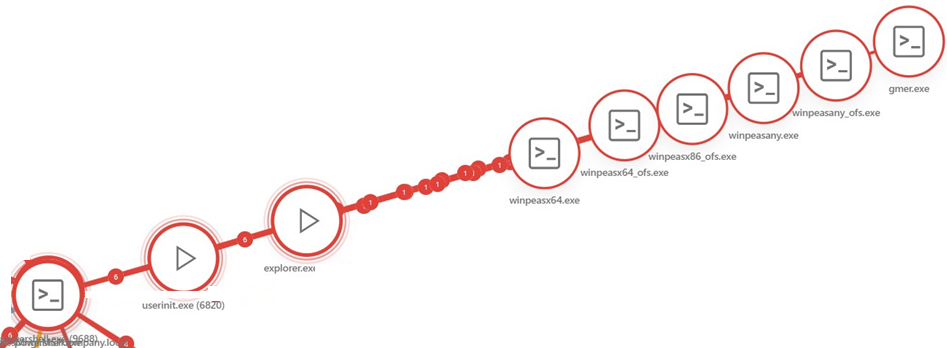
3.Actions in step 2 led to the detection of MSIL/HackTool.Agent.OS.
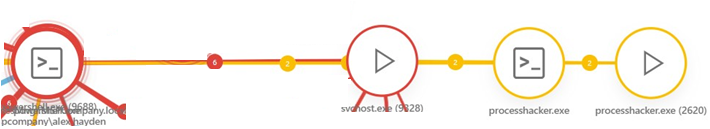
4.Execution of processhacker.exe and kprocesshacker.sys indicated an attempt to disable security software and gain kernel-level privileges.
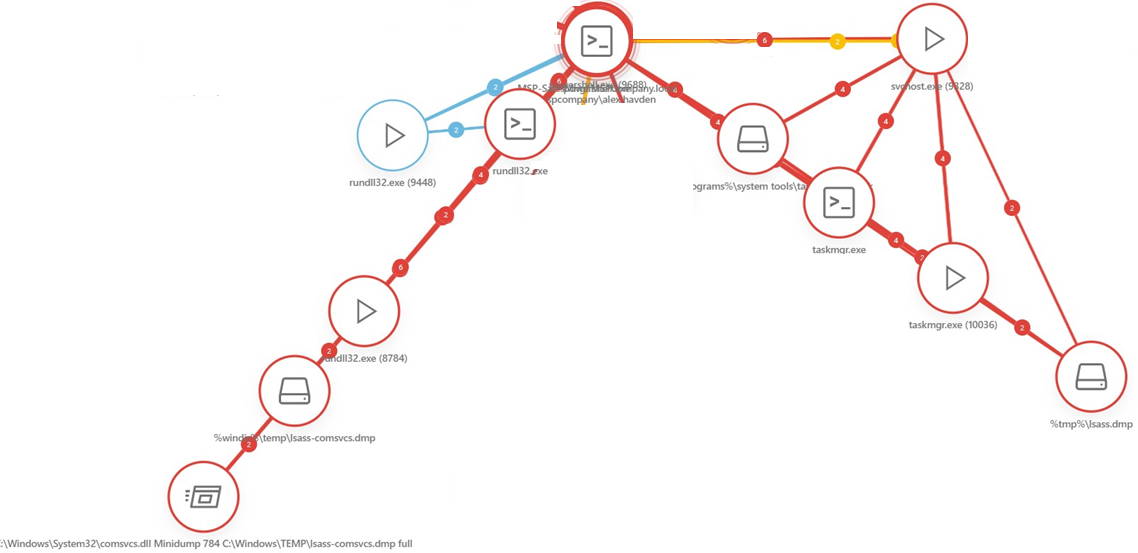
5.Task Manager (taskmgr.exe) and rundll32.exe were used to access the LSASS process (lsass.dmp) and create minidump files with a potential for credential dumping.
6.Trusted utilities (net1.exe and reg.exe) were used to add and hide a user account and modify registry items.
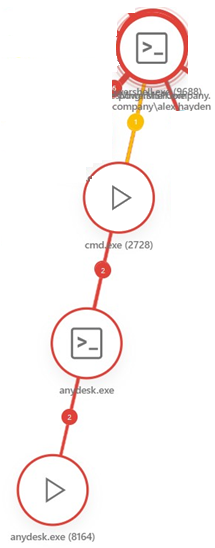
7.AnyDesk (anydesk.exe) remote desktop software was silently installed and configured to start on boot. This was consistent with Conti ransomware gang settings.
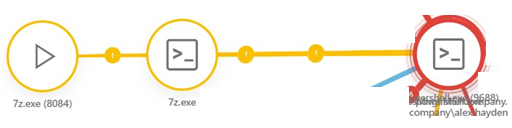
8.7-Zip utility (7z.exe) was used to create a password-protected archive file. This action possibly indicates a suspicious collection or filecoder activity.
9.wevtutil.exe was used to clear the application event log. This action potentially indicates an attempt to remove evidence of malicious activity.