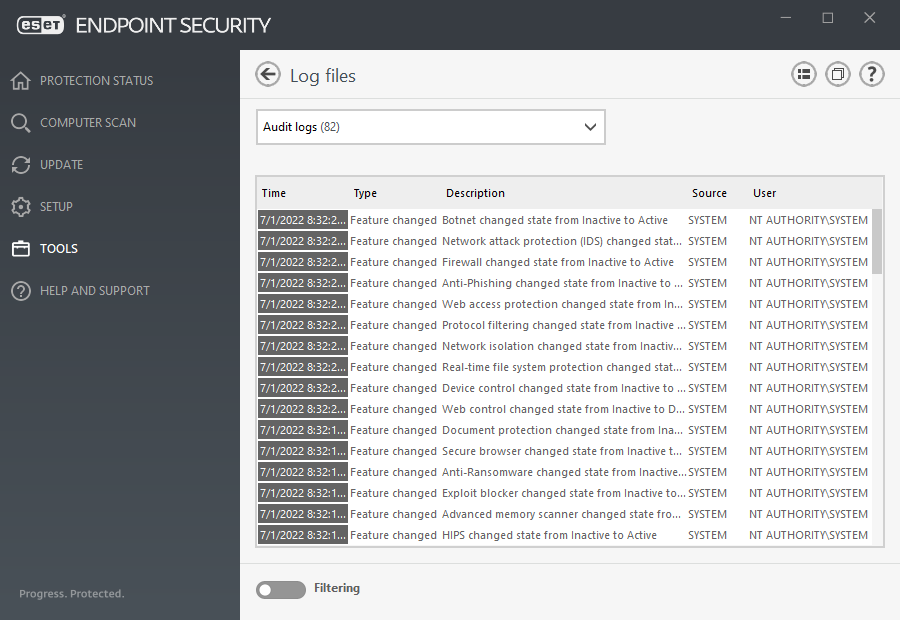
Audit logs
In an enterprise environment there are usually multiple users with access rights defined for configuring endpoints. Since the modification of the product configuration might dramatically affect how the product operates it is essential that administrators would like to trace the changes done by users to help administrators quickly identify, resolve, and also to prevent occurring of the same or similar problems in the future.
The Audit log is a new type of logging from ESET Endpoint Security version 7.1 and solution for the identification of the origin of the problem. Audit log tracks changes in configuration or protection state and records snapshots for later reference.
To see the Audit log, click Tools in the main menu and then click Log files and select Audit logs from the drop-down menu.
The Audit log contains information about:
- Time - when the change was performed
- Type - what type of setting or feature was changed
- Description - what exactly was changed and which part of setting has been changed together with number of changed settings
- Source - where is the source of the change
- User - who made the change
Right-click any Settings changed type of audit log in the Log files window and select Show changes from the context menu to display detailed information about the performed change. Besides, you can restore setting change by clicking Restore from the context menu (not available for product managed by ESET PROTECT). If you select Delete all from the context menu, the log with information about this action will be created.
If Optimize log files automatically enabled in Advanced setup > Tools > Log files, the Audit logs will automatically be defragmented as other logs.
if Automatically delete records older than (days) enabled in Advanced setup > Tools > Log files, log entries older than the specified number of days will automatically be deleted.
