Known networks editor
Known networks can be configured manually in Advanced setup > Network protection > Firewall > Known Networks by clicking Edit next to Known networks.
Columns
Name – Name of known network.
Protection type – Shows if the network is set to Home or office network, Public or Use Windows setting.
Firewall profile – Select a profile from the Display rules used in the profile drop-down menu to display the profiles rules filter.
Update profile – Allows you to apply created update profile when connected to this network.
Control elements
Add – Creates a new known network.
Edit – Click to edit an existing known network.
Delete – Select a network and click Delete to remove it from the list of known networks.
![]() Top/Up/Down/Bottom – Allows you to adjust the priority level of known networks (networks are evaluated from top to bottom).
Top/Up/Down/Bottom – Allows you to adjust the priority level of known networks (networks are evaluated from top to bottom).
Network configuration settings are arranged in the following tabs:
Network
Here you can define the Network name and select the Protection type (Public network, Home or office network or Use Windows setting) for the network. Use the Firewall profile drop-down menu to select the profile for this network. If the network uses the Home or office network protection type, all directly connected network subnets are considered trusted. For example, if a network adapter is connected to this network with the IP address 192.168.1.5 and the subnet mask 255.255.255.0, the subnet 192.168.1.0/24 is added to that adapter's trusted zone. If the adapter has more addresses/subnets, all of them will be trusted, regardless of the Network Identification configuration of the known network.
Additionally, addresses added under Additional trusted addresses are always added to the trusted zone of adapters connected to this network (regardless of the network's protection type).
Warn about weak WiFi encryption – ESET Endpoint Security will inform you when you connect to an unprotected wireless network or network with weak protection.
Firewall profile – Select firewall profile that will be used when connected to this network.
Update profile – Select update profile that will be used when connected to this network.
The following conditions must be met for a network to be marked as connected in the list of connected networks:
•Network identification – All filled in parameters must match active connection parameters.
•Network authentication – if authentication server is selected, successful authentication with the ESET Authentication Server must take place.
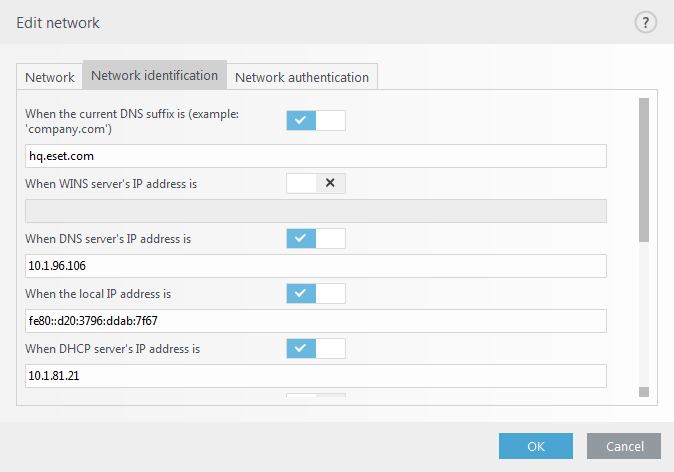
Network identification
Network identification is performed based on the local network adapter's parameters. All selected parameters are compared against the actual parameters of active network connections. IPv4 and IPv6 addresses are allowed.
Network authentication
Network authentication searches for a specific server in the network and uses asymmetric encryption (RSA) to authenticate that server. The name of the network being authenticated must match the zone name set in authentication server settings. The name is case sensitive. Specify a server name, server listening port and a public key that corresponds to the private server key (see Network authentication – Server configuration). The server name can be entered in the form of an IP address, DNS or NetBios name and can be followed by a path specifying the location of the key on the server (for example, server_name_/directory1/directory2/authentication). You can specify alternate servers to use by appending them to the path, separated by semicolons.
Download the ESET Authentication Server.
The public key can be imported using any of the following file types:
•PEM encrypted public key (.pem), this key can be generated using the ESET Authentication Server (see Network authentication – Server configuration).
•Encrypted public key
•Public key certificate (.crt)
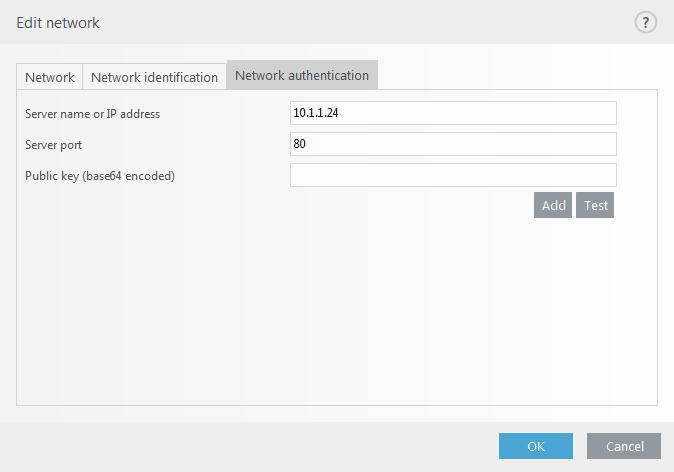
Click Test to test your settings. If authentication is successful, Server authentication was successful will be displayed. If authentication is not configured properly, one of the following error messages will be displayed:
Server authentication failed. Invalid or mismatched signature.
Server signature does not match the public key entered.
Server authentication failed. Network name doesn't match.
The configured network name does not correspond with the authentication server zone name. Review both names and ensure they are identical.
Server authentication failed. Invalid or no response from server.
No response is received if the server is not running or is inaccessible. An invalid response may be received if another HTTP server is running on the specified address.
Invalid public key entered.
Verify that the public key file you have entered is not corrupted.
