Firewall
The Firewall controls all network traffic to and from the system. This is accomplished by allowing or denying individual network connections based on specified filtering rules. It provides protection against attacks from remote computers and can block potentially threatening services.
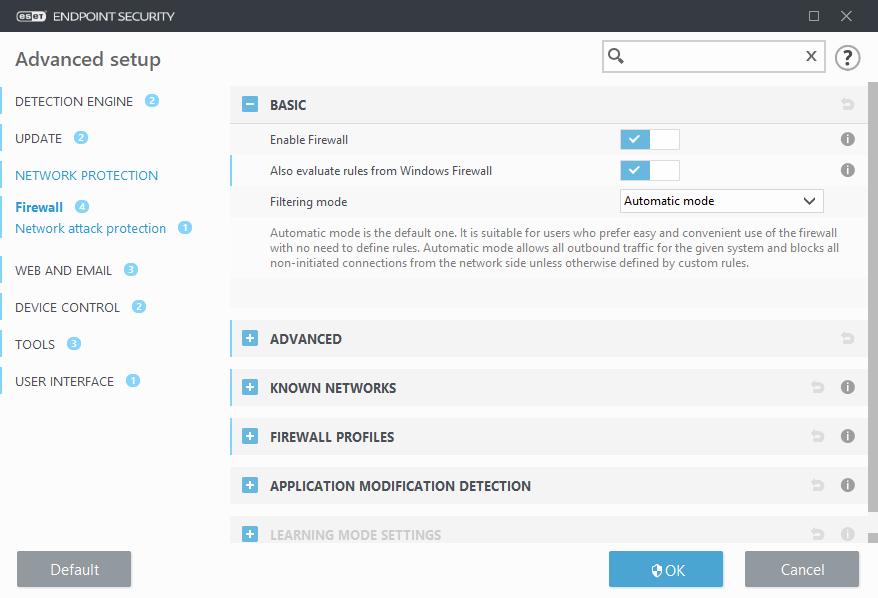
 Basic
Basic
Enable Firewall
We recommend that you leave this feature enabled to ensure the security of your system. With the firewall engaged, network traffic is scanned in both directions.
Also evaluate rules from Windows firewall
In automatic mode, allow also incoming traffic allowed by rules from Windows Firewall, unless explicitly blocked by ESET rules.
Rules from Windows firewall configured using Group Policy (GPO) are not evaluated. |
Filtering mode
The behavior of the firewall changes based on the filtering mode. Filtering modes also influence the level of user interaction required.
The following filtering modes are available for the ESET Endpoint Security Firewall:
Filtering mode |
Description |
|---|---|
Automatic mode |
The default mode. This mode is suitable for users who prefer easy and convenient use of the firewall without the need to define rules. Custom, user-defined rules can be created but are not required in Automatic mode. Automatic mode allows all outbound traffic for a given system and blocks most inbound traffic with the exception of some traffic from the Trusted Zone (as specified in IDS and advanced options/Allowed services) and responses to recent outbound communications. |
Interactive mode |
Allows you to build a custom configuration for your Firewall. When a communication is detected and no existing rules apply to that communication, a dialog window reporting an unknown connection will be displayed. The dialog window gives the option to allow or deny the communication, and the decision to allow or deny can be saved as a new rule for the Firewall. If you choose to create a new rule, all future connections of this type will be allowed or blocked according to that rule. |
Policy-based mode |
Blocks all connections that are not defined by a specific rule that allows them. This mode allows advanced users to define rules that permit only desired and secure connections. All other unspecified connections will be blocked by the Firewall. |
Learning mode |
Automatically creates and saves rules; this mode is best used for the initial configuration of the Firewall, but should not be left on for prolonged periods of time. No user interaction is required, because ESET Endpoint Security saves rules according to predefined parameters. Learning mode should only be used until all rules for required communications have been created to avoid security risks. |
Profiles can be used to customize the behavior of the ESET Endpoint Security Firewall by specifying different sets of rules in different situations.
 Advanced
Advanced
Rules
Rules setup allows you to view all rules applied to traffic generated by individual applications within trusted zones and the Internet.
Zones
A zone represents a collection of network addresses that create one logical group.
You can create an IDS rule when a Botnet attacks your computer. An exception can be modified in Advanced setup (F5) > Network protection > Network attack protection > IDS rules by clicking Edit. |
