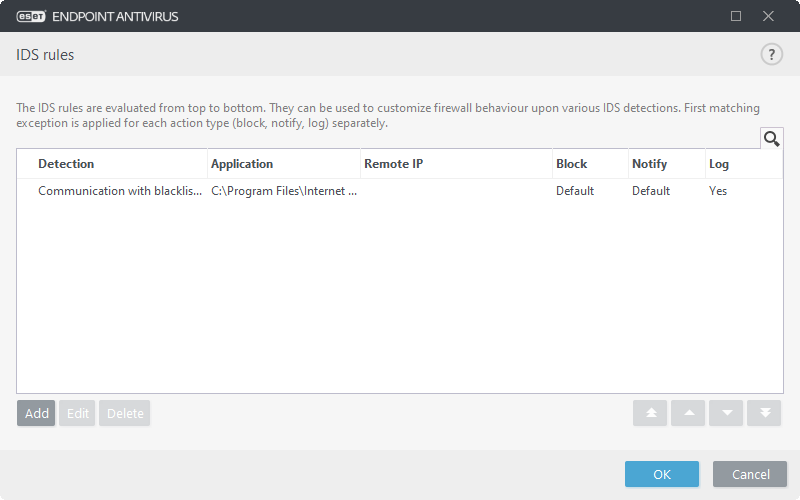
IDS rules
In some situations the Intrusion Detection Service (IDS) may detect communication between routers or other internal networking devices as a potential attack. For example, you can add the known safe address to the Addresses excluded from IDS zone to bypass the IDS.
The following ESET Knowledgebase articles may only be available in English: |
Columns
- Detection – Type of detection.
- Application – Select the file path of an excepted application by clicking ... (for example C:\Program Files\Firefox\Firefox.exe). Do NOT enter the name of the application.
- Remote IP – A list of remote IPv4 or IPv6 address / ranges / subnets. Multiple addresses must be separated by a comma.
- Block – Each system process has its own default behavior and assigned action (block or allow). To override the default behavior for ESET Endpoint Antivirus you can choose to block or allow it using the drop-down menu.
- Notify – Select Yes to display Desktop notifications on your computer. Select No if you do not want desktop notifications. The available values are Default/Yes/No.
- Log – Select Yes to log events to ESET Endpoint Antivirus log files. Select No if you do not want to log events. The available values are Default/Yes/No.
Tab Exclusions will be displayed if an administrator creates IDS exclusions in ESET PROTECT Web Console. IDS exclusions can contain allowing rules only and are evaluated before IDS rules.
Managing IDS rules
- Add – Click to create a new IDS rule.
- Edit – Click to edit an existing IDS rule.
- Delete – Select and click if you want to remove an existing exception from the list of IDS rule.
 Top/Up/Down/Bottom – Allows you to adjust the priority level of rules (exceptions are evaluated from top to bottom).
Top/Up/Down/Bottom – Allows you to adjust the priority level of rules (exceptions are evaluated from top to bottom).
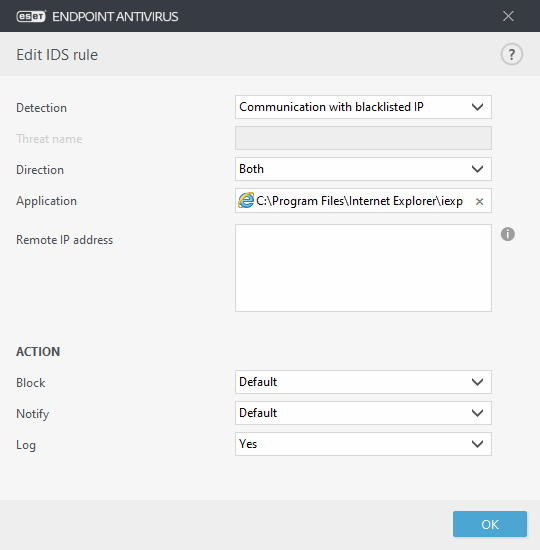
You want to display a notification and collect a log each time the event occurs:
|
You want to remove recurring notifications for a type of detection you do not consider to be a threat:
|
