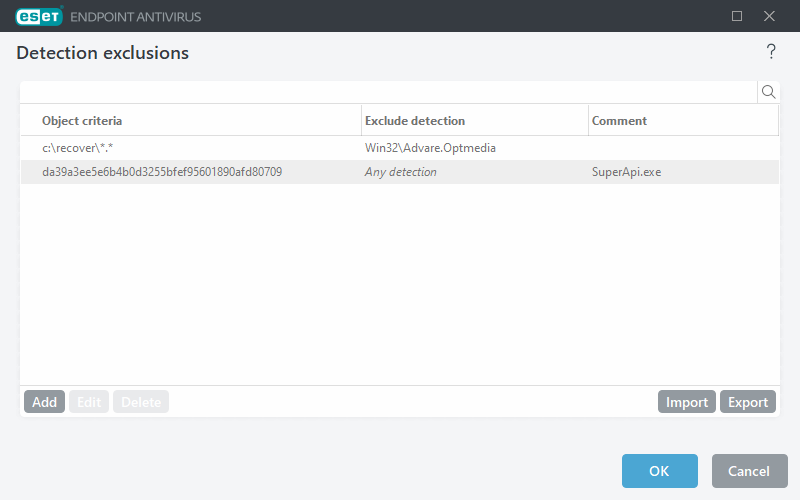
Detection exclusions
Detection exclusions enable you to exclude objects from cleaning by filtering the detection name, object path or its hash.
Detection exclusions do not exclude files and folders from scanning as Performance exclusions do. Detection exclusions exclude objects only when they are detected by the detection engine and an appropriate rule is present in the exclusion list. For example (see the first row on the image below), when an object is detected as Win32/Adware.Optmedia and the detected file is C:\Recovery\file.exe. On the second row, each file, which has the appropriate SHA-1 hash, will always be excluded despite the detection name. |
To ensure that all threats are detected, we recommend creating detection exclusions only when it is absolutely necessary.
To add files and folders to the exclusions list, open Advanced setup > Detection engine > Exclusions > Detection exclusions > Edit.
To exclude an object (by its detection name or hash) from cleaning, click Add.
For Potentially unwanted applications and Potentially unsafe applications, the exclusion by its detection name can also be created:
- In the alert window reporting the detection (click Show advanced options and then select Exclude from detection).
- From the Log Files context menu using Create detection exclusion wizard.
- By clicking Tools > Quarantine and then right-clicking the quarantined file and selecting Restore and exclude from scanning from the context menu.
Detection exclusions object criteria
- Path—Limit a detection exclusion for a specified path (or any).
- Hash—Excludes a file based on a specified SHA-1 hash, regardless of the file type, location, name, or extension.
- Detection name—If there is a name of a detection next to an excluded file, it means that the file is only excluded for the given detection, not completely. If that file becomes infected later with other malware, it will be detected. The detection name is case sensitive.
Control elements
- Add—Add a new entry to exclude objects from cleaning.
- Edit—Enables you to edit selected entries.
- Delete—Removes selected entries (CTRL + click to select multiple entries).
- Import/Export—Importing and exporting of detection exclusions is useful if you need to backup your current exclusions for use at a later time. The export settings option is also convenient for users in unmanaged environments who want to use their preferred configuration on multiple systems, they can easily import a .txt file to transfer these settings.
Display example of the import/export file format
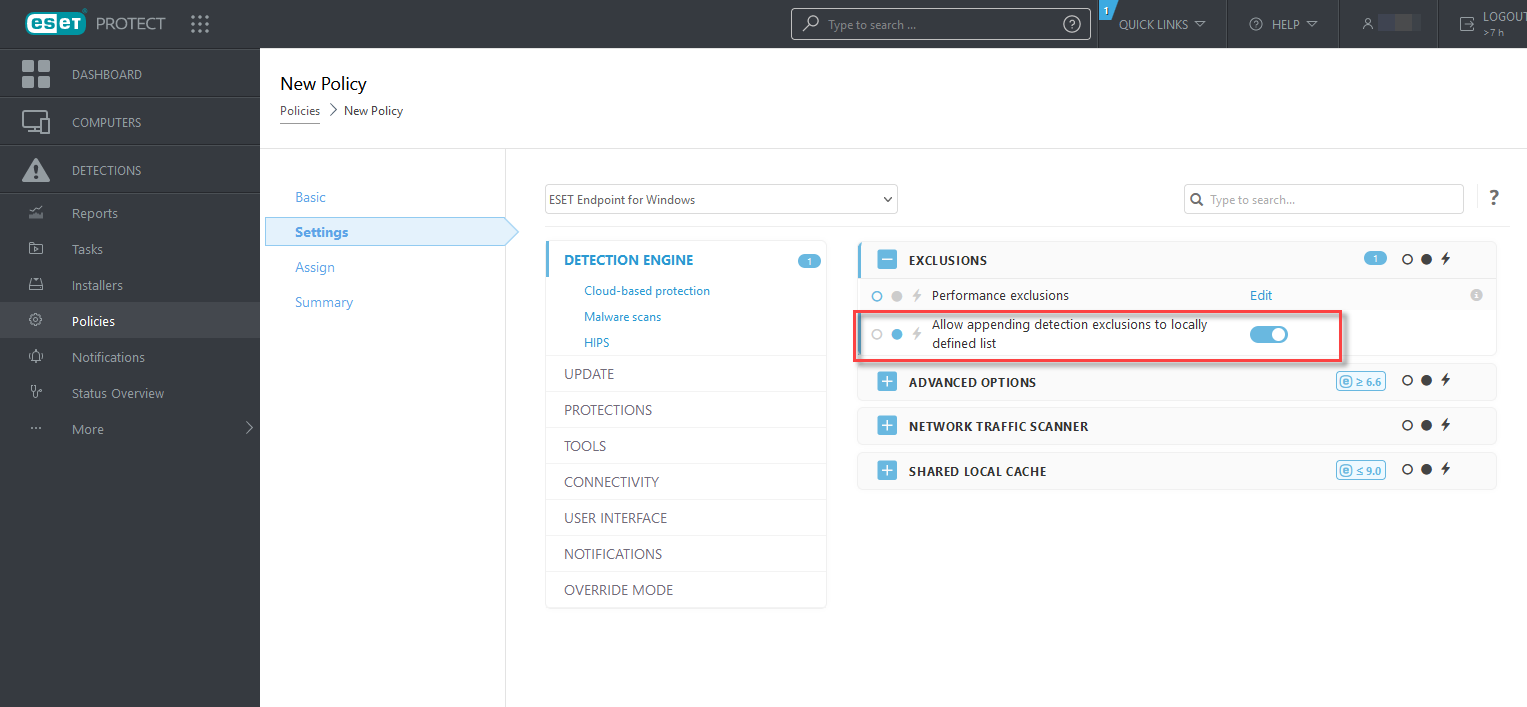
Detection exclusions setup in ESET PROTECT On-Prem
ESET PROTECT On-Prem detection exclusions management wizard—Create a detection exclusion and apply it to more computers/group(s).
Possible detection exclusions override from ESET PROTECT On-Prem
When there is an existing presence of a detection exclusions local list, the admin has to apply a policy with Allow appending detection exclusions to locally defined list. After that, appending detection exclusions from ESET PROTECT On-Prem will work as expected.