Work with ESET Endpoint Antivirus
The ESET Endpoint Antivirus setup enables you to adjust the level of protection for your computer, web and email.
When creating a policy from ESET PROTECT Web Console you can select the flag for each setting. Settings with the Force flag have priority and cannot be overwritten by a later policy (even if the later policy has a Force flag). This assures that this setting will not be changed (e.g. by user or by later policies during merging). For more information see Flags in ESET PROTECT Online Help. |
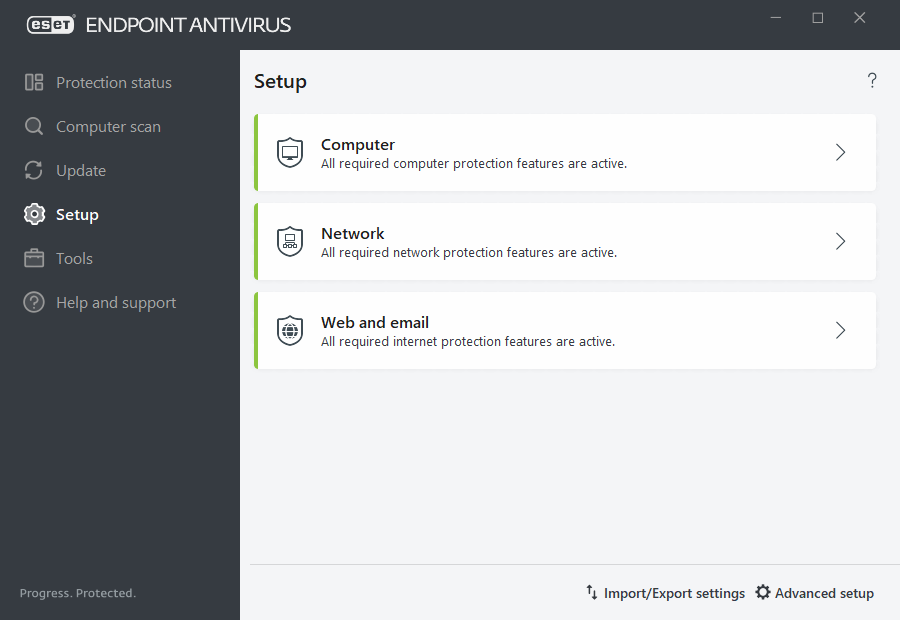
The Setup menu contains the following sections:
- Computer
- Network
- Web and Email
In the Computer section, you can enable or disable the following components:
- Real-time file system protection—All files are scanned for malicious code when they are opened, created or run.
- Device control—Provides automatic device (CD/DVD/USB/...) control. This module enables you to block or adjust extended filters/permissions and define a users ability to access and work with a given device.
- Host Intrusion Prevention System (HIPS)—The HIPS system monitors events that occur within the operating system and reacts to them according to a customized set of rules.
- Advanced memory scanner—Works in combination with Exploit Blocker to strengthen protection against malware that has been designed to evade detection by antimalware products through the use of obfuscation or encryption. Advanced memory scanner is enabled by default. Read more about this type of protection in the glossary.
- Exploit blocker—Designed to fortify commonly exploited application types such as web browsers, PDF readers, email clients and Microsoft Office components. Exploit blocker is enabled by default. Read more about this type of protection in the glossary.
- Ransomware shield—It is another layer of protection that works as a part of HIPS feature. You must have the ESET LiveGrid® reputation system enabled for Ransomware shield to work. Read more about this type of protection.
- Presentation mode—A feature for users that demand uninterrupted usage of their software, do not want to be disturbed by notifications, and want to minimize CPU usage. You will receive a warning message (potential security risk) and the main program window will turn orange after enabling Presentation mode.
The Network section enables you to configure Network attack protection (IDS) and Botnet protection.
Web and email protection setup enables you to configure the following components:
- Web access protection—If enabled, all traffic through HTTP or HTTPS is scanned for malicious software.
- Email client protection—Monitors communication received through the POP3 and IMAP protocol.
- Anti-Phishing protection—Protects you from attempts to acquire passwords, banking data and other sensitive information by illegitimate websites disguised as legitimate ones.
To temporarily disable individual modules, click the green switch ![]() next to the desired module. Note that this may decrease the protection level of your computer.
next to the desired module. Note that this may decrease the protection level of your computer.
To re-enable the protection of a disabled security component, click the red switch ![]() to return a component to its enabled state.
to return a component to its enabled state.
When ESET PROTECT policy is applied, you will see the lock icon ![]() next to a specific component. The policy applied by ESET PROTECT can be overridden locally after authentication by logged user (e.g. administrator). For more information see the ESET PROTECT Online Help.
next to a specific component. The policy applied by ESET PROTECT can be overridden locally after authentication by logged user (e.g. administrator). For more information see the ESET PROTECT Online Help.
All protective measures disabled this way will be re-enabled after a computer restart. |
To access detailed settings for a specific security component, click the gear wheel ![]() next to any component.
next to any component.
There are additional options at the bottom of the setup window. To load setup parameters using an .xml configuration file, or to save the current setup parameters to a configuration file, use Import/Export settings. See Import/Export settings for more detailed information.
For more detailed options, click Advanced Setup or press F5.
