Review list of submitted files
Create a list of top submitting computers
1.Click Reports > ESET LiveGuard.
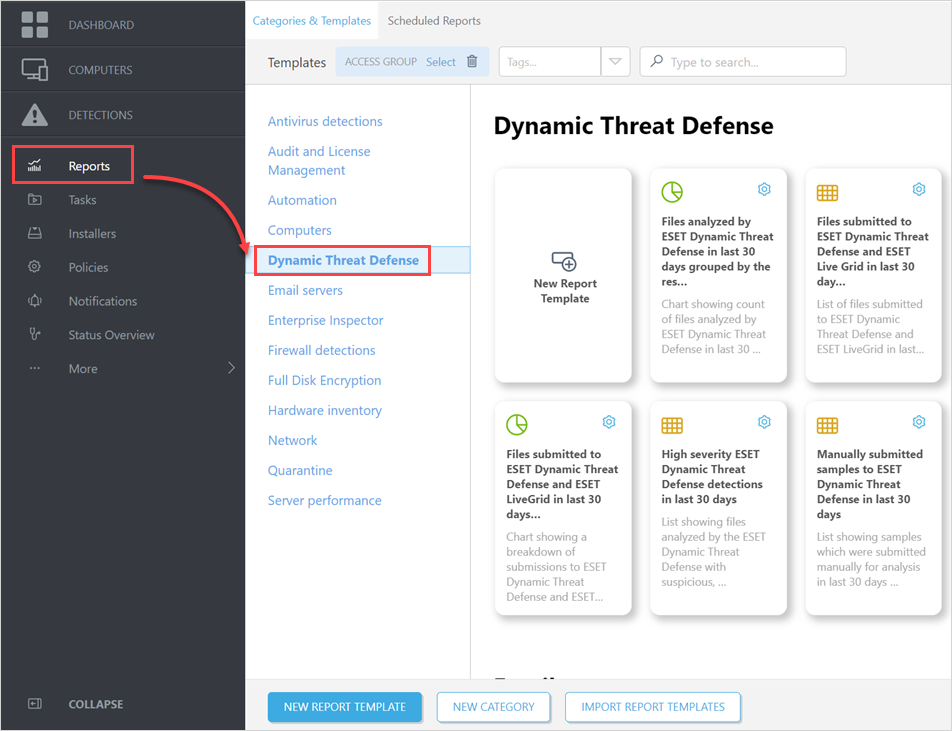
2.Find the Top 10 computers with file submissions to ESET LiveGuard and ESET LiveGrid in last 30 days report template.
You can edit the template first and change the computers count (10) or time frame (the last 30 days) to another value. You may need to change that if the situation in your network requires it. |
3.Click Generate now and save the report (the list of top computers).
Create the list of submitted files for the top computers
You need the list of top submitting computers from the procedure above to complete the following steps.
1.In the Web Console, click Reports > New Report Template.
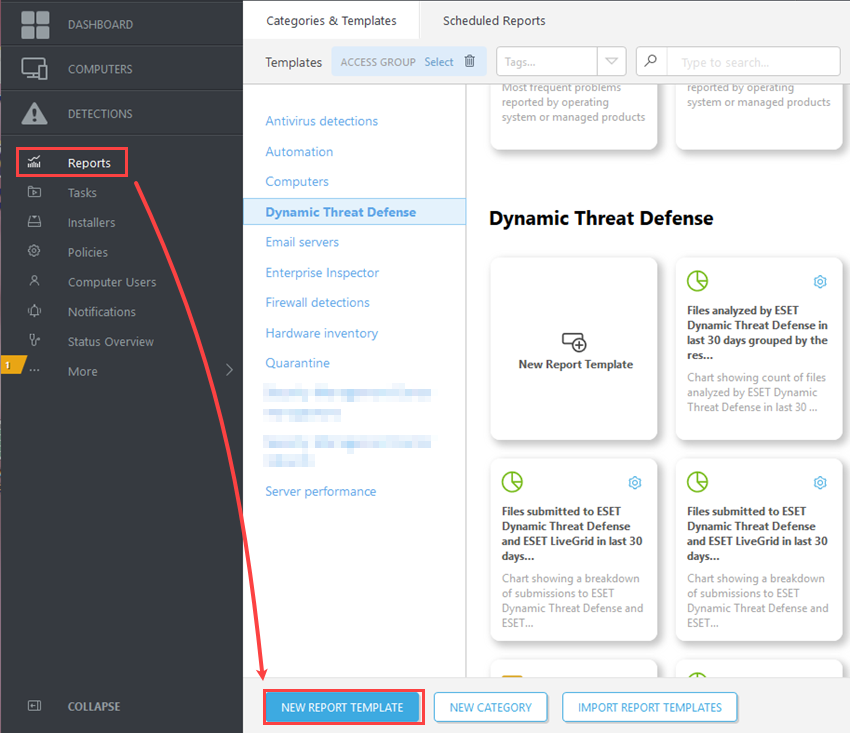
2.Give the template an appropriate Name and Category.
3.Continue to the Chart section.
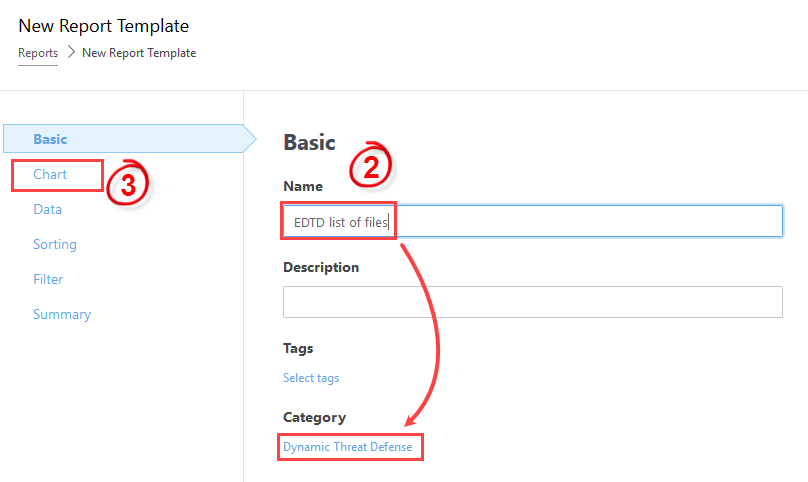
4.In the Chart section, select only the Display Table check box and continue to the Data section.
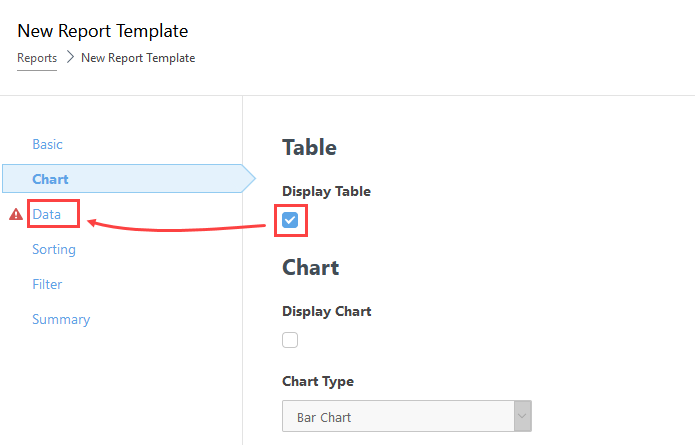
5.In the Data section, click Add Column and add the following:
Computer - Computer name
ESET LiveGuard - Object URI
6.Click Filter.
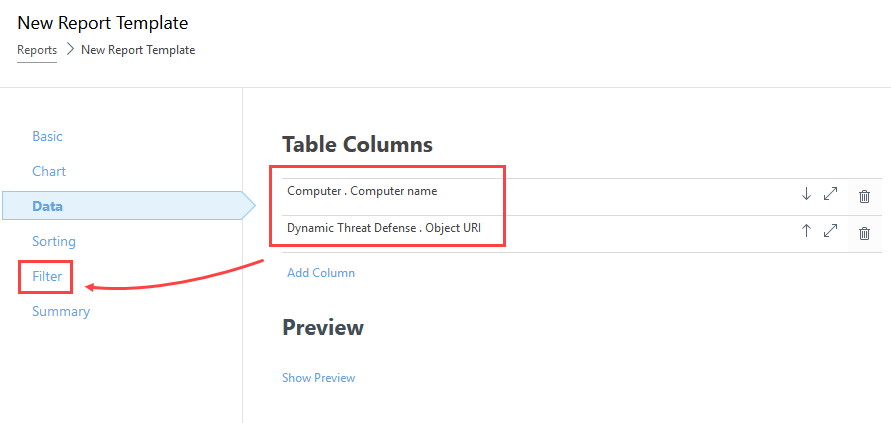
7.Click Add column, select ESET LiveGuard . Relative time interval (Time of occurrence).
8.Set the interval to the last 30 days or other values relevant to your system.
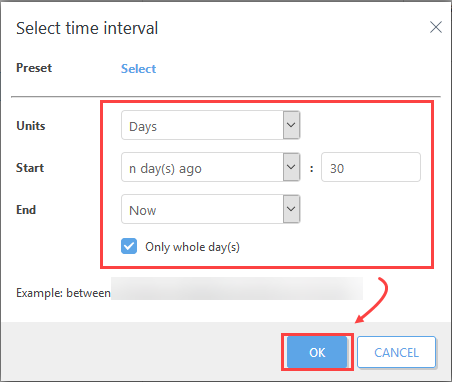
9.Click Add Column again and add Computer . Computer name item.
10. Add all the names of top computers from the previous procedure (top 10 substituting computers).
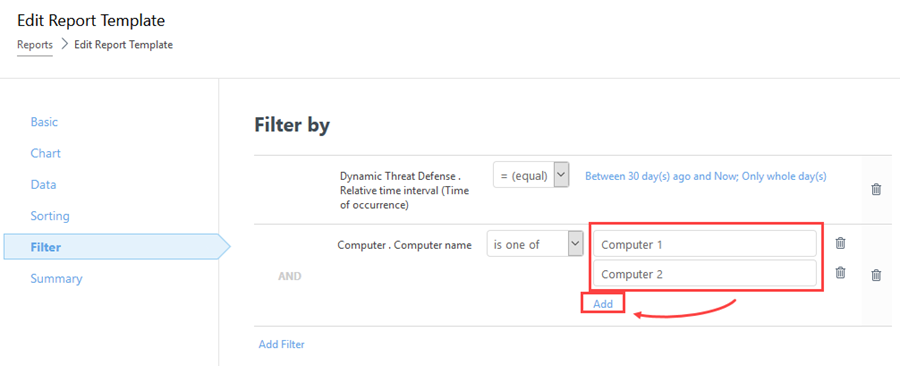
11. Click Finish to save the report template.
12. Find the new report template and generate a CSV file.
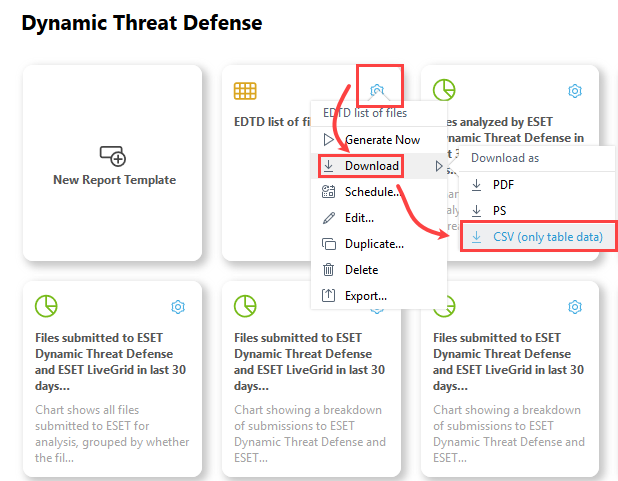
Data analysis
The following procedure requires third-party software (a spreadsheet editor and basic data analysis skills).
1.Open the CSV exported file in a spreadsheet editor, for example, Microsoft Excel.
2.Separate the data into two columns. In Microsoft Excel, select the first column, and navigate to Data > Text to Columns.
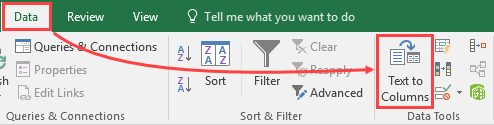
3.Select Delimited > Next.
4.Select the Semicolon delimiter and click Next > Finish.
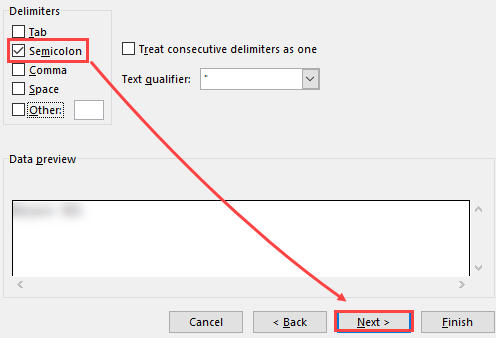
Analyze the data.
Look for a pattern in submitted files and their locations. Find a pattern, usually a folder, from which the vast majority of files is submitted. When you have a pattern, suspicious computer, or application, you need to investigate the pattern. Look for answers to the following: •Which application is using this folder? •What is this computer used for, what makes it stand out from others? •What is the origin of those files? The ultimate goal of the investigation is to find a pattern for exclusion. |
When you have found the pattern, continue with Exclude Folders.
