Extend endpoint management from ESET PROTECT to DEM plugin
To extend endpoint management from the ESET PROTECT to the ESET DEM plugin for Datto RMM create a ESET RMM enabled policy with ESET PROTECT policy creation wizard and assign it to the desired devices.
ESET PROTECT versus DEM plugin We recommend using ESET PROTECT for endpoint management, as it offers more options for detailed endpoint overview and incident analysis. If you want to extend endpoint management for specific devices to the Datto RMM platform, perform the steps below to create the ESET PROTECT ESET RMM enabled policy. |
1.Setup the ESET DEM plugin for Datto RMM.
2.Run an Onboard (Install and Activate) task to deploy a ESET security product to a desired devices.
3.In ESET PROTECT, create a policy to configure ESET RMM settings on all endpoints so that they can be managed in the ESET DEM plugin for Datto RMM.
4.In the Settings section of the policy creation wizard select ESET Endpoint for Windows from the drop-down menu.
5.Click Tools.
6.Expand section ESET RMM.
7.Click the Enable RMM toggle.
8.Next to Working mode select All operations from the drop-down menu.
9.Next to Authorization method select Application path from the drop-down menu.
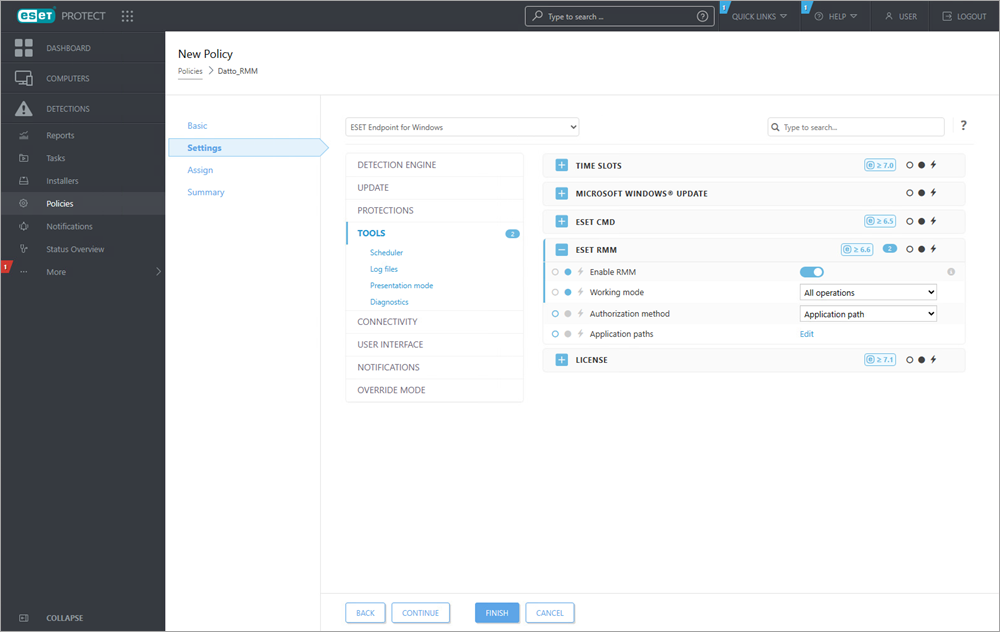
10. Next to Application paths click the Edit button.
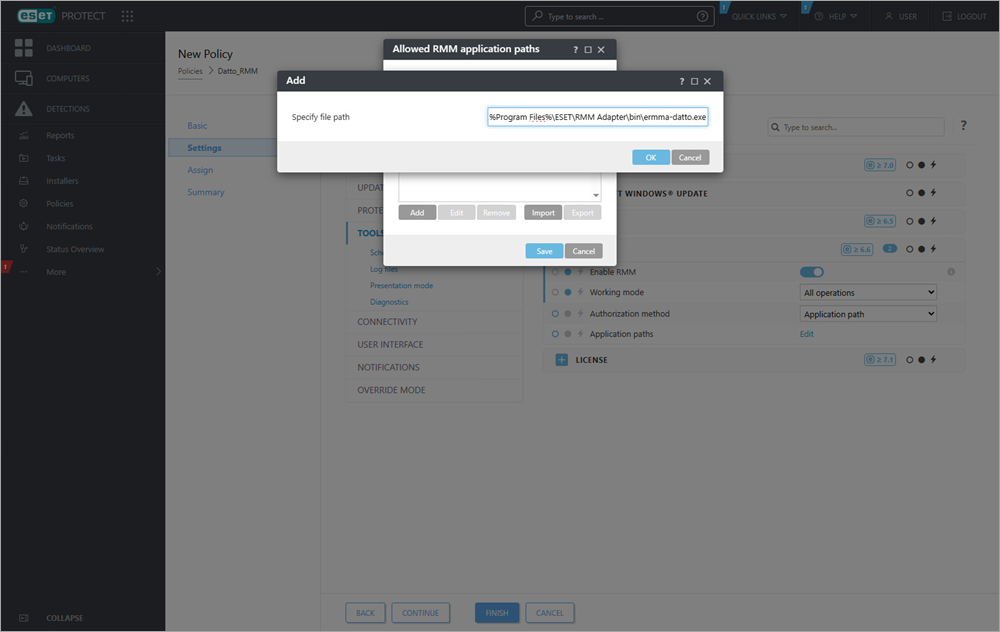
11. In the Allowed RMM application paths window, click Add.
12. Type the file path %Programfiles%\ESET\RMM Adapter\bin\ermma-datto.exe for the ESET DEM plugin for Datto RMM and click OK > Save.
File path entry If necessary, use the full path: C:\Program Files\ESET\RMM Adapter\bin\ermma-datto.exe instead of %Programfiles%\ESET\RMM Adapter\bin\ermma-datto.exe. |
13. Complete remaining steps in the ESET PROTECT New Policy creation wizard, assign the policy and apply the policy the desired endpoint computers.
14. Uninstall the ESET PROTECT Agent on all endpoint computers managed by the ESET DEM plugin for Datto RMM to prevent configuration conflicts.
